
Ransomware review: May 2024
April was the second most active month of 2024 as ransomware groups positioned themselves to take over from LockBit and ALPHV.
This article is based on research by Marcelo Rivero, Malwarebytes’ ransomware specialist, who monitors information published by ransomware gangs on their Dark Web sites. In this report, “known attacks” are those where the victim did not pay a ransom. This provides the best overall picture of ransomware activity, but the true number of attacks is far higher.
In April, we recorded a total of 373 confirmed ransomware attacks. This makes April the second most active month for ransomware gangs in 2024 so far.
Last month, we continued to see the aftermath of the LockBit and ALPHV law enforcement actions. In April, LockBit only posted a total of 28 victims to its leak site—the lowest in its entire history. ALPHV, meanwhile, displayed no victims, effectively confirming its shutdown.
While LockBit is technically still alive, it’s fair to say the group is not what it was: Not only are its attacks dwindling, but in early May law enforcement also revealed the identity of alleged LockBit leader Dmitry Khoroshev, aka LockBitSupp. LockBitSupp, who is now subjected to a series of asset freezes and travel bans, also has a reward of up to $10 million over his head for information that leads to his arrest.
As the old tyrants get deposed, however, new ones rise to take their place.
The PLAY ransomware gang is the current leader, and other groups, such as Medusa and Hunters International, are also higher up on the charts than normal since LockBit and ALPHA’s collapse, signaling a shift in the RaaS landscape. However, the most striking thing about the ransomware in May 2024 is that for the first time in years, no one group is dominant.
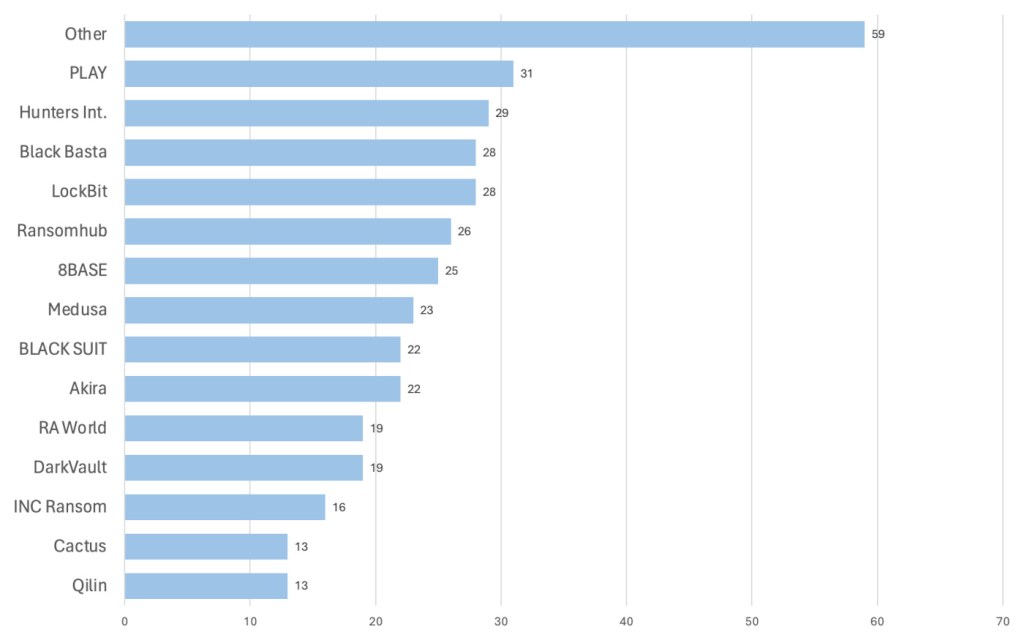
Speaking of ransomware gangs racking up victims for a short time period, the RansomHub group published an unprecedented 26 victims on its leak site in April, the fifth most that month. Perhaps most important, however, is the fact that the group began leaking stolen data from Change Healthcare, a subsidiary of the UnitedHealth Group.
Readers might be understandably confused if they remember hearing that Change Healthcare was attacked by a different group, ALPHV, in February. In that story, ALPHV was allegedly paid the full $22 million ransom and suddenly disappeared in an unconvincing exit scam. A month later, however, newcomer ransomware group RansomHub listed Change Healthcare as a victim on its website, claiming:
ALPHV stole the ransom payment (22 Million USD) that Change Healthcare and United Health payed in order to restore their systems and prevent the data leak.
HOWEVER we have the data and not ALPHV.
ThreatDown Cybersecurity Evangelist Mark Stockley writes about the mix-up: “Quite how the data made it from ALPHV to RansomHub isn’t known, but the most likely route is that the disgruntled ALPHV affiliate simply found a new partner to work with in newcomer RansomHub.”
RansomHub claimed that it had 4 TB of “highly selective data,” which includes medical records, dental records, payments information, claims information, PII belonging to patients and US military personnel, and insurance records. In mid-April, the group raised the stakes by posting a selection of screenshots on its leak site and threatening to release the rest in two days’ time if it didn’t receive a ransom.
Lo and behold, during a hearing before the US Senate Committee on Finance shortly thereafter, UnitedHealth CEO Andrew Witty confirmed that the company paid a $22 million ransom to the attackers.
To round out the whole Change Healthcare saga—which is already being described as the most significant cyberattack on the US healthcare system in history—details of how the company’s network was breached finally emerged last month. Can you take a guess? If you said it was due to the company not having multi-factor authentication (MFA) enabled, you’d be right
New group: dAn0n
dAn0n is a new ransomware gang that published the data of 8 victims on its leak site in April.
New player: DarkVault
DarkVault is a new ransomware gang that published the data of 19 victims on its leak site in April. The group, which resembles LockBit with a similar website design, and its use of the LockBit Black ransomware, has spurred rebranding rumors. It’s important to remember, however, that many gangs mimic LockBit’s leak site and use its leaked ransomware builder.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.



