
Mobile Menace Monday: AndroRAT Evolved
Nathan Collier
Nathan Collier
An increasing amount of mobile malware known as Android/Trojan.AndroRAT has been seen in the wild lately. AndroRAT is a contraction of Android and RAT (Remote Access Tool). This piece of malware is far from new, but has gradually become more evolved over the years.
AndroRAT History
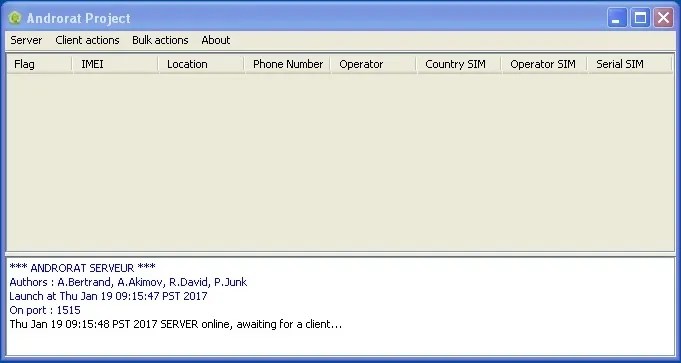
As the story goes (according to its GitHub page), the original AndroRAT was created as a proof of concept by a small team of developers for a University project in 2012. It has two parts: the AndroRAT server which runs on a PC to control infected mobile devices, and the AndroRAT client which is installed onto a mobile device.
With a little Android development knowledge, the AndroRAT proof of concept could be used as a Trojan by taking an existing legitimate APK, decompiling it, adding the AndroRAT client code into the APK, and recompiling the APK. After installing the infected APK onto a mobile device, it can be controlled via the AndrodRAT server which is a simple GUI interface.
Here are just some of the functionalities of AndroRAT:
- Collect contacts
- Collect call logs
- Collect all messages including SMS
- Record calls
- Location through GPS
- Take a picture from the camera
- Send a SMS message
- Make outgoing calls
- Open an URL in the default browser
AndroRAT Binder
Soon after the original AndroRAT was uploaded to GitHub, the malware authors took it a step further and created AndroRAT Binder; an APK builder that adds the AndroRAT client code to any APK. AndroRAT Binder made building infected APKs so easy, that any script kiddie could use it.
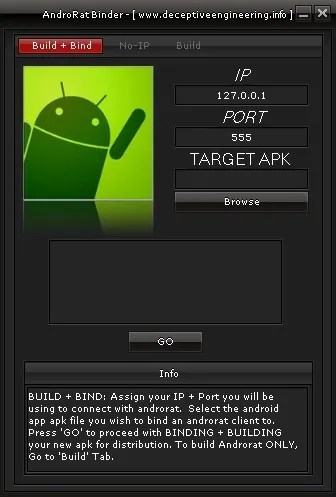
Simply add the IP and port used to connect the AndroidRAT server to the client, provide a legitimate APK (most likely from Google PLAY) to repackage with AndroRAT, and build. Once built, the infected APK could be put onto third party markets and/or file sharing sites for unsuspecting victims to install. Considering we have found around 31k infected APKs that used the default settings of the AndroRAT Binder in our Mobile Intelligence System, it seems it caught on like wild fire.
AndroRAT Evolved
The AndroRAT variants we see in the wild today are far from the original open source code uploaded to GitHub back in 2012. Updated coding has improved the functionality, made it more stable, and added obfuscation to deter against detection by malware scanners. With the recent increase of AndroRAT in the wild, I predict the distribution method has greatly improved as well. The old AndroRAT Binder made building an infected APK easier, but still only built APKs one at a time. Most likely new builders have been developed that are capable of automating the process even further; such as bulk building AndroRAT infected APKs using legitimate apps.
The RAT is Always Lurking
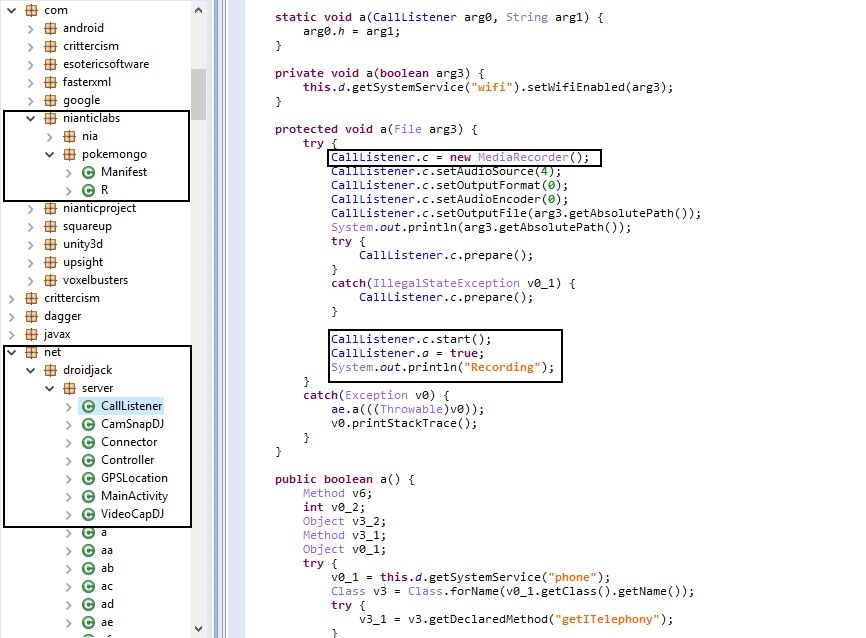
AndroRAT client infected APKs run just like the apps they steal, but with added malicious functionality in the background. If an app is popular on Google PLAY, most likely there is an AndroRAT infected version of it somewhere in the wild. For example, here’s some code of an infected Pokémon GO app:
Trapping the RAT
As usual, it’s a cat and “RAT” game between malware developers and malware researchers. They keep putting new variants of AndroRAT out in the wild, we keep detecting them as they emerge. The best way to trap this RAT is to have a good malware scanner installed on your mobile device, and to install apps from reputable stores such as Google PLAY. Stay safe out there!



