
“Enhanced Bonus” QR code phish steals Microsoft credentials
A personalized phishing attack could lead to a catastrophic loss of credentials.
Phishing continues to be a major headache for organizations because organizations continue to use email for important and interesting things, like discounts, security alerts, and invoices. And people continue to be interested in the things that people are interested in, like discounts, security alerts, and invoices.
And of course there’s little that’s more interesting to paid employees than salaries and bonuses, and the phishers know that too.
In the case of this phish, the target received an email with an attachment that looks like it came from a company HR department—hooking them with the promise of an “enhanced bonus”.

[Organization’s name] Enhanced Bonus Distribution Strategy
Your attention to the document provided by the Human Resources/Payroll Department is requested.
Date: Friday February 2025
Scan the QR code below with your smartphone camera for easy access to the document review.[QR code]
Please refrain from sharing this email, as it includes a secure link to our SharePoint platform. We appreciate your cooperation in maintaining security and confidentiality by not disclosing this link or its access code to others.
Your email: [employee.name@organization.country]
The phishing attempt looks very personalized because both the attachment name and the URL the QR code leads to include the target’s email address:
- The name of the attachment was [email-address]-Employee-Handbook-6384.pdf.
- The QR code leads to https://qn.s19pk[.]com/FEDn6OrqfXLcYxwKzcc/#X[email-address]
After scanning the QR code and passing a Cloudflare bot protection screen, the target is taken to a fake Microsoft login screen.
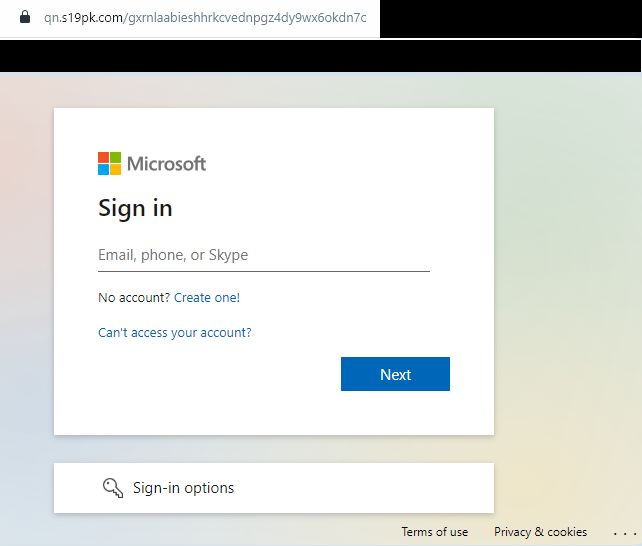
We removed the email address from the URL we used, to avoid alerting the attackers, but we suspect that if we used the unmodified URL the email address would be pre-filled in the login screen.
Intriguingly, clicking the “next” button only works if you enter a corporate email address, otherwise the phishing site comes back with the message “We couldn’t find an acount with that username. Try another or get a new Microsoft account.”
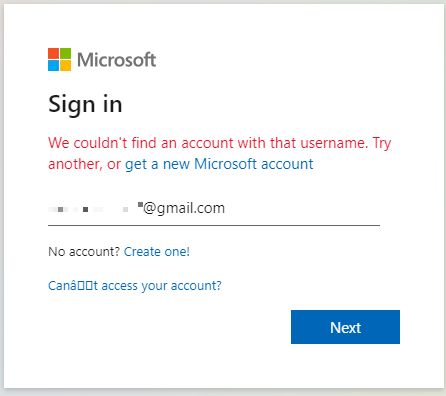
If the target enters a corporate email address they are asked for their password.
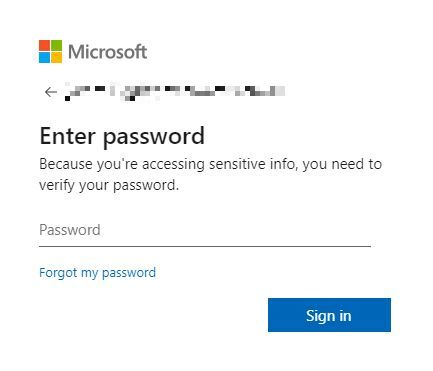
Twice.
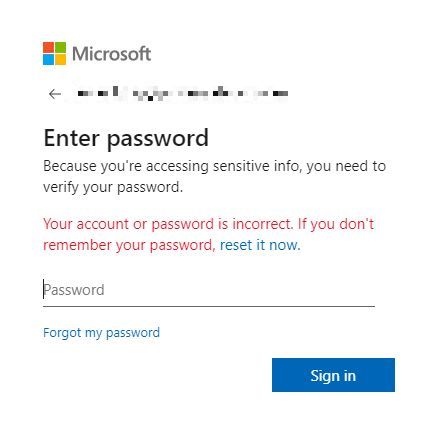
On the second attempt, the site accepts the password, and the data is sent to http://ysl3zzdmfwncbktqtvx2aosnxo8zxyeflmphszset0akvfaxrv.ecshag[.]ru.
With Microsoft 365 credentials, attackers can gain access to sensitive corporate data, including emails, documents, and internal communications. Company login credentials can also give attackers a foot in the door of an entire company network—which can be used to steal data, escalate attacks, and even launch ransomware attacks.
Attackers use QR codes because they are more likely to make it past email filters, and may evade company security software if the target’s phone isn’t covered by an EDR solution.
IOCs
Some domains you can block with ThreatDown DNS filtering:
Main phishing site
qn.s19pk[.]com
Receiving domain for the credentials
ecshag[.]ru
Redirects
wh5nbx.revishbos[.]ru
o3mfqg.warthydri[.]ru
cemh.urj7zq[.]com
8kbxy.adlijari[.]ru
98oj4s.drogdordr[.]ru
cyt4.drogdordr[.]ru



