
Black Basta ransomware affiliates use Quick Assist to target users
Cybercriminals are using the Quick Assist remote assistance tool to deliver ransomware.
The Microsoft Threat Intelligence Team has observed a group of cybercriminals it calls Storm-1811, abusing Quick Assist in attacks that lead to Black Basta ransomware.
Quick Assist is an application that enables you to share your Windows or macOS device with another person remotely, typically for providing technical support.
Microsoft reports that the cybercriminals call the victim and try to convince them they need technical assistance. The attacker pretends to be a trusted contact, like Microsoft technical support or an IT professional from the target user’s company. During the call, the attacker persuades the user to grant them access to their device through Quick Assist. They use the access gained with Quick assist to quietly establish backdoor access to the machine. Once the call is concluded they use the backdoor access to install Black Basta ransomware.
Only recently, the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), Department of Health and Human Services (HHS), and Multi-State Information Sharing and Analysis Center (MS-ISAC), released a joint Cybersecurity Advisory (CSA) about Black Basta. The advisory reports that threat actors using the ransomware have encrypted and stolen data from at least 12 out of 16 critical infrastructure sectors, including the Healthcare and Public Health (HPH) Sector.
The advisory provides a lot of Indicators of Compromise (IOCs) and Tactics and Techniques related to Black Basta and is worth a read.
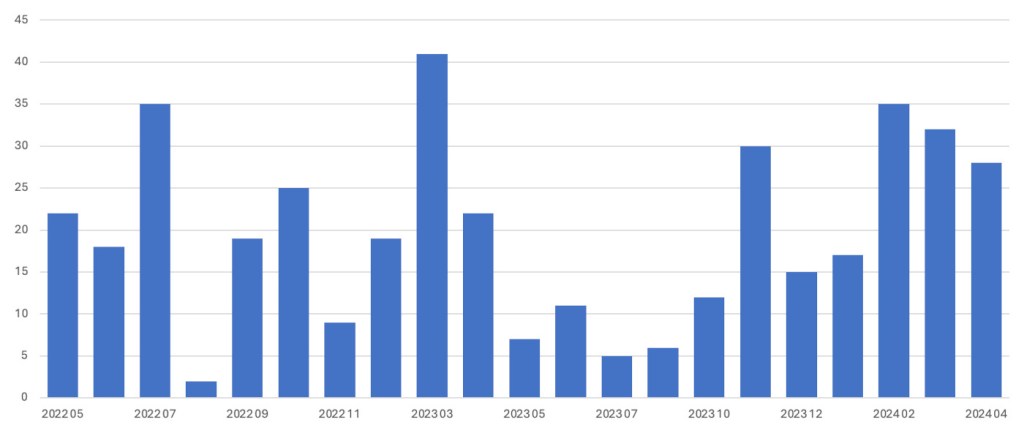
Malwarebytes’ telemetry shows that Black Basta has reported more attacks in the last three months than at any other time in the last two years.
Mitigation
Microsoft says it is investigating the use of Quick Assist in these attacks and is working on improving the transparency and trust between helpers and sharers and incorporating warning messages in Quick Assist to alert users about possible tech support scams.
ThreatDown users can use Application Block to stop unauthorized software from executing on endpoints. This feature is designed to help organizations combat the trend for Living off the Land, where criminals try to avoid detection by using legitimate applications to do their dirty work instead of malware. They are especially fond of remote assistance tools, so users can use Application Block to select remote management tools they don’t use and block them from running in their environment.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.



