
ALPHV squeezes victim with dedicated leak site for employees and customers
Threat Intelligence Team
Threat Intelligence Team
Eyebrows were raised this week when the ALPHV ransomware group created a leak site dedicated to just one of its victims. The site was aimed at the employees and guests of a hotelier that had been attacked, and allowed them to see if their personal details had been leaked. The new tactic seems to be designed to create further pressure on the victim to pay the ransom.
The ransomware-as-a-service (RaaS) group ALPHV, also known as BlackCat and Noberus, is currently one of the most active. In our recent May ransomware review, only BlackBasta and the prolific LockBit accounted for more known attacks in the last month.
ALPHV ransomware is used by affiliates who conduct individual attacks, beaching organizations using stolen credentials or, more recently by exploiting weaknessesin unpatched Microsoft Exchange servers. During the attacks data is stolen and encrypted, and the victim is asked to pay a ransom for both a decryption tool, and to prevent the stolen data being leaked.
Although affiliates perform the attacks, the ransom negotiations and data leaks are typically coordinated from a single ALPHV website, hosted on the dark web.
But in this case neither of those two things were true.
Instead of hosting the stolen data on a site that deals with all the gang’s victims, the victim had a website dedicated to them. Bolder still, the site wasn’t on the dark web where it’s impossible to locate and difficult to take down, but hard for many people to reach. Instead it was on the regular world wide web, where we (and law enforcement) could easily discover things like where it was located and what company was hosting it. It was even indexed by Google.
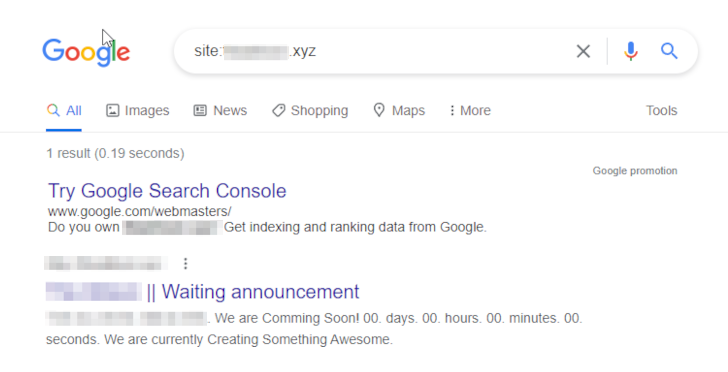
The aim seems to have been to make it as easy as possible for employees and guests to find their data, so that they would put pressure on the hotelier to pay up.
A message on the site makes it clear that this is about ramping up pressure:
Inaction endangers both your employees and your guests ... We strongly advise you to be proactive in your negotiations; you do not have much time.
The 112GB of stolen data included personally identifiable information (PII) belonging to 1,500 employees and guests. The gang is reported to have created “data packs” for each employee, containing files related to their hotel employment.
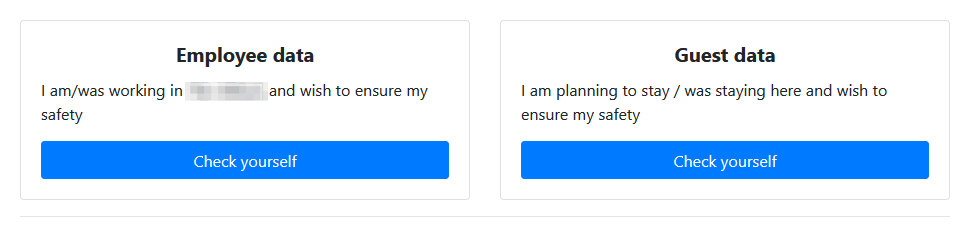
Ransomware groups use the dark web for their leak sites, rather than the regular web, because it makes it almost impossible for them to be taken down, or for their operators to be traced.
So, wouldn’t this make the site easy to take down, and leave the operators vulnerable?
Because this is unlike anything ALPHV has done before, it’s possible that this is being done by an affiliate, and it may turn out to be a mistake. However, it’s likely the accounts for the site’s name and hosting were created using stolen data. Equally, it may be that this was simply an experiment and that ALPHV were using the media to spread word of the site and weren’t expecting it to be around for very long.
Sure enough, the site disappeared from the web yesterday.


