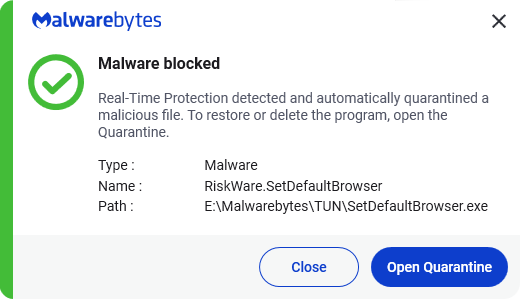
RiskWare.SetDefaultBrowser
ThreatDown is now the name of the Malwarebytes line of business products. References to Malwarebytes below reflect the amazing technology used to first identify the threat.
Short bio
RiskWare.SetDefaultBrowser is Malwarebytes’ detection name for a specific family of browser hijackers that change the user’s default browser.
Type of infection
This software is sometimes installed by system administrators to control the default browser on the endpoints under their control, but it can also be abused by others. In those cases it often comes as bundleware.
Malicious behavior
Even though RiskWare.SetDefaultBrowser can be found under variooius filenames, the original filename under Properties > Details will be SetDefaultBrowser.exe. RiskWare.SetDefaultBrowser can be used to change the default browser to Chrome, Firefox, Edge, and Internet Explorer.
Protection
Malwarebytes blocks RiskWare.SetDefaultBrowser to give users a chance to review the consequences before using it.
Home remediation
Malwarebytes can detect and remove RiskWare.SetDefaultBrowser without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.
Add an exclusion
Should users wish to keep this program and exclude it from being detected in future scans, they can add the program to the exclusions list. Here’s how to do it.
- Open Malwarebytes for Windows.
- Click the Detection History
- Click the Allow List
- To add an item to the Allow List, click Add.
- Select the exclusion type Allow a file or folder and use the Select a folder button to select the main folder for the software that you wish to keep.
- Repeat this for any secondary files or folder(s) that belong to the software.
If you want to allow the program to connect to the Internet, for example to fetch updates, also add an exclusion of the type Allow an application to connect to the internet and use the Browse button to select the file you wish to grant access.
