
[Updated April 3] 3CX desktop app used in a supply chain attack
Researchers have found that the 3CX desktop app may be compromised and used in supply chain attacks.
The 3CX Desktop App is a Voice over Internet Protocol (VoIP) type of application which is available for Windows, macOS, Linux and mobile. Many large corporations use it internally to make calls, view the status of colleagues, chat, host web conferences, and for voicemail. 3CX is a Private Branch Exchange (PBX) system, which is basically a private telephone network used within a company or organization.
The 3CX website boasts 600,000 customer companies with 12 million daily users, which might give you an idea of the possible impact a supply chain attack could have.
The discovered attack is very complex and probably has been going on for months. While attribution in these cases is always difficult, some fingers are pointing to North Korea. It is likely the attacks have been ongoing since one of the shared samples was digitally signed on March 3, 2023, with a legitimate 3CX Ltd certificate issued by DigiCert.
While it is almost certain that Windows Electron clients are affected, there is no evidence so far that any other platforms are. On the 3CX forums, users are being told that only the new version (3CX Desktop App) leads to the malware infection, because the 3CX Phone for Windows (the legacy version) is not based on the Electron Framework. Electron is an open source project that enables web developers to create desktop applications.
Update March 31, 2023: an independent researcher and 3CX have confirmed that the Mac version of the desktop client is compromised as well.
According to a 3CX spokesperson, this happened because of an upstream library it uses became infected.
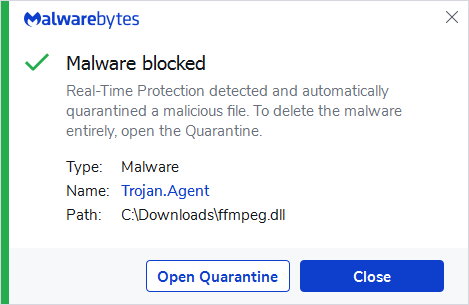
The main executable is not malicious itself and can be downloaded from 3CX’s website as part of an installation procedure or an update. The 3CXDesktopApp.exe executable, however, sideloads a malicious dynamic link library (DLL) called ffmpeg.dll.
The ffmpeg.dll in turn is used to extract an encrypted payload from d3dcompiler_47.dll and execute it. The malware then downloads icon files hosted on GitHub that contain Base64 encoded strings appended to the end of the images, as shown below.
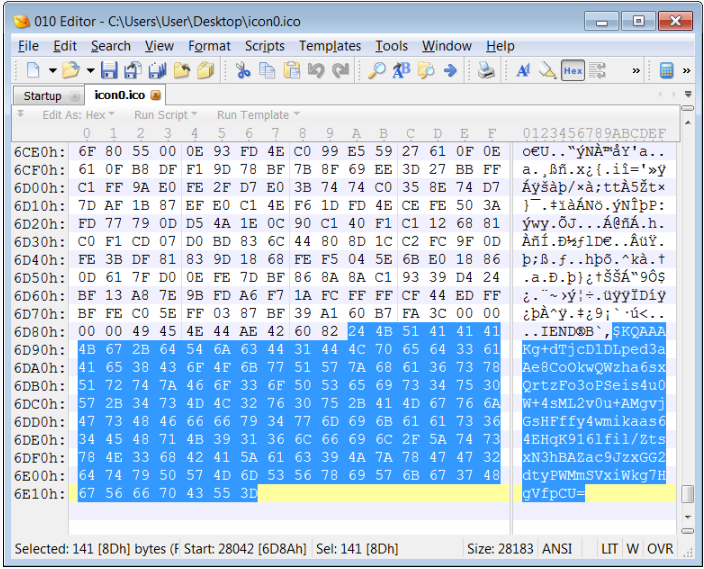
The d3dcompiler_47.dll file has all the functionality of the legitimate version, with the payload appended. This warrants that it would alert users to the fact that something is wrong with their software.
While research is ongoing into the full payload, it is clear that a backdoor is created on affected systems.
What needs to be done?
After initially playing down the alerts on its user forums as a possible false positive, 3CX has now posted that it is working on an update.
The advice on the 3CX forums is to uninstall the app and then reinstall it, accompanied by a strong advice to install the PWA client instead.
Update April 3: 3CX has published a blog with uninstall instructions for Windows, Mac, and a Powershell script suitable for mass uninstalls.
Malwarebytes detects the malicious DDLs as Trojan.Agent (ffmpeg.dll) and Trojan.Compromised3CX (%LOCALAPPDATA%PROGRAMS3CXDesktopApp*d3dcompiler_47.dll).
We will keep you updated here, but as a user you might want to keep an eye on 3CX’s blog and forums to learn about new developments, and when an update is available.



