
Why YOUR software is the new malware
Cybercriminals are increasingly turning away from malware and shifting to a stealthier approach known as Living Off the Land (LOTL).
For many years, the primary vector for bad things happening on computers was malicious software—malware. Correspondingly, a significant part of cybersecurity was about identifying and blocking this hostile code before it could cause trouble.
It was their software against your software.
But now, cybercriminals are increasingly turning away from malware and shifting to a stealthier approach known as Living Off the Land (LOTL). This method involves using legitimate tools and software to carry out malicious activities, like data theft, so that cybercriminals can blend in to their environment and avoid detection.
Detecting LOTL requires careful monitoring of Endpoint Detection and Response (EDR) alerts, to identify out of place behavior, making LOTL detection a matter of their people against your people.
Understanding the environment is paramount. With this baseline, security analysts can identify anomalies that might not seem malicious but aren’t common for the environment.
Hiep Hinh, Principal MDR Analyst, ThreatDown
According to the 2025 State of Malware report, LOTL techniques have now become an indispensable part of ransomware groups’ attack chains.
The Windows Remote Desktop Protocol (RDP) is particularly favored by ransomware groups, with 58% of ransomware attacks dealt with by ThreatDown’s Malware Removal Specialists starting with an RDP intrusion.
Although we tend to think of RDP as a method of initial access, it is also a LOTL tactic. A ransomware group that correctly guesses an RDP password hasn’t broken into a network using malware or a vulnerability—it has logged in and authenticated itself, and is operating as a legitimate user on the network.
However they gain access to a target, attackers often establish persistence with another kind of remote desktop software—remote monitoring and management (RMM) software such as AnyDesk and ConnectWise. RMM tools afford the same convenient access as RDP and also don’t look out of place on a company network.
The State of Malware report also highlights the most common LOTL techniques detected by ThreatDown EDR in 2024, including network service scanning, suspicious PowerShell executions, and unauthorized local account creations.
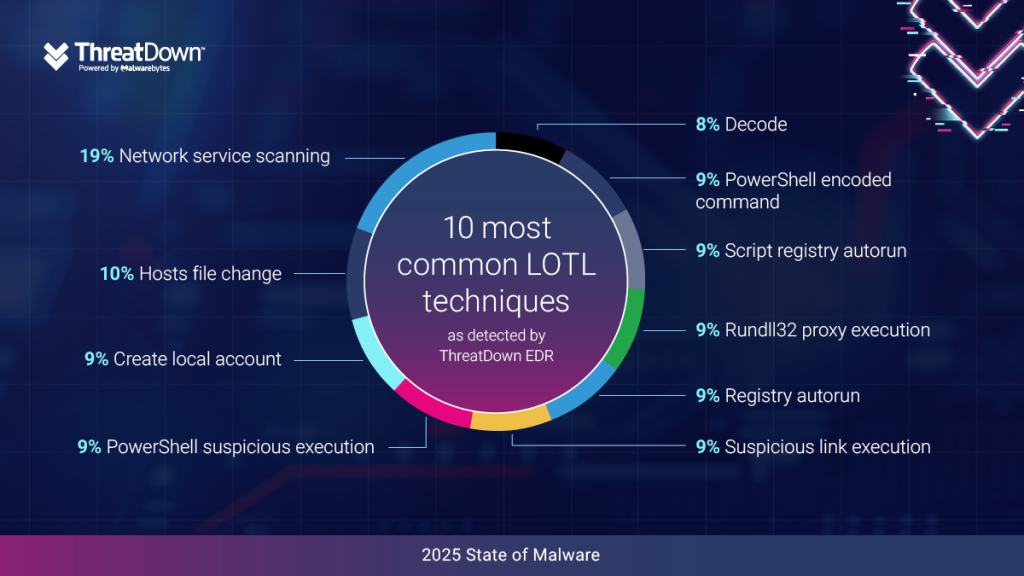
The increasingly popular LOTL approach highlights the importance of being able to identify suspicious or unexpected behaviors. Defenders must ensure that their monitoring tools are sophisticated enough to spot unusual patterns, such as uncommon execution times, unexpected modifications, or new account creations.
To learn more about LOTL and how criminal tactics are evolving, read the 2025 ThreatDown State of Malware report.



