
Ransomware review: April 2023
Threat Intelligence Team
Threat Intelligence Team
This article is based on research by Marcelo Rivero, Malwarebytes’ ransomware specialist, who monitors information published by ransomware gangs on their Dark Web sites. In this report, “known attacks” are those where the victim didn’t pay a ransom. This provides the best overall picture of ransomware activity, but the true number of attacks is far higher.
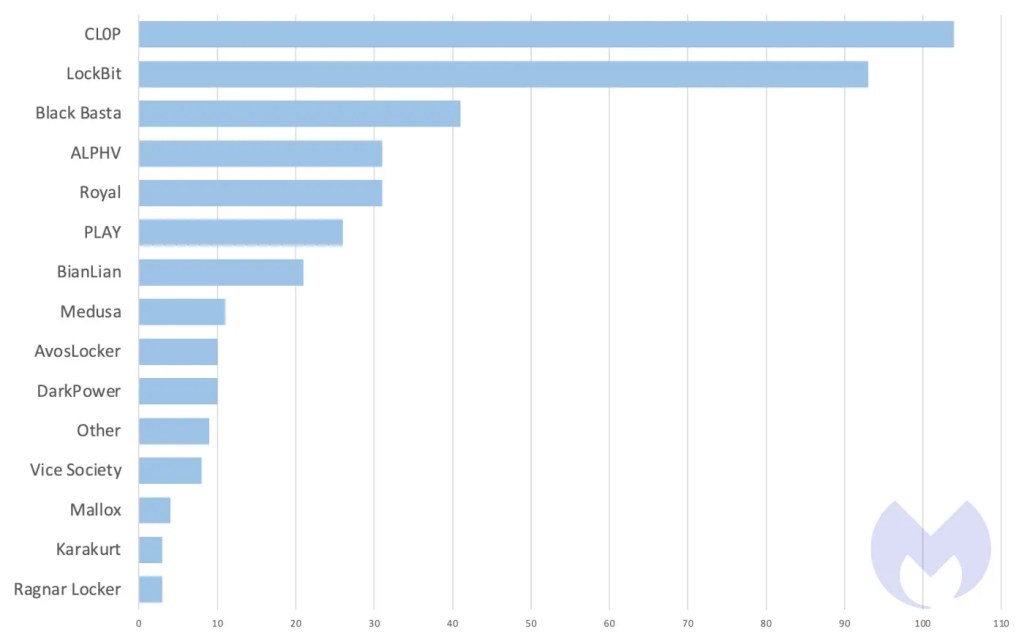
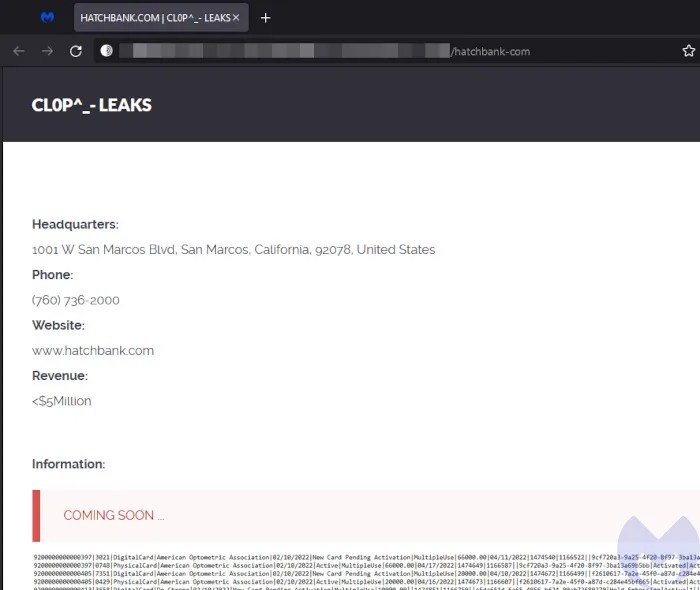
In a surprising turn of events for the ransomware landscape, Cl0p has emerged as the most used ransomware in March 2023, dethroning the usual frontrunner, LockBit. Indeed, while LockBit was still used in 93 successful attacks last month, it couldn’t quite match the sheer force of Cl0p’s sudden resurgence.
Contributing to Cl0p’s rise to the number one spot was its extensive GoAnywhere campaign. The group successfully breached over 104 organizations by taking advantage of a zero-day vulnerability in the widely-used managed file transfer software, GoAnywhere MFT.
March has also seen some intriguing activity from other ransomware gangs like DarkPower, which appeared to be turning on and off throughout the month, as well as BianLian, which has shifted its focus from encrypting files altogether to pure data-leak extortion.
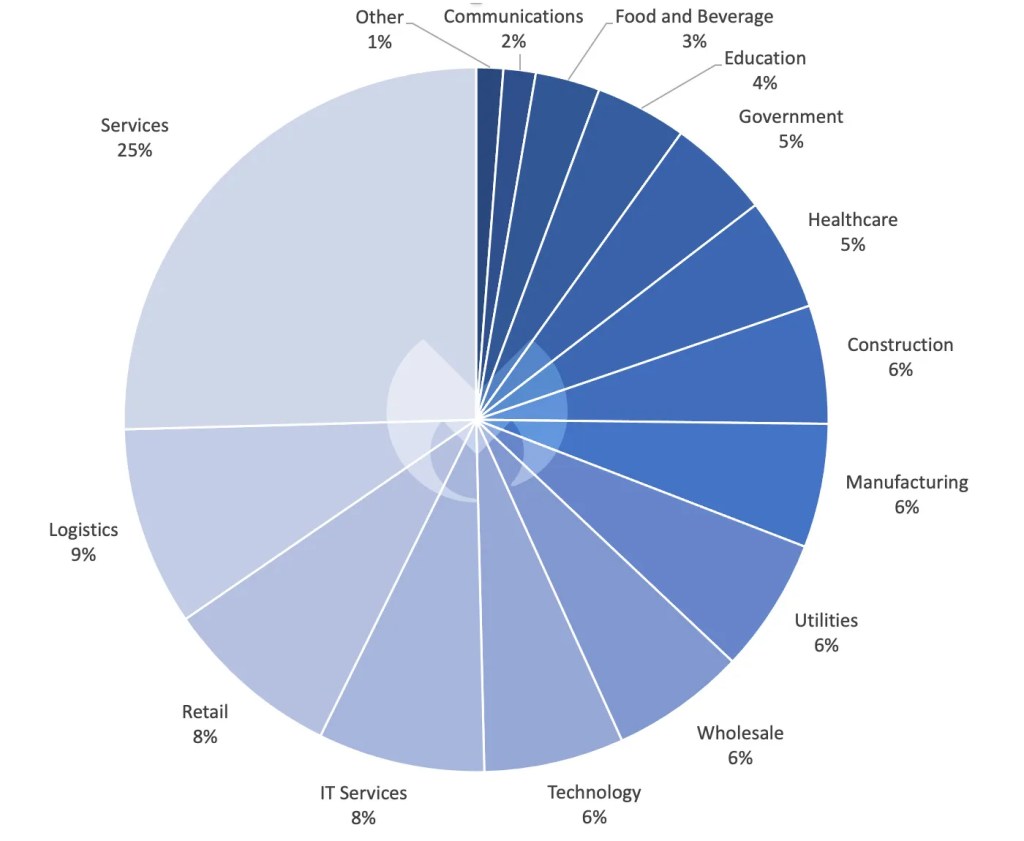
Fortra, the company behind GoAnywhere MFT, released an emergency patch (7.1.2) for the vulnerability in early February—but by then, Cl0p had already used it to break into a myriad of networks and deploy ransomware.
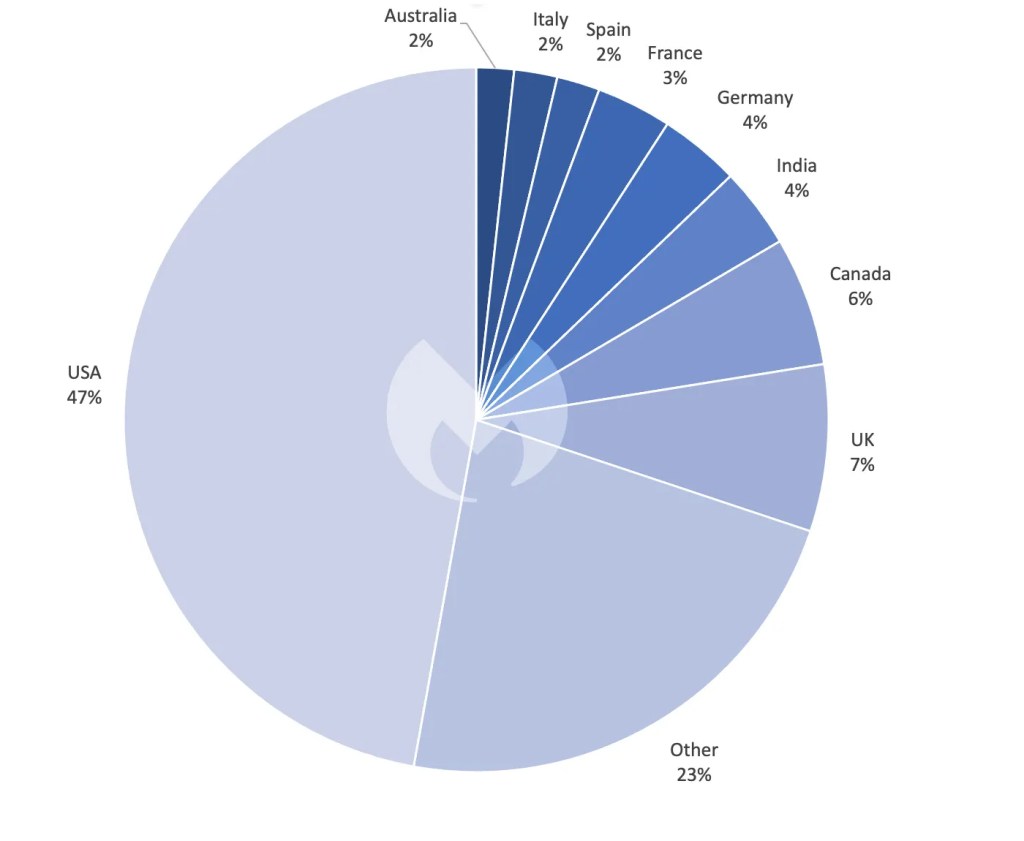
Recent research by Malwarebytes highlighted the bias that ransomware gangs have for attacking English-speaking countries, and the Cl0p campaign follows the same trend. Between them, the Anglosphere countries of the USA, Canada, UK, and Australia accounted for 69% of known Cl0p attacks, with Canada and Australia suffering more attacks than countries with bigger populations and economies, like Germany and France.
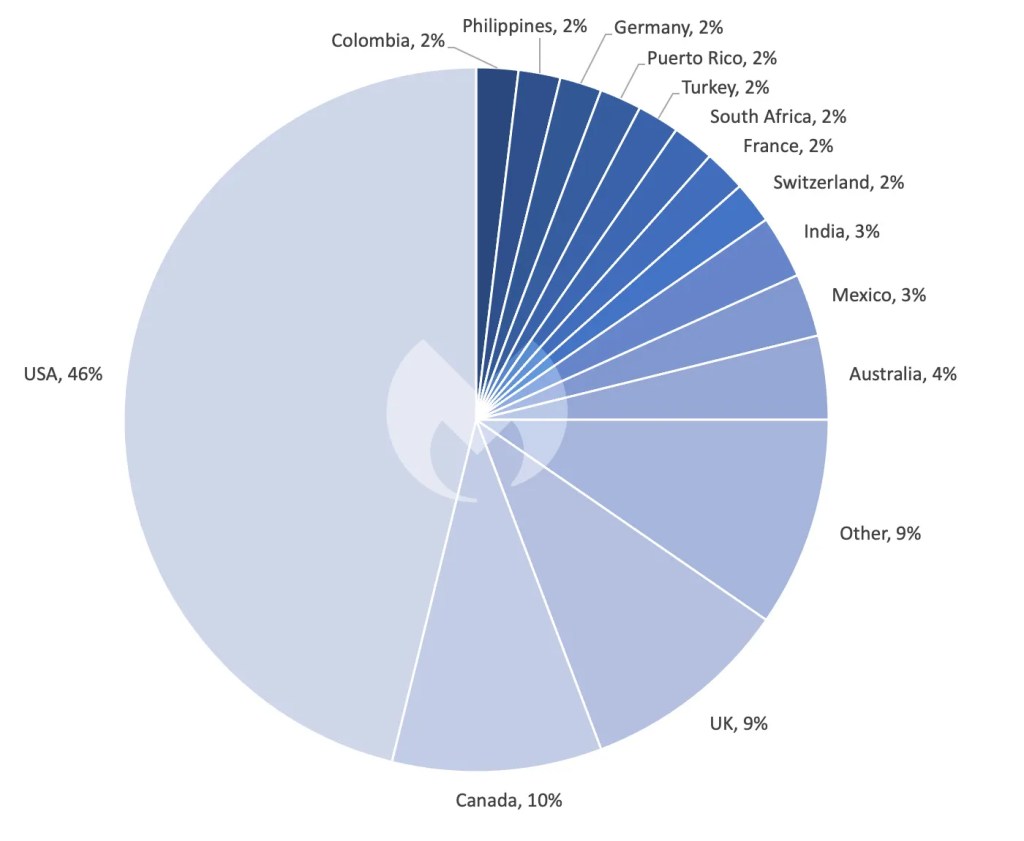
Cl0p’s ability to exploit a zero-day to such effect is akin only in recent memory to the Kaseya VSA ransomware incident in July 2022. The Kaseya attack involved a malicious auto-update that pushed the REvil ransomware onto victims’ machines, primarily targeting Managed Service Providers (MSPs), causing widespread downtime for over 1,000 companies.
The successful use of zero-day vulnerabilities by ransomware gangs like Cl0p and REvil is, thankfully, relatively rare. However, when it happens it can be devastating. Ransomware gangs are always looking for new tactics to help them maximize the impact of their attacks and, rare or not, we should all be concerned about the example Cl0p has set for weaponizing a newly discovered vulnerability and exploiting it before a patch is released or applied.
Cl0p wasn’t the only gang we saw last month experiencing an unexpected surge in activity.
BlackBasta and LockBit
In January 2023, we noted a complete absence of activity from BlackBasta, a group which up to that point had usually ranked highly on our monthly charts. That trend continued into February, but in March it returned with a vengeance with over 40 known victims. It’s hard to tell why BlackBasta went underground for two months only to eventually burst back onto the scene, but it’s possible that the group was working on developing new attack techniques or evading detection. Other possibilities are a sudden change in leadership, that the group wanted to lay low to avoid the attention of law enforcement, or it simply wanted a break. This kind of thing isn’t unusual and the group’s sudden re-emergence highlights the unpredictable nature of ransomware gangs and the need for constantly monitoring the latest threat intelligence. Just because a group is gone today doesn’t mean it won’t be back tomorrow.
Meanwhile, LockBit’s activity in March was headlined by a major ransomware attack on Essendant, a US-based distributor of office products. This attack, which is said to have begun on or around March 6, created severe ramifications for the organization, disrupting freight carrier pickups, online orders, and access to customer support.
In other LockBit news, a CISA advisory on LockBit 3.0 ransomware was released on March 16, 2023. LockBit 3.0, also called LockBit Black, was discovered in June 2022. While many of LockBit 3.0’s TTPs remain consistent with previous versions, the advisory sheds light on the updated and enhanced features in LockBit 3.0. These improvements include more advanced detection evasion methods and customization options that enable affiliates to modify the ransomware’s behavior according to their requirements, making the ransomware harder to detect and counter.
Dark Power
March saw the rise of Dark Power, a new ransomware group that tallied 10 victims. Dark Power’s ransomware is interesting in that it is written in the relatively obscure Nim programming language.
Dark Power’s approach to ransomware, despite being relatively basic, manages to create unique encryption keys for each targeted machine, making it difficult to develop a generic decryption tool. The ransomware effectively stops services and terminates processes, ensuring the encryption process is unhindered. It also clears logs, making it harder for analysts to investigate an attack.
The effectiveness of Dark Power ransomware underlines the fact that attackers do not always need advanced, novel techniques to succeed. A basic approach, executed well and combined with an adaptable programming language, can prove to be just as effective.

BianLian
BianLian, a ransomware gang that first appeared in July 2022 and has consistently hovered near the top of our monthly charts, has shifted its focus from encrypting files to data-leaks. The group’s shift in focus can be attributed to the release of a decryption tool by Avast, which made encrypting files less effective for BianLian. Consequently, the group now focuses on threatening to leak stolen data to extort payments from victims instead.
BianLian’s shift toward data-leak extortion demonstrates that RaaS gangs can be highly adaptable to changing circumstances, such as the emergence of decryption tools that undermine encryption-based ransomware. This strategic shift allows them to maintain a steady income stream, even as traditional methods lose their effectiveness.
As organizations face the daunting prospect of sensitive data leaks or security breach exposure, they are more likely to pay ransoms to avoid legal, financial, and reputational repercussions. Furthermore, the lingering threat of leaked data, even after recovering encrypted files, makes it harder for victims to resist paying ransoms.
Our Ransomware Emergency Kit contains the information you need to defend against ransomware-as-a-service (RaaS) gangs.



