
Patch now! Cactus exploits Qlik Sense to deliver ransomware
Researchers say the Cactus ransomware group is exploiting vulnerabilities in Qlik Sense.
Dutch researchers are warning Qlik Sense users that haven’t patched their data visualization and business intelligence tool that the Cactus ransomware group is actively exploiting vulnerabilities in the software to deliver its ransomware.
Qlik Sense is a Software-as-a-Service (SaaS) platform that provides business intelligence analytics. According to the researchers, the Cactus ransomware group has been actively targeting it since November of 2023.
The specific vulnerabilities are CVE-2023-41266, CVE-2023-41265 aka ZeroQlik, and potentially CVE-2023-48365, aka DoubleQlik, which patched an incomplete fix for CVE-2023-41265. Patches have been available for all these vulnerabilities since September 2023.
Based on an initial scan on April 17, 2024, the researchers identified 5,205 Qlik Sense servers of which 3,143 seem to be vulnerable to the exploits used by the Cactus group.
Qlik updates can be downloaded from the official Qlik download page (customer login required).
We talked about the Cactus ransomware group in our August 2023 ransomware review. The group emerged in March 2023 as a fresh strain of ransomware, zeroing in on large-scale commercial operations.
Back then, we noted that Cactus exploits well-known vulnerabilities present in VPNs. Once Cactus operatives gain access to a network, they enumerate local and network user accounts and reachable endpoints. Following this, they create new user accounts and deploy their ransomware encryptor. The uniqueness of Cactus lies in its use of specialized scripts that automate the release and activation of the ransomware through scheduled tasks.
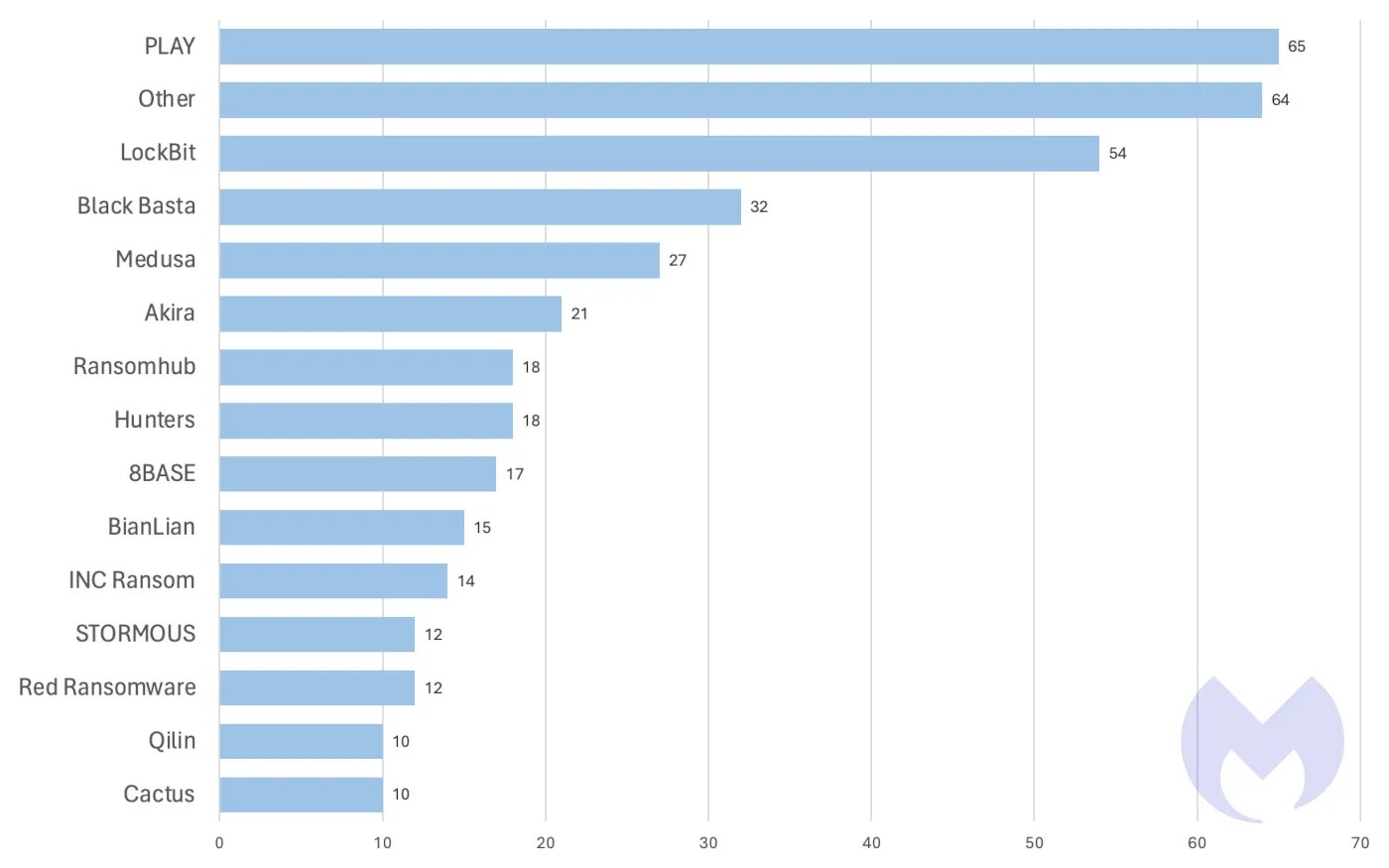
In March 2024, Cactus was the 14th most active ransomware gang globally.
How ThreatDown stops ransomware
ThreatDown bundles take a comprehensive approach to these challenges. Our integrated solutions combine EP, VPM, and EDR technologies, tailored to your organization’s specific needs. ThreatDown’s select bundles offer:
- Advanced Web Protection: Blocking phishing websites ransomware gangs use for initial access.
- RDP Shield: Securing remote access points with Brute Force Protection.
- Continuous Vulnerability Scanning and Patch Management: Identifying and patching weaknesses before ransomware gangs can exploit them.
- Sophisticated EDR: Detecting and neutralizing advanced threats such as LockBit within the network.
- Ransomware Rollback: Reversing the impact of any successful attacks.
For resource-constrained organizations, select ThreatDown bundles offer Managed Detection and Response (MDR) services, providing expert monitoring and swift threat response to ransomware threats—without the need for large in-house cybersecurity teams.



