
Fake CrowdStrike hot fix leads to Remcos Trojan
To nobody’s surprise, cybercriminals are abusing the CrowdStrike outage.
Cybercriminals, being the opportunists they are, love to monetize other people’s misfortune.
Following Friday’s global Windows outage, which saw machines around the world unable to boot and displaying the infamous “blue screen of death” (BSOD) because of a faulty CrowdStrike update, we have seen a huge number of new CrowdStrike-themed domain names being registered, as well as cybercriminals trying to take advantage of the company’s name in other ways.
Some of the domains are being registered by legitimate companies posting websites offering technical support in difficult times, some have been left unused, and some are being used by people who get paid for clicks. No doubt some will be used for malvertising.
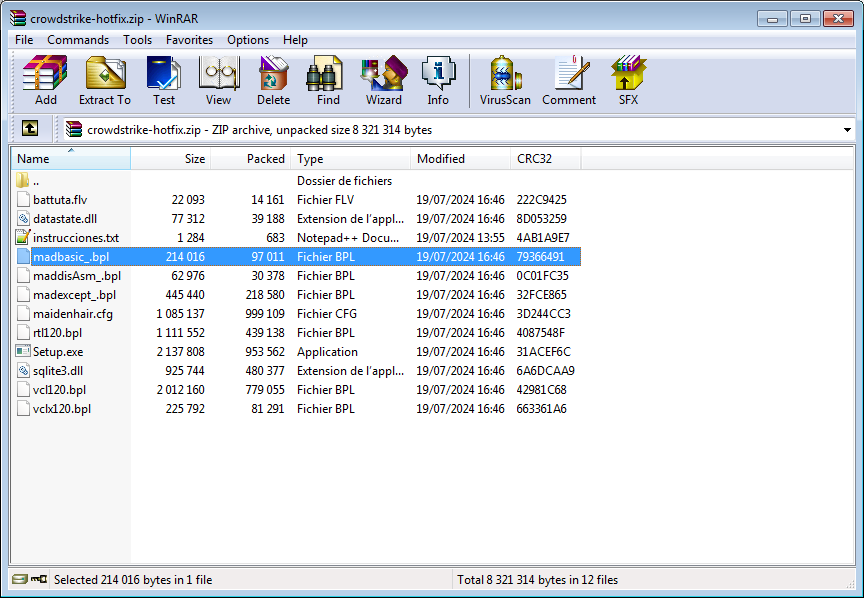
Cybercriminals are also abusing the CrowdStrike name in malicious emails. One of the opportunistic campaigns ThreatDown has seen used an email with instructions for applying a patch for the CrowdStrike issue, accompanied by an attachment with the deceptive name crowdstrike-hotfix.zip.
The filenames in the zip archive were familiar to our researchers, who recognized them immediately—they have previously been used in a campaign that bundled a legitimate file with a set of malicious PowerShell commands that download and install the Remcos Trojan.
The Remcos Trojan is a Remote Access Trojan (RAT) that can be used to fully control and track the activity of any affected Windows computer. It provides administrator privileges, a keylogger, and other methods to collect information about the victim and their computer, which makes it possible for an attacker to drop additional malware, like ransomware.
Usually, it’s spread in email campaigns that have a malicious zip disguised as a PDF file. Making it look like a fix for the CrowdStrike BSOD is a quick and dirty adaptation to the current news cycle.
Remcos is hard to detect because it hides its code inside a legitimate process by using process injection methods, like process hollowing. Process hollowing is a technique where malware suspends a legitimate, running process and replaces the memory occupied by that process with malicious code.
Other researchers have reported CrowdStrike-related tech support scams, and destructive wiper malware.
As Crowdstrike CEO George Kurtz said:
I encourage everyone to remain vigilant and ensure that you’re engaging with official CrowdStrike representatives. Our blog and technical support will continue to be the official channels for the latest updates.
And this is not only true for this incident. Many worldwide events, good or bad, are used by cybercriminals to pique victims’ interest and get them to allow or perform an action they wouldn’t otherwise do.



