
Fake Booking.com emails target hotels
A new phishing campaign is using a famous brand to compromise hotels.
A new phishing campaign is using the Booking.com brand to target hotels, using fake Captcha websites. The attack begins with cybercriminals sending a fake Booking.com email to the hotel’s email address, asking them to confirm a booking.

If the hotel staff go to the URL in the email, they are greeted by a website with a fake CAPTCHA popup asking them to prove they are a human.
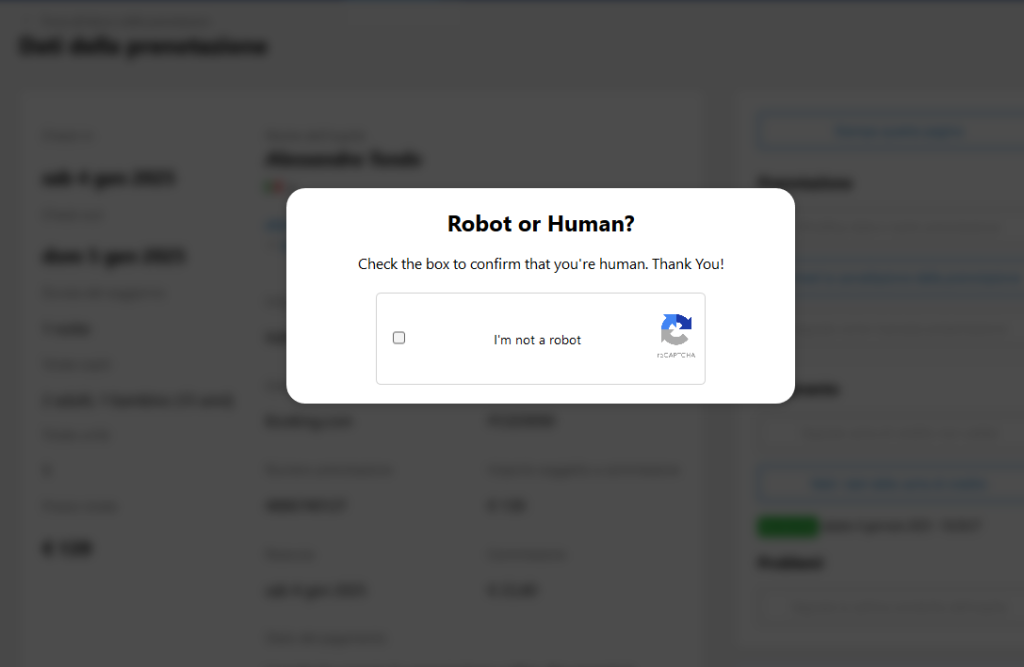
Behind the scenes, the website has loaded a malicious mshta command into the user’s clipboard.
When they tick the CAPTCHA checkbox, the target is asked to complete a set of “Verification Steps”.
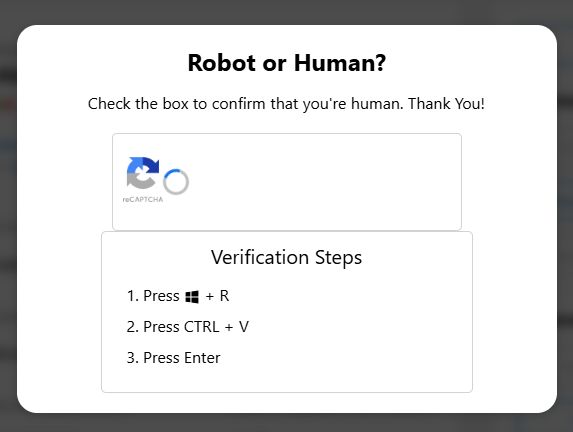
What the instructions actually do is paste the contents of the clipboard into a Windows command prompt and run it, which runs the mshta command that fetches and runs a remote file, setting off an attack chain that ends with the hotel’s systems being infected with a Trojan.
A compromised hotel network is a significant prize for cybercriminals, potentially offering access to payment details and other personal data that can be abused or sold.
How ThreatDown can help you
Even staff who have been trained to check that email senders are valid and that to avoid links in emails will slip up from time to time, and a range of technologies can blunt the impact when they do.
- ThreatDown DNS filtering can block access to malicious sites and disrupt communication to command and control servers.
- ThreatDown Application Block can block scripting engines like mshta, disrupting the attack chain.
- Endpoint Detection & Response (EDR) can detect and neutralise threats like Trojans.
IOCs
Domains used in this campaign:
- vencys[.]com, appears in the email and redirects to the CAPTCHA site.
- bokcentrpart[.]com, hosts the fake CAPTCHA site.
- captpart[.]info, the site the malware is downloaded from.



