
Day in the life of a ThreatDown MDR analyst: Stopping a live ransomware infection
Walk through a ransomware infection from the POV of an MDR analyst.
With ransomware attacks reaching all-time highs in 2023, the ability to find and weed out network intruders—known as detection and response—is more important than ever. But what does detection and response actually look like in action?
The ThreatDown Managed Detection and Response (MDR) team has the answers. With over 100 years of combined cybersecurity experience at places like the US military and Sony, the ThreatDown MDR team have mastered the art of detection and response.
In this article, we walk you through tackling a ransomware infection from the POV of a ThreatDown MDR analyst. Let’s dive right in to it.
Step 1: Detecting the suspicious activity
In the MDR portal, we can see a case has been created for the suspicious activity relating to an unusual executable.
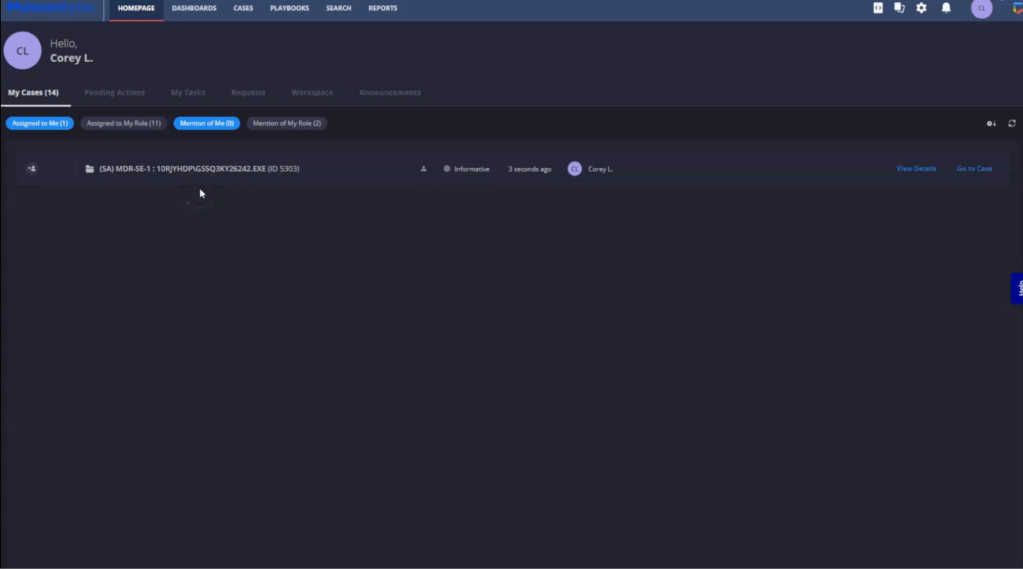
This case involves two alerts and incorporates the Suspicious Activity playbook. ThreatDown generate alerts for suspicious activity using a heuristic approach, focusing on system behaviors that could indicate malicious intent.
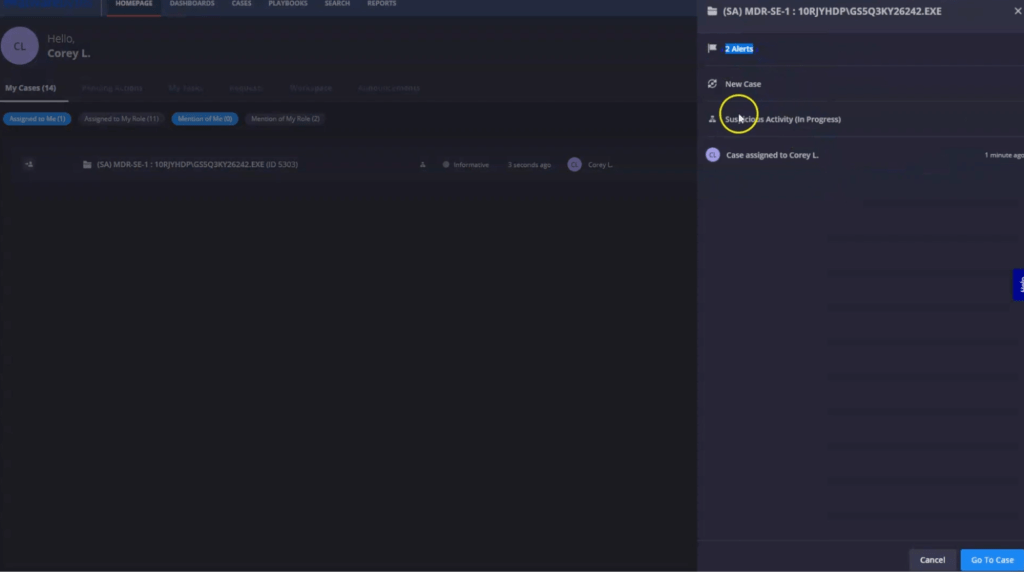
To investigate further, we will delve into the case details.
By reviewing the alert overview, we aim to highlight anything that stands out. Here, we can see Netsh was used to delete firewall rules. We also see PowerShell being invoked, its execution policy being set to bypass, and a base64 encoded command being executed.
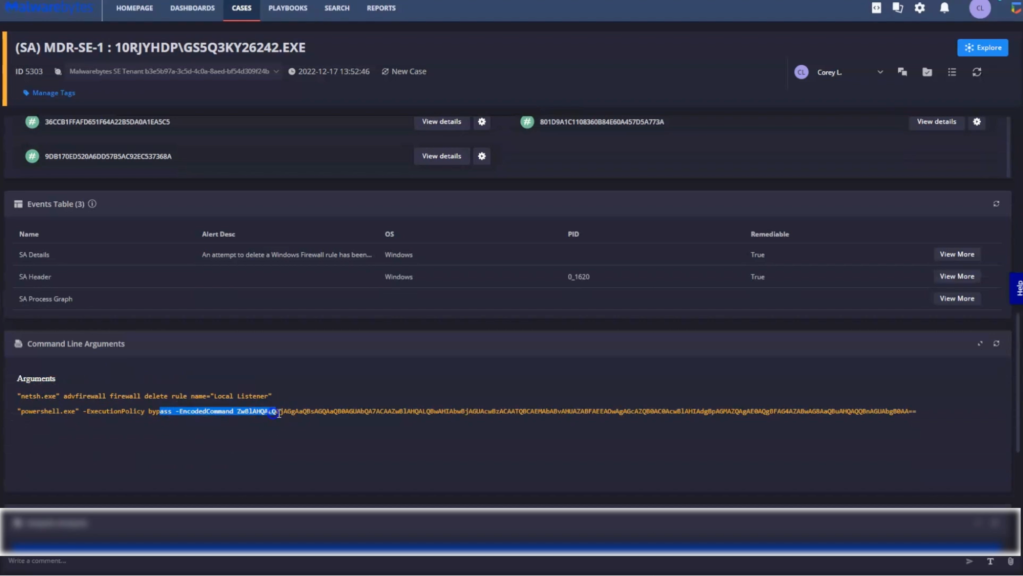
Step 2: Digging further into the investigation
In the events tab, we have a lot more data which will provide further insight into this investigation. The events tab provides us with a wealth of data for deeper insight.
We observe PowerShell being used again, alongside system enumeration tools like systeminfo.exe, whoami.exe, netstat.exe, and ipconfig.exe being executed, which clearly indicates the malware’s intent to gather system information for potential exploitation or exfiltration. The invocation of netsh.exe to manipulate firewall rules further supports our suspicions.
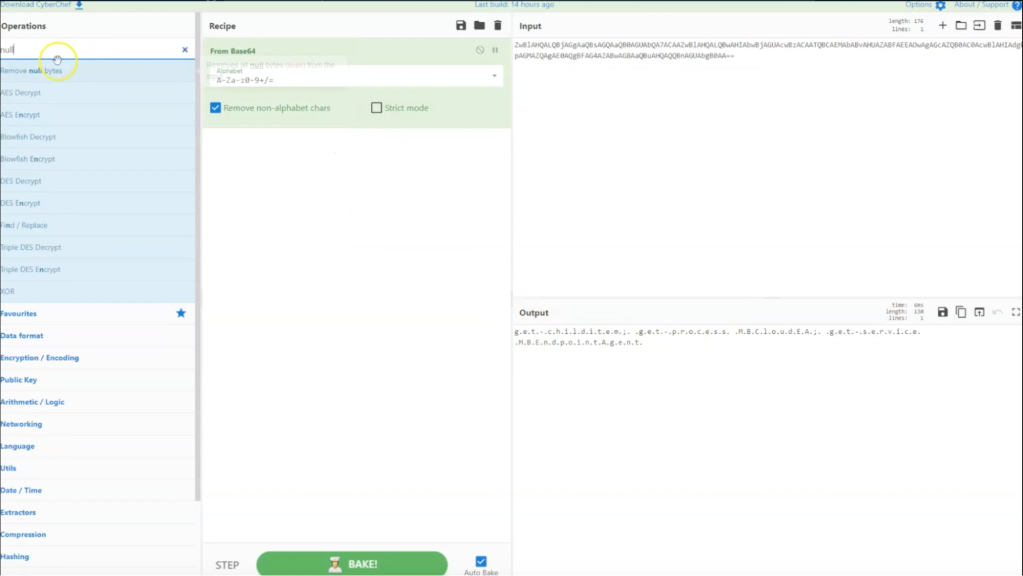
We uncover additional detection rules in the SA details event data that corroborate our initial findings. By analyzing the Base64 encoded string in CyberChef, we make the text readable, enhancing our understanding.
Step 3: Exploring the malicious file’s execution
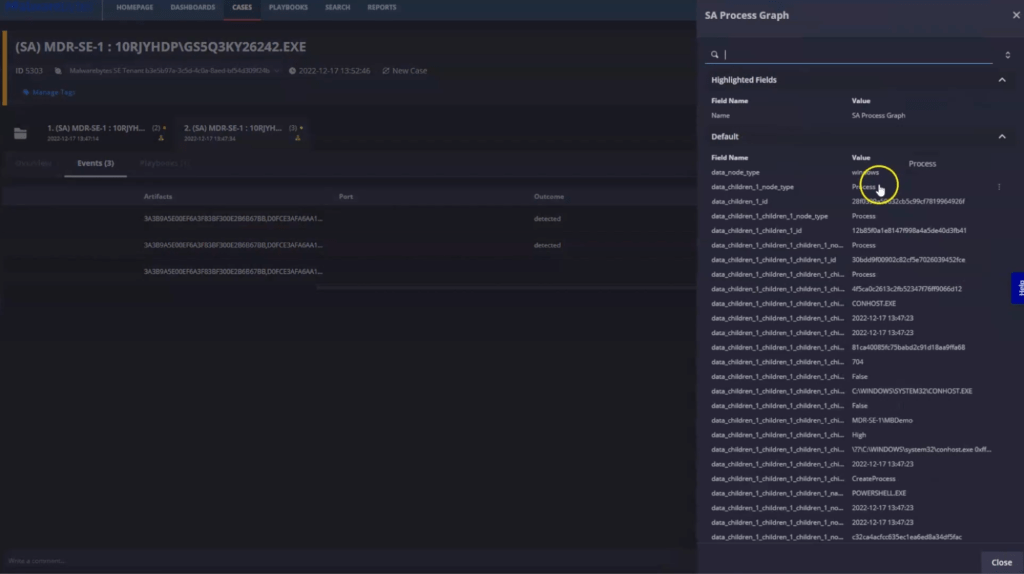
Pivoting to the customer’s Nebula environment, we explore a process graph that outlines the sequence of activities starting from the malicious file’s execution.
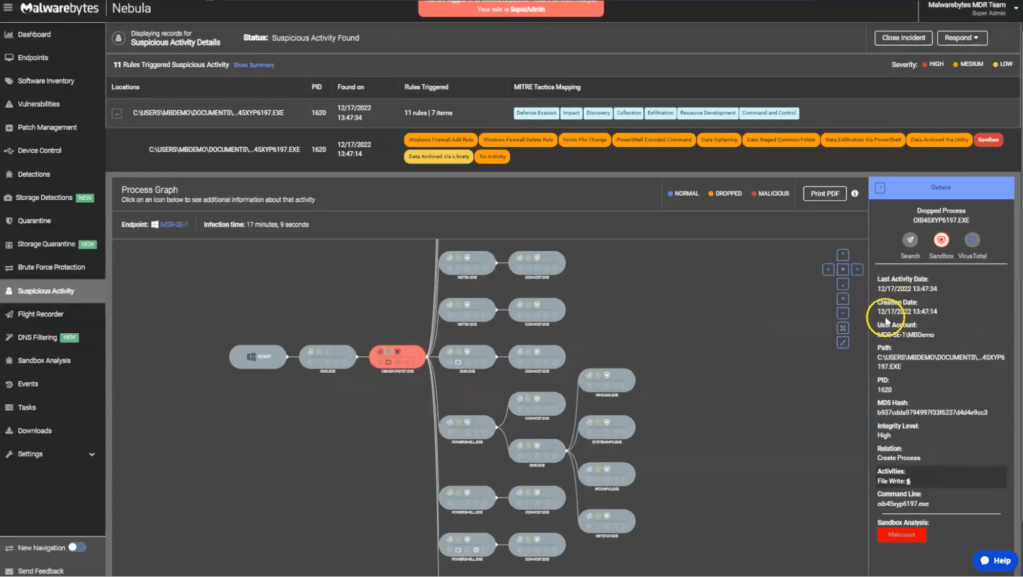
The process details for this malicious executable reveal crucial information such as the last activity date, creation date, path, PID, hash, and command line. We also note suspicious activities post-execution, including six file writes.
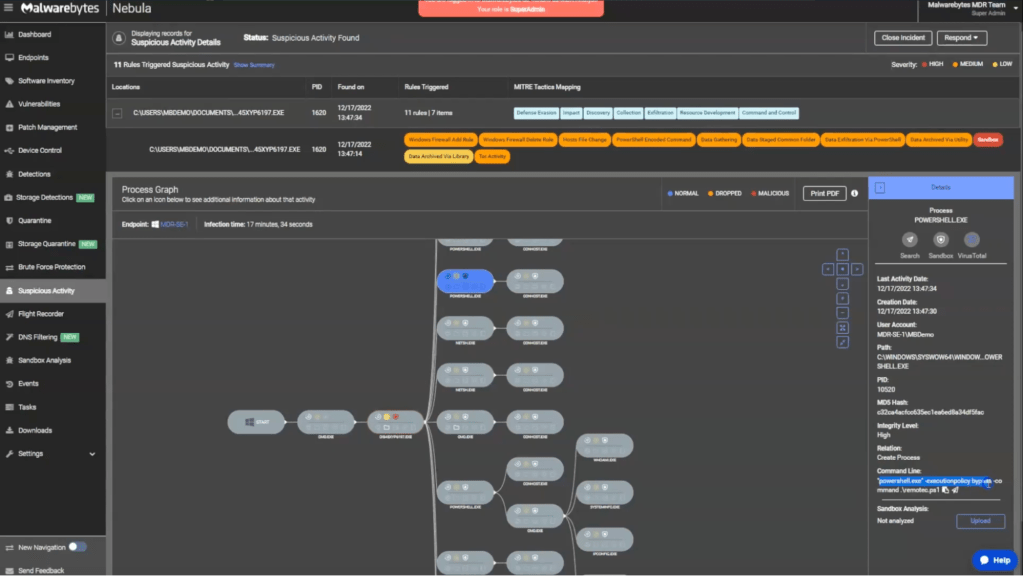
When examining the PowerShell process initiated by the malicious file, we find it set to bypass execution policies for executing remotec.ps1. Another PowerShell instance shows system enumeration activities and the execution of racoon.ps1, which triggers running native Windows utilities for system information gathering.
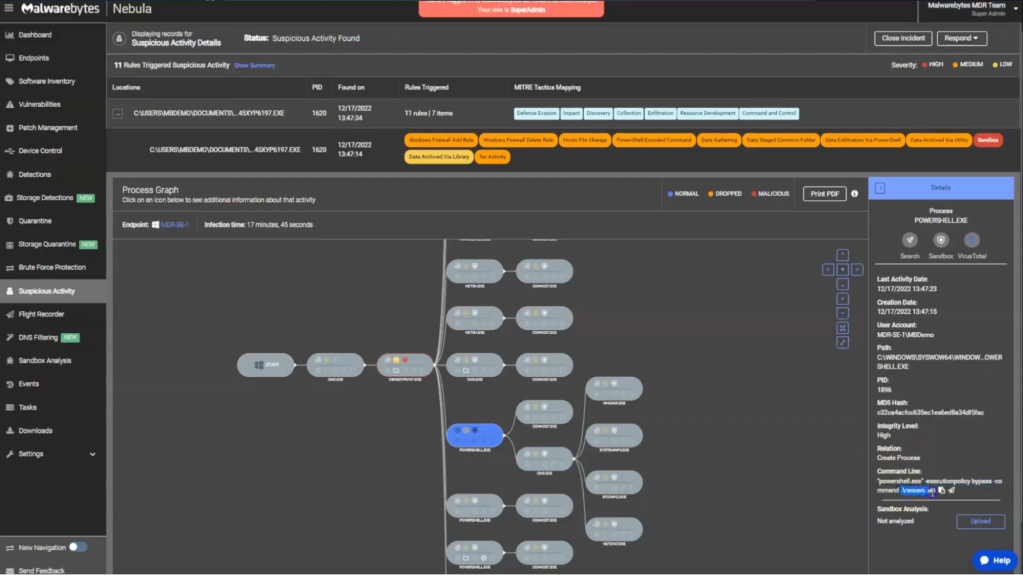
We also highlight detection rules triggered during this incident, providing insight into the detected activities on the endpoint, such as modifications to firewall rules and host files, indicative of exfiltration attempts.
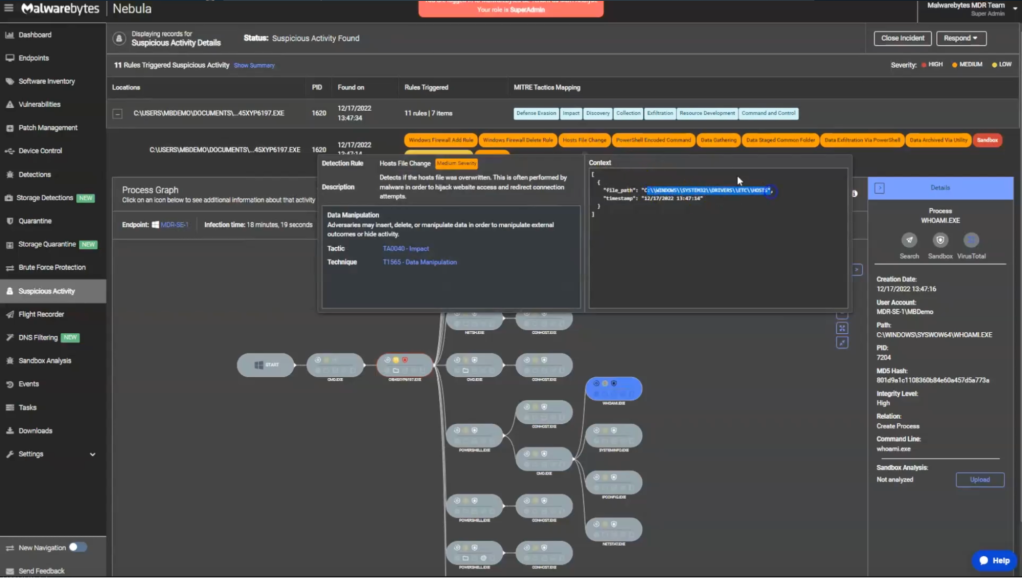
Within the PowerShell script, we identify several actions related to data gathering and exfiltration:
- Creating a variable pointing to an exfiltration path.
- Running whoami, systeminfo, ipconfig, and netstat, directing outputs to a text file.
- Copying the sysinfo.txt file to a designated folder.
- Compressing collected data into a zip file for exfiltration.
- Executing an HTTP post request to transfer data to external servers, hinting at double extortion.
- Cleaning up the exfiltration folder and removing malicious scripts.
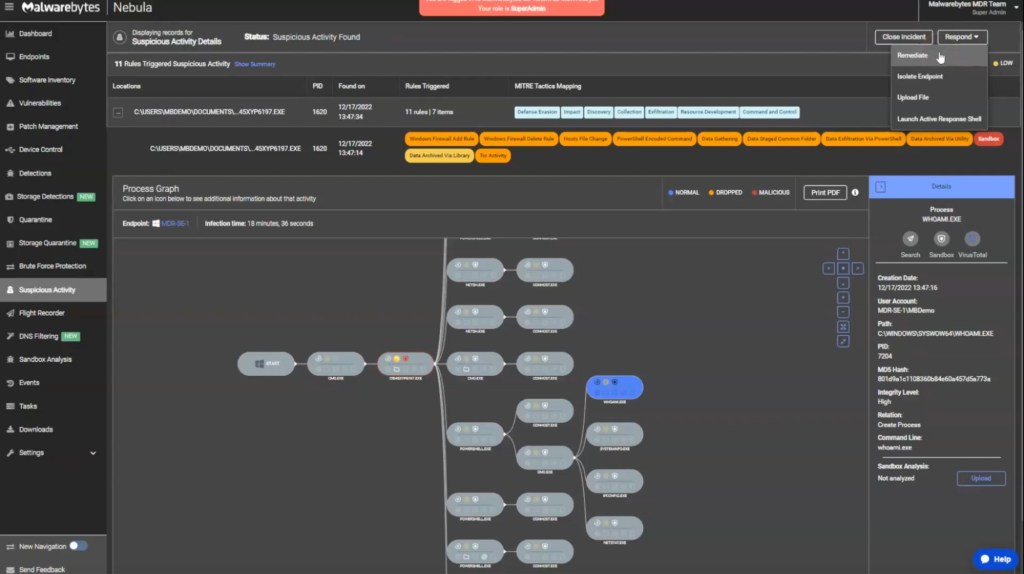
Step 4: Isolating the endpoint and rolling back chagnes
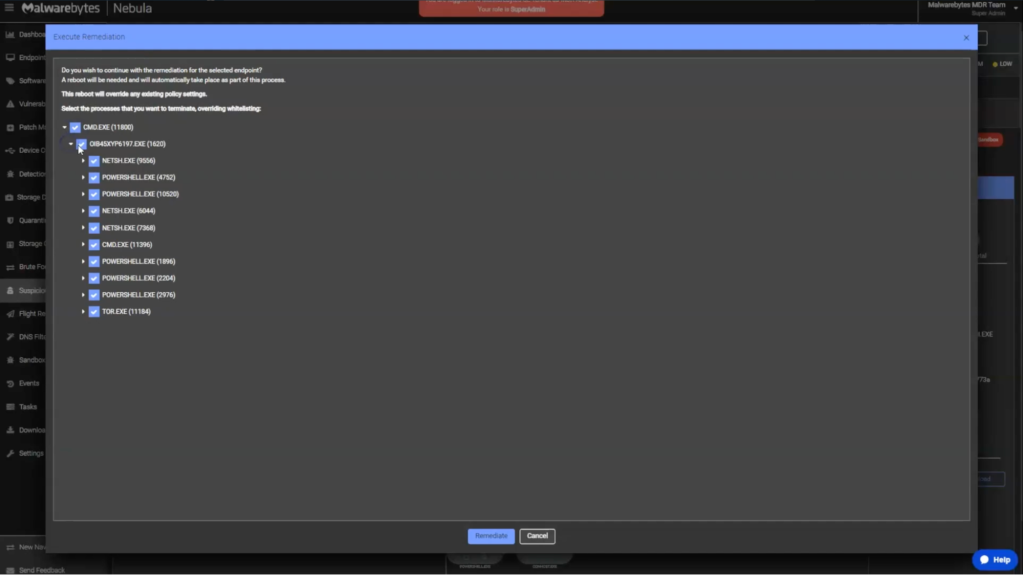
We can isolate the infected endpoint to prevent further spread and initiate remediation processes, including ransomware rollback to restore the endpoint to its pre-infection state.
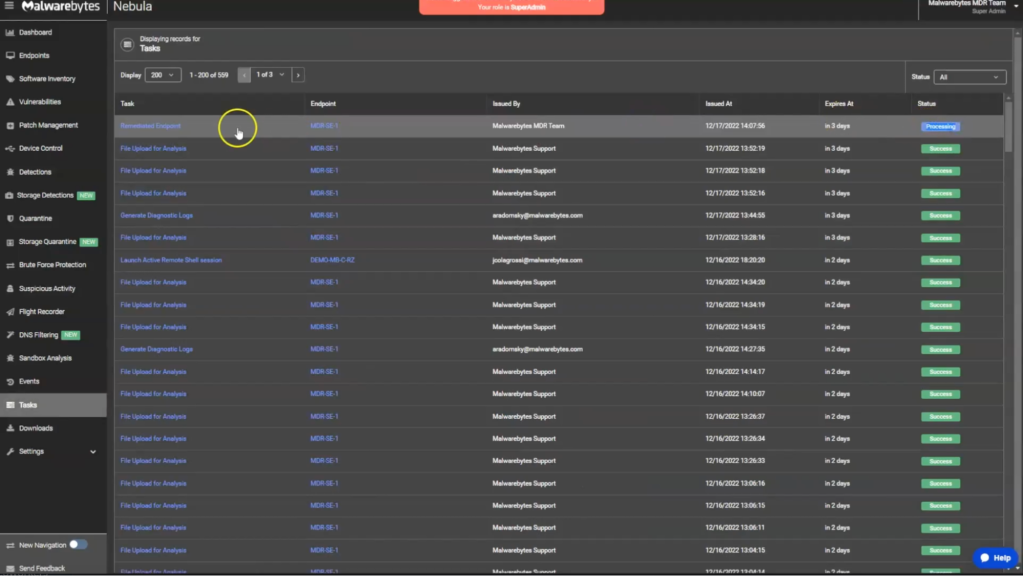
Upon remediation, we create a task to track the status and the processes being addressed.
Examining the victim’s machine, we observe a ransom note and files with a .encrypted extension, inaccessible without a ransom payment.
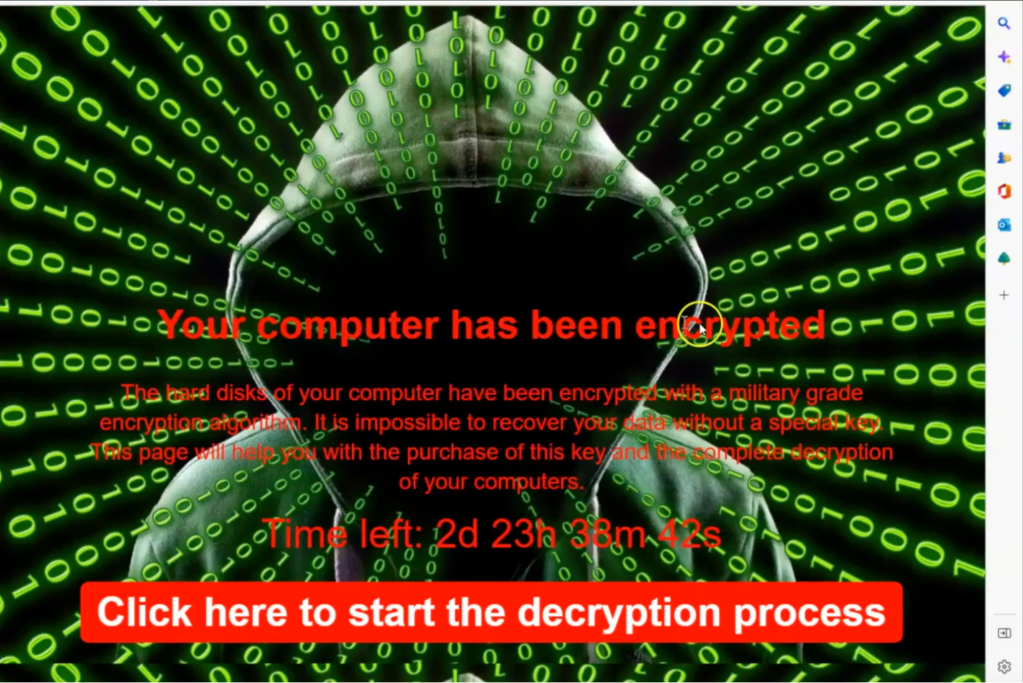
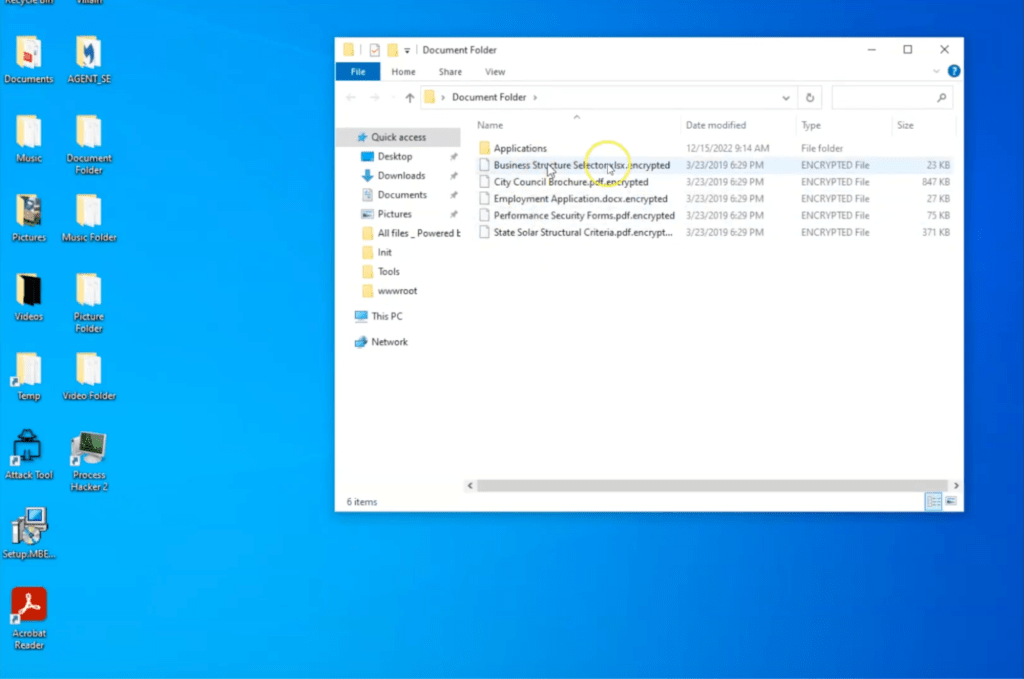
Going back to the MDR portal, we are confident that this is a ransomware attack based on our evidence. The next steps would be to set the priority of the case to critical and to mark the case as an incident. We can then notify the customer via the case wall and provide recommendations.
Checking back on the remediation task status, we can see the status is now set to success, indicating the remediation is complete.
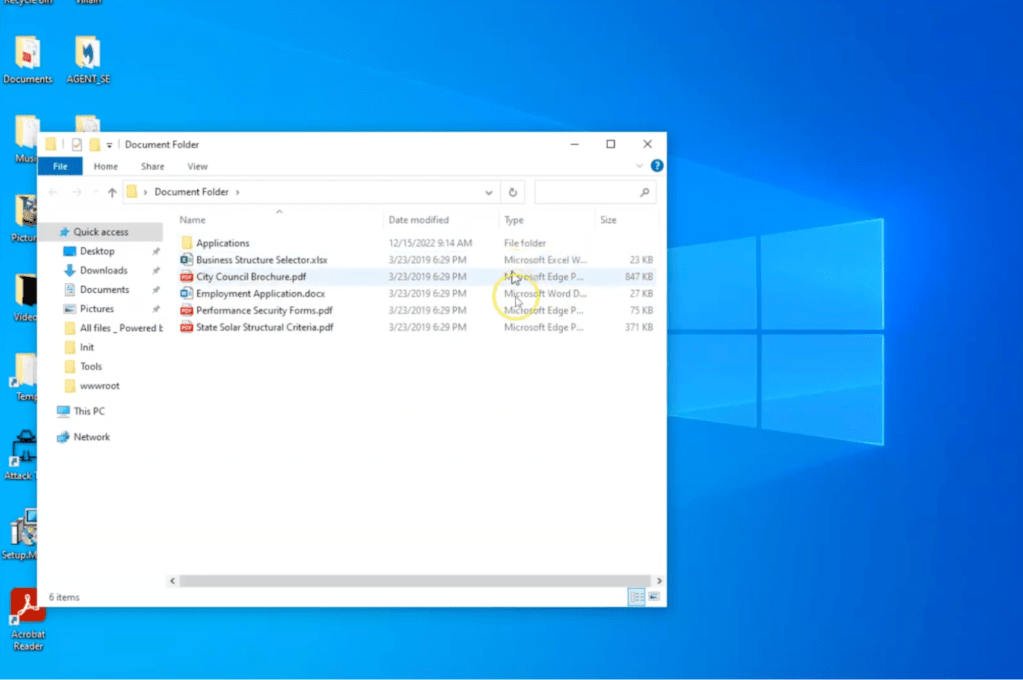
Pivoting back to the victim machine, we can see the ransomware rollback was successful, and the endpoint is no longer infected. The user’s data is no longer encrypted.
The ThreatDown MDR difference
From the initial alerts to the intricate analysis of suspicious activities and the execution of a successful remediation strategy, this walkthrough showed the steps ThreatDown MDR takes to stop ransomware in its tracks and save client data.
The team’s ability to isolate the infected endpoint, analyze malicious scripts, and rollback the ransomware to restore the affected systems highlights their comprehensive approach to detection and response, ensuring that all traces of an attack are erased during remediation.
ThreatDown MDR is available as part of our Elite and Ultimate Bundles, which combines the technologies and services that resource constrained IT teams need into four holistic, cost-effective packages. Learn more.



