
Azure Service Tags vulnerability could allow attackers to access private data
Researchers have found that relying on Azure Service Tags to restrict access to systems is not a secure solution. Microsoft isn’t impressed.
Security researchers at Tenable have published a blog about what they call a vulnerability in Azure, a description that Microsoft denies.
Long story, very short: It’s not a bug, it’s a feature, unless you use it incorrectly.
Tenable points out that it’s possible for an attacker to bypass firewall rules based on Azure Service Tags by forging requests from trusted services.
Azure Service Tags are intended to simplify network isolation. It allows you to group IP ranges and use them to define network security rules. But there is a caveat. Multiple services in Azure allow the customer to craft web requests. Some even allow users to add headers to the request and to change HTTP methods. This is part of the intended functionality of these services.
This feature opens an opportunity for an attacker to have a server-side application make requests to an unintended location, whether internal or external, allowing the attacker, among other options, to reach/expose resources that were previously unreachable.
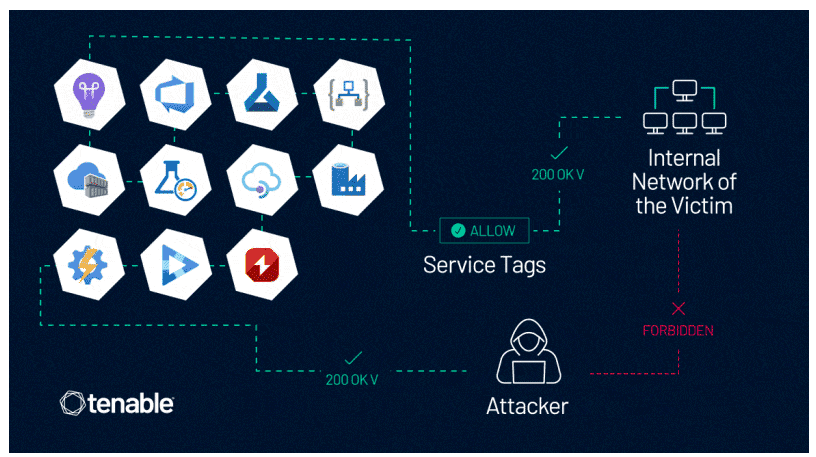
As shown in the diagram above, an attacker which is blocked from direct access can create a workaround in which a service allowed by the Service Tags grants them access to the network of the target.
A service tag represents a group of IP address prefixes from a given Azure service. Microsoft manages the address prefixes encompassed by the service tag and automatically updates the service tag as addresses change, minimizing the complexity of frequent updates to network security rules.
Tenable:
Customers who rely on these firewall rules for security are at risk from this vulnerability. They should take immediate action to mitigate the issue and ensure they are protected by robust layers of authentication and authorization.
Both:
Service Tags are not sufficient to secure traffic to a customer’s origin without considering the nature of the service and the traffic it may send. It is always the best practice to implement authentication/authorization for traffic rather than relying on firewall rules alone.
So, if you’re running:
- Azure DevOps
- Azure Machine Learning
- Azure Logic Apps
- Azure Container Registry
- Azure Load Testing
- Azure API Management
- Azure Data Factory
- Azure Action Group
- Azure AI Video Indexer
- Azure Chaos Studio
And you’re using Azure Service Tags, it’s advisable to search for the use of Service Tags and filter the affected services. To defend these assets, add authentication and authorization layers to them. A list of available Service Tags can be found on this Microsoft site.
As always, it’s important to understand what normal behavior on your network looks like in order to figure out if anything suspicious is going on.


