
Giant health insurer struck by ransomware didn’t have antivirus protection
The Philippine Health Insurance Corporation (PhilHealth), has confirmed that it was unprotected by antivirus software when it was attacked by the Medusa ransomware group in September.
Antivirus software—or more correctly, its modern descendents endpoint security and Endpoint Detection and Response (EDR)—are essential tools in the battle against cybercrime. EDR can detect an intruder’s suspicious activity in advance of them running ransomware, as well as being able to identify the ransomware itself.
Because of this, ransomware groups, who can spend days or even weeks setting up an attack inside a compromised network, will typically try to disable antivirus software.
GMA News reports that PhilHealth confirmed that lack of antivirus on its news programme, 24 Oras:
In Mark Salazar’s report on “24 Oras” on Monday, PhilHealth confirmed that its antivirus software had expired on April 15, but that it had not been able to renew its subscription immediately due to complicated government procurement processes.
PhilHealth is the government owned and controlled corporation that provides universal health coverage in the Philippines. It was attacked on September 22, 2023.
According to a recent post on its Facebook account, all of the corporation’s public-facing applications have been back online since October 6, 2023, including “the website, Member Portal, eClaims for electronic submission of hospital claims, and EPRS for employer remittances.”
The organisation deserves praise for recovering its systems swiftly and for refusing to pay the ransom demand, which is reported to be around $300,000. In response, the Medusa ransomware group has made data stolen in the attack available for download on its dark web leak site, saying the “Company came to the tor chat but didn’t answer for the payment yet.”
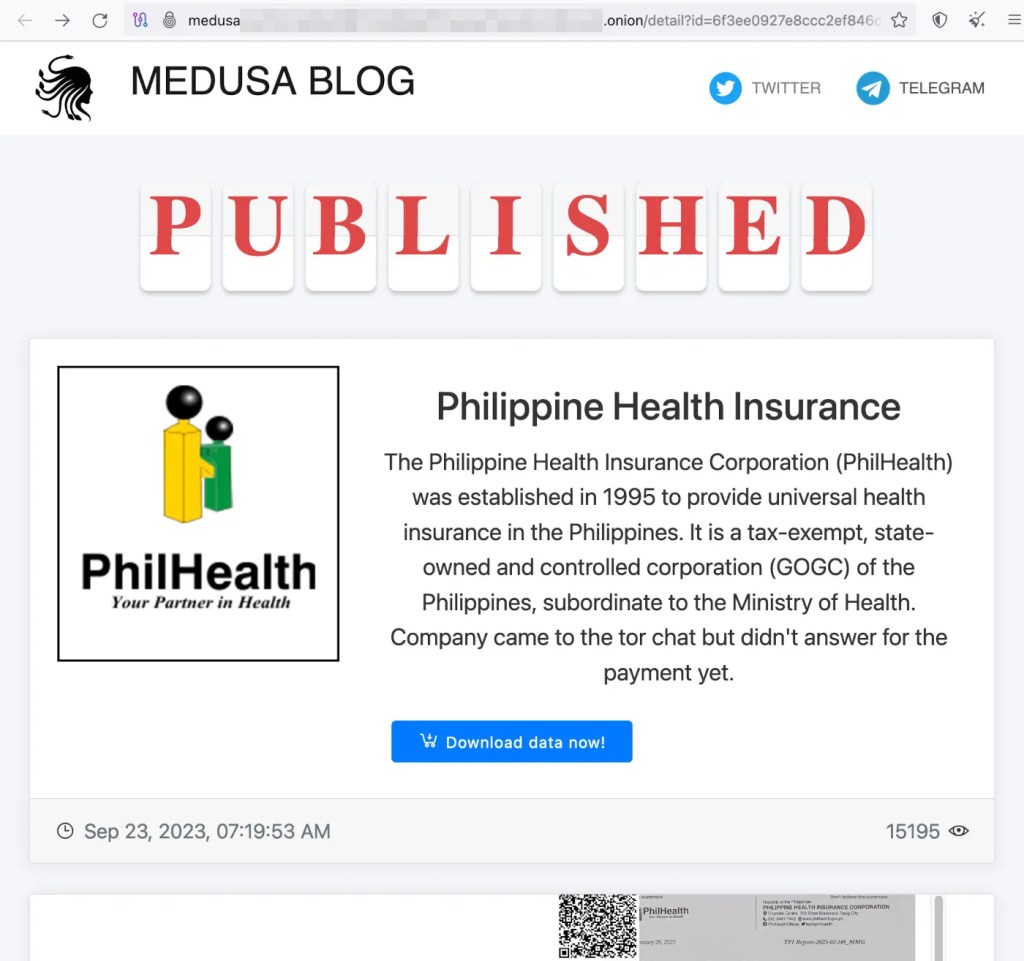
Filipino news site Rappler reports that almost 750 gigabytes of information was stolen from PhilHealth, and the number of PhilHealth members affected is in the “millions”.
Their data is now available for download on the dark web. PhilHealth warns that members are likely to be “victimized by opportunists” who can use the information to create targeted and believable social engineering attacks.
In response, PhilHealth “strongly recommends changing passwords of online accounts, enabling multi-factor authentication, monitoring of suspicious activities in their online accounts, not opening and clicking suspicious emails and links, and not answering suspicious calls and text messages”
The attack is a great example of how ransomware attacks aren’t really about computers, they are about the effects they have on people. Despite expending a lot of hot air on the subject, ransomware groups have shown time and again that they are absolutely not above targeting the healthcare sector. As the attack on Ireland’s Health Service Executive in 2021 showed, attacks on healthcare can create uncertainty, delays, enormous stress and legal jeopardy for staff, and the very real risk of pain, physical harm and even death for patients.
In the twelve months between October 2022 and September 2023, there were 213 known attacks against the healthcare sector, making it the ninth most attacked sector globally. More than half of those attacks occurred in the USA, where healthcare was the third most attacked sector, suggesting it may be targeted deliberately in the USA rather than opportunistically.



