
Upgrade now! New MOVEit Transfer vulnerability under active exploitation
A new vulnerability in MOVEit Transfer is already under active exploitation, just a day after a patch was released.
A critical authentication bypass vulnerability in Progress’ MOVEit Transfer is reportedly being actively exploited, just a day after a security bulletin and patch were released.
The vulnerability does not affect MOVEit Cloud, which has already been patched. The affected software versions are MOVEit Transfer 2023.0.0-2023.0.10, 2023.1.0-2023.1.5, and 2024.0.0-2024.0.1. To check which version you are using, take a look at MOVEit Transfer – How to Check My Software Version.
Users of software affected by the bug should upgrade as soon as possible. Progress notes that:
Upgrading to a patched release, using the full installer, is the only way to remediate this issue. There will be an outage to the system while the upgrade is running.
According to Progress, customers on a current maintenance agreement can access their upgrades by logging into the Progress Community.
You can find the patched release for your version in this table:
| Fixed Version | Documentation | Release Notes |
| MOVEit Transfer 2023.0.11 | Install and upgrade guide | Release Notes – 2023.0.11 |
| MOVEit Transfer 2023.1.6 | Install and upgrade guide | Release Notes – 2023.1.6 |
| MOVEit Transfer 2024.0.2 | Install and upgrade guide | Release Notes – 2024.0.2 |
Progress also recommends that users:
- Block public inbound RDP access to MOVEit Transfer servers.
- Limit outbound access to only known trusted endpoints from MOVEit Transfer servers.
The vulnerability at hand is listed as CVE-2024-5806, which has a CVSS score of 9.1 out of 10. The authentication bypass vulnerability was found in the SSH File Transfer Protocol (SFTP) module in Progress MOVEit Transfer. It allows an attacker to impersonate any user they want on the server.
The small amount of time between the release of the security bulletin and the start of active exploitation suggests that the patch was easy to reverse engineer. The situation is likely to get worse too, because while some cybercriminals now have a working exploit, the barrier to other groups doing the same is likely to be low.
As we noticed last year, ransomware groups like Cl0p have a special interest in exploitable vulnerabilities in file transfer software. The group accumulated the third-highest number of known victims in 2023, with just a few short campaigns exploiting zero-days in GoAnywhere MFT and MOVEit Transfer. In the few months when it was active it was way ahead of its competition.
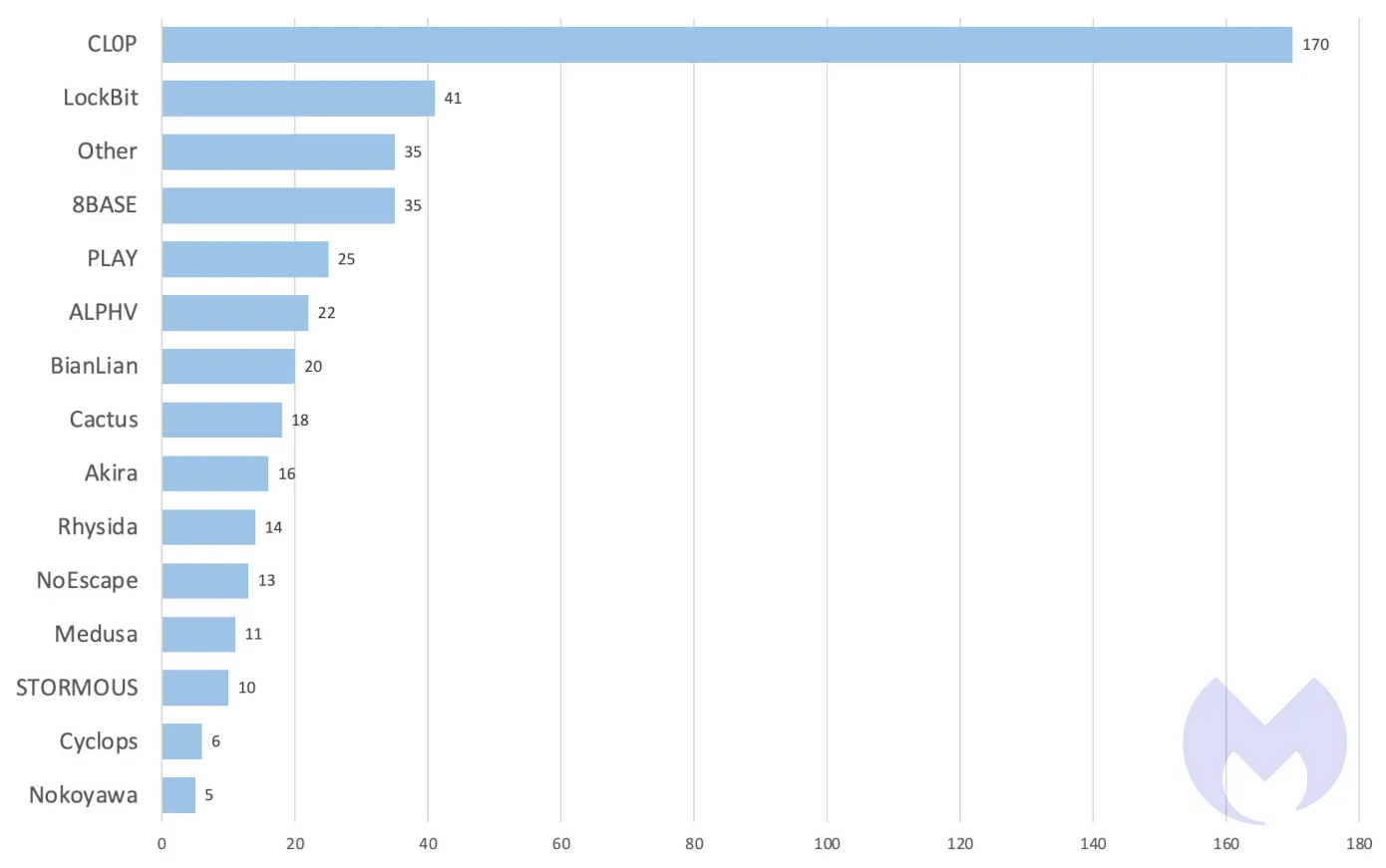
The only silver lining this time is that while Cl0p used zero-days, users have an opportunity to defend themselves by patching this latest vulnerability—if they’re quick.
So, while it’s good to be forewarned, it’s better to get that upgrade installed.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.



