
Citrix Bleed widely exploited, warn government agencies
In a joint cybersecurity advisory, the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI), along with other international agencies, warn that ransomware gangs are actively exploiting the Citrix Bleed vulnerability.
Affiliates of at least two ransomware groups, LockBit and Medusa, have been observed exploiting Citrix Bleed as part of attacks against organizations. Both are globally significant, and were ranked as the first and sixth most active groups in our November ransomware review.
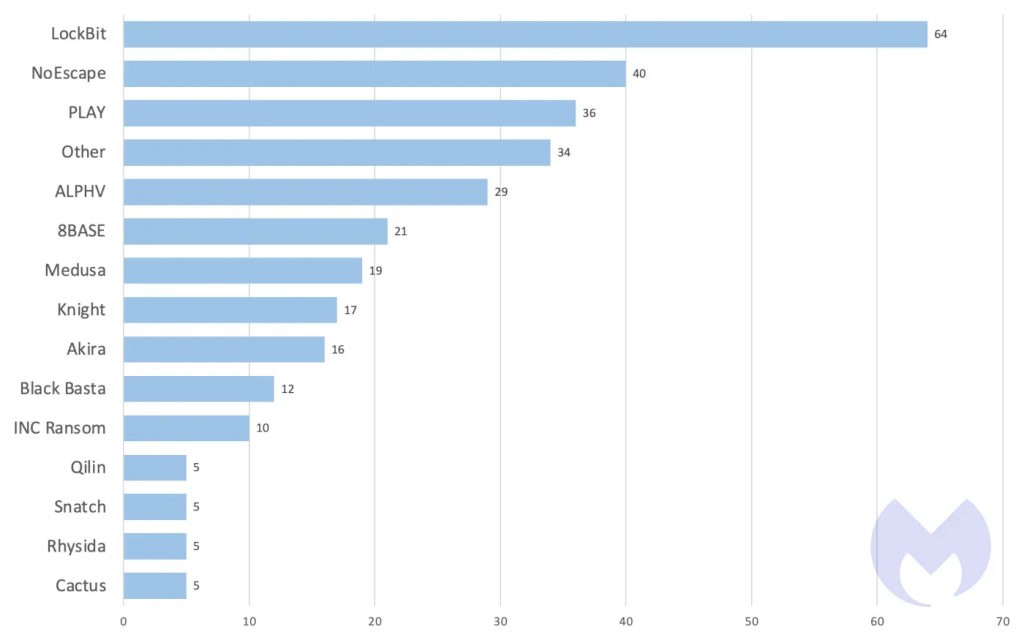
Known ransomware attacks by ransomware group, October 2023
Mandiant states it is currently tracking four distinct uncategorized groups involved in exploiting this vulnerability.
The Common Vulnerabilities and Exposures (CVE) database lists publicly disclosed computer security flaws. The CVE for the vulnerability known as Citrix Bleed is CVE-2023-4966 (CVSS score 9.4 out of 10). The vulnerability is described as a sensitive information disclosure in NetScaler web application delivery control (ADC) and NetScaler Gateway when configured as a Gateway (VPN virtual server, ICA Proxy, CVPN, RDP Proxy) or AAA virtual server.
The vulnerability provides attackers with the capability to bypass multi-factor authentication (MFA) and hijack legitimate user sessions, and is said to be very easy to exploit. It’s reported to have been in use as a zero-day since late August. On October 10, 2023, Citrix released security updates to address CVE-2023-4966 along with another unrelated vulnerability giving organizations the chance to patch for the vulnerability.
The following supported versions of NetScaler ADC and NetScaler Gateway are affected by the vulnerability:
- NetScaler ADC and NetScaler Gateway 14.1 before 14.1-8.50
- NetScaler ADC and NetScaler Gateway 13.1 before 13.1-49.15
- NetScaler ADC and NetScaler Gateway 13.0 before 13.0-92.19
- NetScaler ADC 13.1-FIPS before 13.1-37.164
- NetScaler ADC 12.1-FIPS before 12.1-55.300
- NetScaler ADC 12.1-NDcPP before 12.1-55.300
NetScaler ADC and NetScaler Gateway version 12.1 are now End-of-Life (EOL) and also vulnerable. Customers using Citrix-managed cloud services or Citrix-managed Adaptive Authentication products are not impacted.
The advisory provides Tactics, Techniques and Procedures (TTPs) and Indicators of Compromise (IoCs) obtained from FBI, the Australian Cyber Security Centre (ACSC), and voluntarily shared by Boeing. Boeing observed LockBit affiliates exploiting CVE-2023-4966, to obtain initial access to Boeing Distribution Inc., its parts and distribution business that maintains a separate environment.
Besides patching, CISA encourages organizations to assess Citrix software and their systems for evidence of compromise, and to hunt for malicious activity. If compromise is suspected or detected, organizations should assume that threat actors hold full administrative access and can perform all tasks associated with the web management software as well as installing malicious code.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.



