
Configuring the Windows firewall
Show of hands—How many of you have heard someone say something like this: “You don’t need an extra firewall. The one that comes with Windows is sufficient for home users”. While this may be true for the default settings when it comes to protection, how many who have heard this remark are able to check which programs have added themselves to the list of allowed programs?
Find the settings
Let’s take a look.
You can find the settings for the Windows firewall under Control Panel > System and Security > Windows Firewall > Allow a program or feature through Windows Firewall.
Despite the title “Allow a program or feature …”, this is also the place where you can remove them from the list of allowed programs and features.
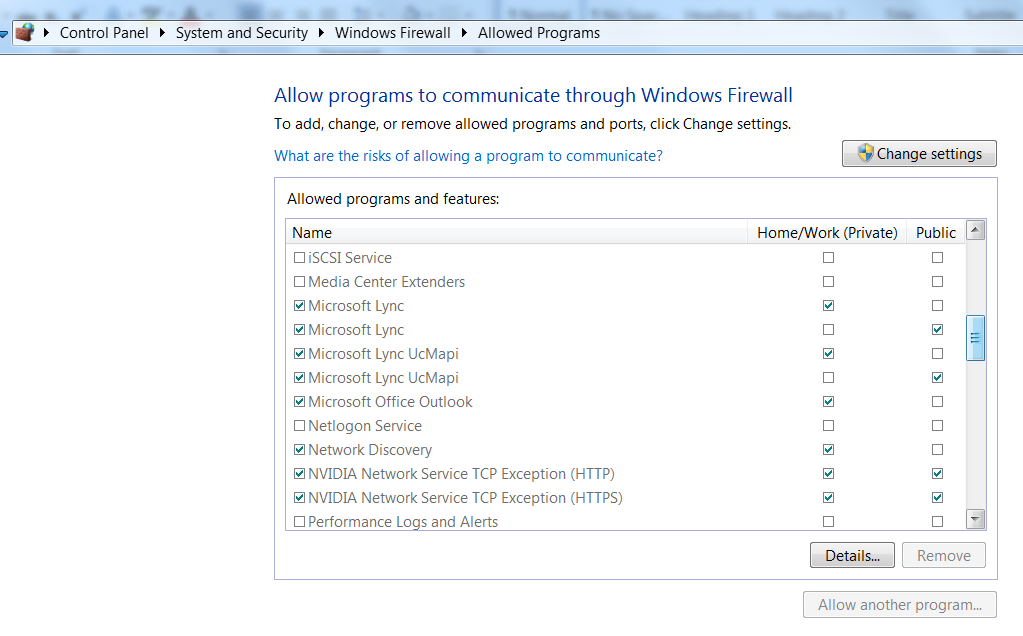
The method above can be rather painstaking, especially if you have a large amount of programs installed. Not to mention all the (undoubtedly) confusing names. Malware authors are sometimes counting on our reluctance to disable anything made to look like it’s related to Microsoft, Windows, or Internet Explorer. “Who knows what will stop working if I disable that?”
An easier way to check
To make it a little easier, you can use a program that makes a log and uses whitelisting, so all you have to do is take a look at the remaining entries. One such program which is very popular at many tech help forums is FRST. If you download FRST (make sure to get the right version) and run it, make sure there is a tick in the “Addition.txt” field if you want to look at the firewall section.
Once “FRST.txt” and “Addition.txt” are ready, you will be prompted. Click OK on both prompts, and the logs will be saved in the same folder as “FRST(64).exe”.
A typical firewall related section of FRST will look like this:
==================== FirewallRules (Whitelisted) ===============
(If an entry is included in the fixlist, it will be removed from the registry. The file will not be moved unless listed separately.)
FirewallRules: [{3297B962-0770-4831-890E-FEF6510610E4}] => (Allow) C:Program FilesNewsbinnewsbinpro64.exe
FirewallRules: [{8D2A05D2-99CF-487E-A1B9-F8564A86F6A2}] => (Allow) C:Program FilesNVIDIA CorporationNvStreamSrvnvstreamer.exeFirewallRules: [{E5055742-8397-4AFB-BDD9-DF9CFB3B2C4E}] => (Allow) C:Program FilesNVIDIA CorporationNvStreamSrvnvstreamer.exe
FirewallRules: [{64DC59A3-D99D-4926-8010-A4006CC83EC1}] => (Allow) C:Program FilesNVIDIA CorporationNvStreamSrvnvstreamsvc.exeFirewallRules: [{AD102C3A-3D40-4A47-9483-AB5C8FC40D25}] => (Allow) C:Program FilesNVIDIA CorporationNvStreamSrvnvstreamsvc.exe
FirewallRules: [{06100084-A816-405E-B3E8-965FD63E1B8F}] => (Allow) C:Program Files (x86)NVIDIA CorporationNetServiceNvNetworkService.exeFirewallRules: [{8B8C1A5C-20E0-4B64-BC6B-705C4B002763}] => (Allow) C:Program Files (x86)NVIDIA CorporationNetServiceNvNetworkService.exe
FirewallRules: [UDP Query User{1D2F5D5C-673D-4480-A385-C362D7BE39F7}C:program files (x86)skypephoneskype.exe] => (Allow) C:program files (x86)skypephoneskype.exeFirewallRules: [TCP Query User{16301F9C-A2E7-4758-894D-18B300A6E0F9}C:program files (x86)skypephoneskype.exe] => (Allow) C:program files (x86)skypephoneskype.exe
FirewallRules: [{47F0B7D0-D0EA-403F-9D8B-0A1F92E5E84E}] => (Allow) C:Program FilesMicrosoft OfficeOffice15UcMapi.exeFirewallRules: [{88724164-66B1-4D9B-97BD-76BDBD486E3F}] => (Allow) C:Program FilesMicrosoft OfficeOffice15UcMapi.exe
FirewallRules: [{2A926726-D200-4CAD-9A56-7D6B10516B53}] => (Allow) C:Program FilesMicrosoft OfficeOffice15lync.exeFirewallRules: [{CAE1A4B8-4C29-4929-A508-D2B2D89AFEAA}] => (Allow) C:Program FilesMicrosoft OfficeOffice15lync.exe
FirewallRules: [{1AB7A511-8CC3-4032-936D-6E6121445CF5}] => (Allow) C:Program Files (x86)RelevantKnowledgerlvknlg.exeFirewallRules: [{5B7AD292-902A-44BE-A6F1-E276DC1E4E89}] => (Allow) C:Program Files (x86)RelevantKnowledgerlvknlg.exe
FirewallRules: [{854E69F5-896D-4BF9-A5EB-F1C645E8EBD1}] => (Allow) C:Program Files (x86)Mozilla Firefoxfirefox.exeFirewallRules: [{006610CB-49E1-4F19-BB70-783191B21F91}] => (Allow) C:Program Files (x86)Mozilla Firefoxfirefox.exe
If you need help analyzing one of these logs, we recommend asking for help on our forums.
Malware adding allowed programs
So, if it’s so difficult to find and get rid of unwanted entries, it must be really hard to add one, you might think. Unfortunately, that’s not true. If a program is run elevated—with Administrator privileges—all it has to do is run a command like the example below:
netsh firewall add allowedprogram "C:Users{username}AppDataRoamingTr.exe" "Tr.exe" ENABLE
This example is taken from a Trojan that runs this command to grant itself internet access. After which, it downloads additional malware. Of course, this is not only true for malware. Every program and installer that runs elevated has the ability to add programs to the “Allowed” list, which is exactly the reason why we recommend regular checks to see which programs are allowed if you are relying on the Windows firewall alone. Some might argue that this is true for every firewall, and they would be right in my book. It never hurts to check your firewall settings, certainly not after cleaning up an infection.
Conclusion
While the built-in Windows firewall may offer adequate protection, this is only true if you check the settings on a regular basis, and certainly immediately after removing an infection.
Links
Pieter Arntz



