
The anatomy of a Medusa ransomware attack: ThreatDown MDR team investigates
In early April 2024, a prominent service chain in the United States fell victim to a Medusa ransomware attack.
In early April 2024, a prominent service chain in the United States fell victim to a Medusa ransomware attack. This case study dissects the attack’s framework, exploring the chronological events, key indicators of compromise (IOCs), and steps the ThreatDown MDR team took to mitigate the infection.
About Medusa ransomware
Medusa is a relatively new ransomware gang with an outsized focus on attacking companies in the the US and the Services Industry. That said, there are two industries they attack at an above-average rate: Education and Healthcare.
To learn more about Medusa, read our overview here.
Discovery and initial indicators
Incident timeline
- Initial detection (8:30:59 AM, 04/07/2024): The first alert was triggered by an SHA256 hash match for a file later identified as part of the Medusa ransomware.
- SHA256: 3CA3A0B5AEEB05EF1A7E789B339BFDD2465CD09880416A325A1337C2E6D1188E
- Confirmation of infection (8:33:27 AM, 04/07/2024): An SA alert confirmed the infection on one of the machines.
- Last recorded activity (8:44:47 AM, 04/07/2024): The last activity linked to the ransomware was noted, indicating the spread and execution of the malicious payload.
System compromise details
- Compromised Path:
C:\WINDOWS\SYSTEM32\NTOSKRNL.EXE - Process ID (PID): 4
- Security Violation: Ransomware Activity Rule Trigger
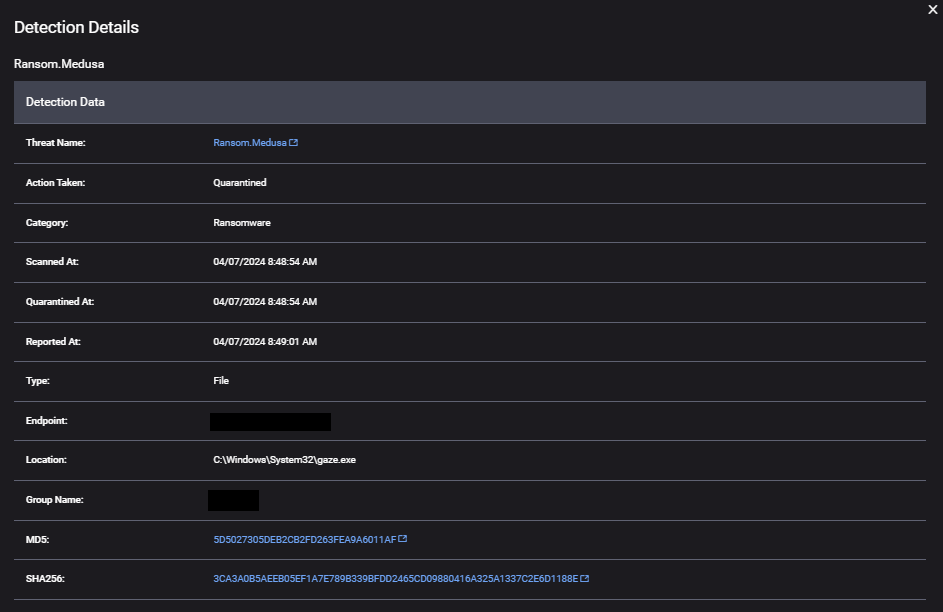
Key Indicators of Compromise (IOCs)
The attack’s footprint was identified through various system and network indicators:
- Executable paths and malicious files:
- Primary execution:
C:\Windows\AdminArsenal\PDQDeployRunner\service-1\PDQDeployRunner-1.exe - Additional malicious files:
C:\Windows\PSEXESVC.exeC:\Windows\System32\gaze.exe%WINDIR%\g0bSJ5IAHi.exe
- Primary execution:
- Network and configuration files:
APPDATA\LOCAL\CISCO\CISCO ANYCONNECT SECURE MOBILITY CLIENT\PREFERENCES.XML
Detailed analysis of IOCs
- Ransomware payload:
c:\windows\system32\gaze.exe(SHA1: 5D5027305DEB2CB2FD263FEA9A6011AF) - Driver loaders:
C:\WINDOWS\G0BSJ5IAHI.EXE(SHA1: 35dfc1fcb06fe31264a3fc7ff307e166)C:\USERS\<redacted>\APPDATA\LOCAL\TEMP\LOW\G0BSJ5IAHI.EXE(SHA1: 35dfc1fcb06fe31264a3fc7ff307e166)
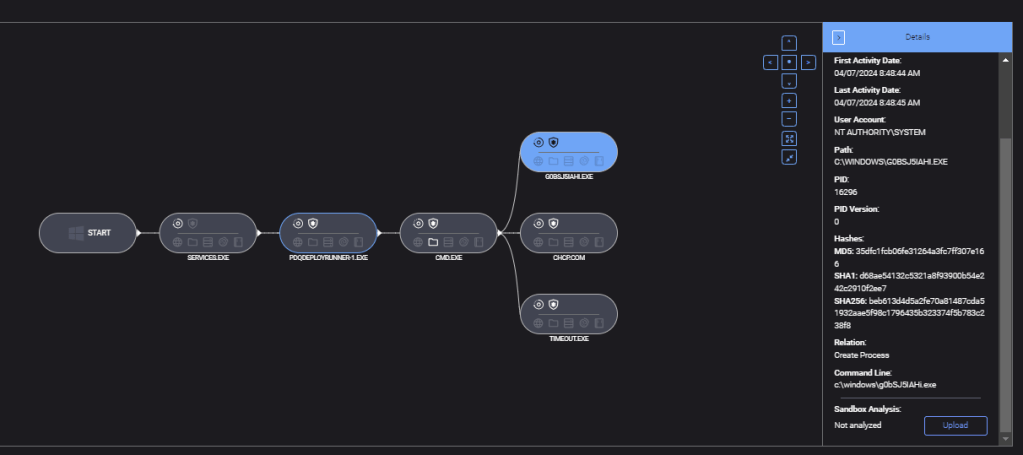
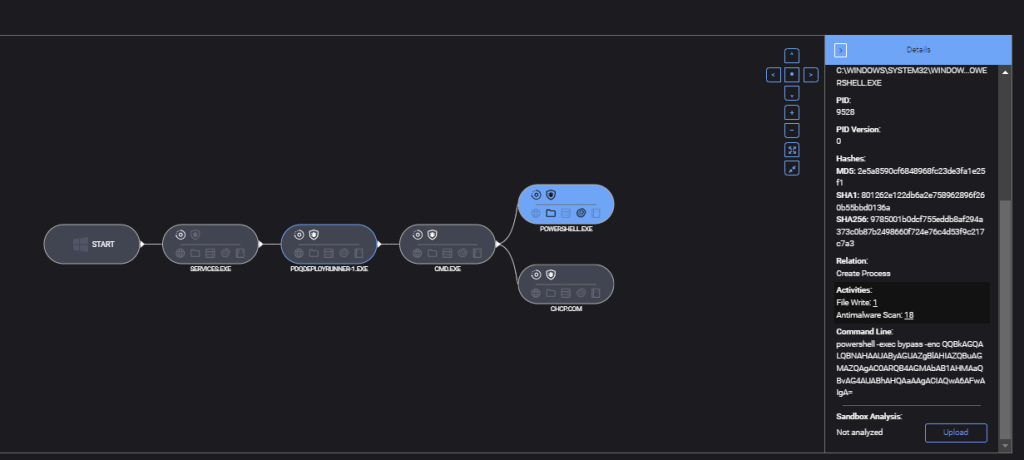
Attack execution
Attackers executed three main actions:
- PowerShell manipulation: A malicious command was launched to exclude the C: drive from Microsoft Defender’s real-time monitoring.
- Vulnerable driver loading: A payload was executed to load a vulnerable driver capable of terminating active processes of Defender and ThreatDown.
- Payload deployment: The Medusa ransomware payload was deployed through the manipulated PDQ Deploy.
Stopping Medusa ransomware
As we’ve seen in our 2024 State of Ransomware report, businesses in the Services sector, such as this company, continue to be a prime target for attackers. In this case, Medusa used malicious PowerShell commands and PDQ Deploy in an attempt to spread their ransomware. Fortunately, the ThreatDown MDR team successfully identified and alerted the customer to the attack, allowing them to isolate affected endpoints before further damage could be done.
Purpose-built for organizations with small (to non-existent) security teams that lack the resources to address all security alerts, the ThreatDown Elite Bundle includes award-winning technologies and 24x7x365 expert-managed monitoring and response from the ThreatDown MDR team.



