
Memory scan
Memory Scan
You may have noticed this line in a Malwarebytes Anti-Malware log “Memory : Enabled” or looked at the setting shown below.
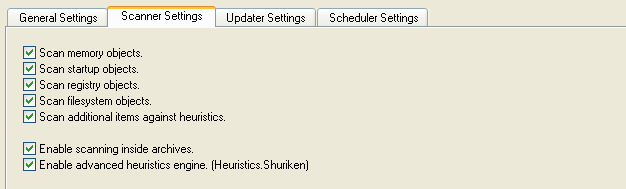
To explain why you would want Malwarebytes Anti-Malware, or your anti-virus for that matter, to scan your computer’s memory, we need to explain a few other things first.
Basically it comes down to scanning files that are actively being used in their raw (unpacked) state. For a more elaborate explanation of this statement and the basic principles it is based on, keep reading.
What is the Active Memory of your computer?
The active memory of the computer is made up off the RAM that you have available.
If the RAM is not big enough for the current operations, Windows adds Virtual Memory to the resources. Virtual memory moves data from RAM to a space called a paging file, typically located on your hard disk.
Your computer can read data from RAM much more quickly than from a hard disk, so adding RAM is a recommended solution if this happens regularly.
Once your computer is put to work, files are unpacked, if necessary, and loaded in active memory to speed up computer operations. These can be programs but also libraries, (partial) databases or whatever the computer might need to perform the given tasks.
Unpacked?
Yes. Some files are packed to make them smaller or, more often, to obfuscate their content. Since the active memory is all about speeding up operations, packed files are not copied as such, but their unpacked equivalents are loaded in memory.
But this behavior has some consequences that you may not notice during every day use. Nevertheless it is good to know what happens and what the ramifications can be.
You may for example have heard of POS Malware which is basically a RAM scraper that can extract certain information from RAM, like for example the credit card data during the recent Target breach, where the malware took the data from the one place where it is not encrypted. You guessed it: in the RAM of the Point-of-Sale that has to check the validity of those data. RAM scrapers can be customized to go after any other particular kind of data like email-addresses as well.
The Memory Manager
To control and oversee the operations necessary to optimize the use of RAM, there is a Memory Manager.
One vital service provided by the Memory Manager includes memory-mapped files. Memory-mapping can speed-up sequential file processing due to the fact the data is not sought randomly, and it provides a mechanism for memory-sharing between processes (when they are referencing the same DLL, as there must be only one instance at a time of any DLL.
This is not an easy task when for current computers it is not uncommon to have to deal with systems with several gigabytes of physical memory. Because the virtual address space might be larger or smaller than the physical memory on the machine, the Windows Memory Manager has two first-in-rank responsibilities.
The first is to translate, or map, a process’s virtual address space into physical memory so that when a thread is running in the context of that process reads or writes to the virtual address space, the correct physical address is referenced.To do this there are some helpful tools.
PID , VAD and File Mapping
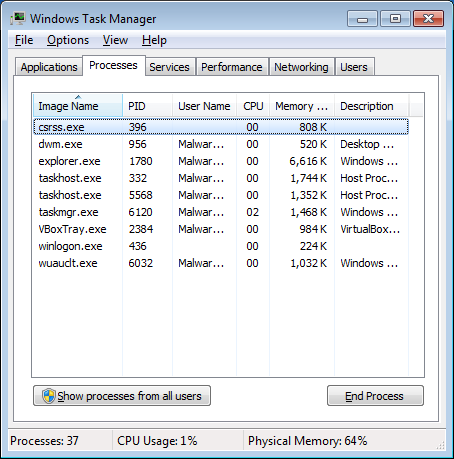
Each process running in Microsoft Windows is assigned a unique decimal number called the process ID, or PID. This number is also used to specify the process when attaching a debugger to it. You can see the running processes and their PID in Task Manager, if you have that column enabled.
Virtual Address Descriptors (VAD) record the usage of virtual addresses by a process and helps breaking up physical memory into more manageable and semantically meaningful units. A file view is the portion of virtual address space that a process uses to access the file’s contents.
File mapping is the association of a file’s contents with a portion of the virtual address space of a process. File mapping allows the process to use both random input and output (I/O) and sequential I/O. It also allows the process to work efficiently with a large data file, such as a database, without having to map the whole file into memory.
File mapping also can be used to share a file or memory between two or more processes. To share a file or memory, all of the processes must use the name or the handle of the same file mapping object. As you can imagine all these pointers are a real necessity if you want to find your way in a few gigabytes of raw data.
Summary
I think that answered the question why we advise to scan the memory when using Malwarebytes Anti-Malware (or your AV).
No matter which packer deception techniques may have been used, your protection module and threat scan will recognize the unpacked file in memory.
Also, the files that are loaded into RAM are the ones that are active and pose the most acute threat. It may also have given you some insight as to why it takes relatively long to scan the memory.



