
Advanced tools: Process Hacker
Process Hacker is a very valuable tool for advanced users. It can help them to troubleshoot problems or learn more about specific processes that are running on a certain system. It can help identify malicious processes and tell us more about what they are trying to do.
Background information
Process Hacker is an open source project and the latest version can be downloaded from here. The site also provides a quick overview of what you can do with Process Hacker and what it looks like. At first sight Process Hacker looks a lot like Process Explorer but it does have more options. And since it is open source you can even add some of your own if you are able and willing.
Installing
If you just want to start using the tool it’s as easy as downloading and running the installer:
The current version at the time of writing is 2.39
During the installation process you will see a few options:
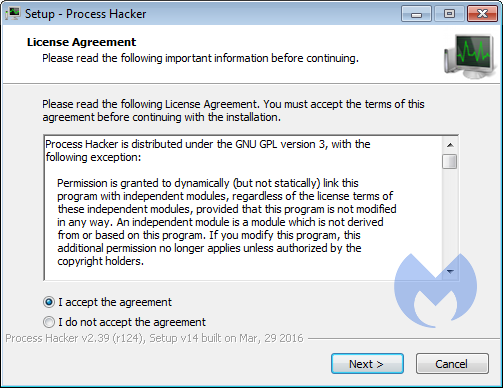
Accept the EULA
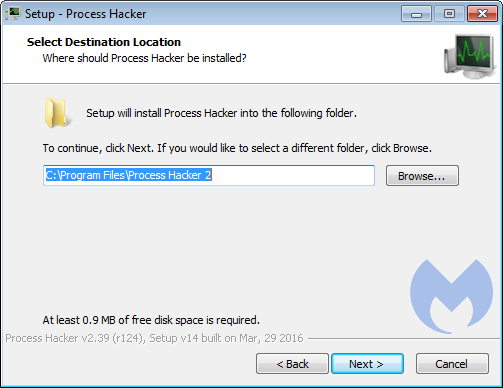
Choose the destination folder for the program
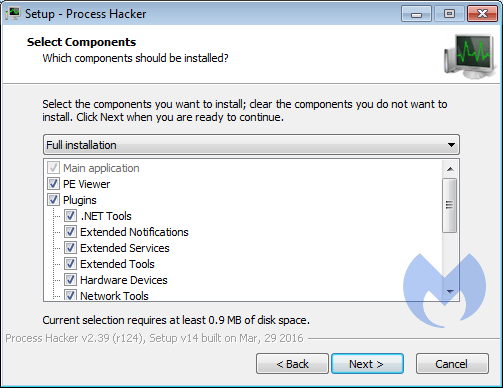
Select the components you wish. They don’t require a lot of space, so there is no need to be picky.
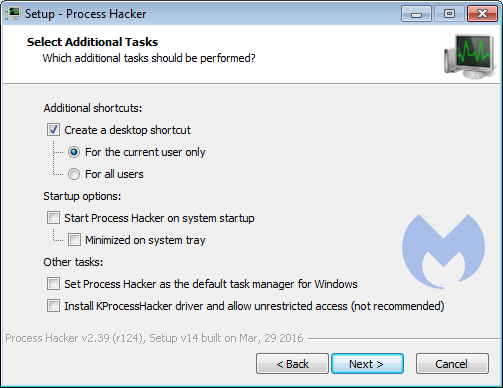
These are worth studying and depend on how you plan to use Process Hacker. Most can be changed afterwards though.
And you are done!
The main screen
When you run Process Hacker this is the main screen.
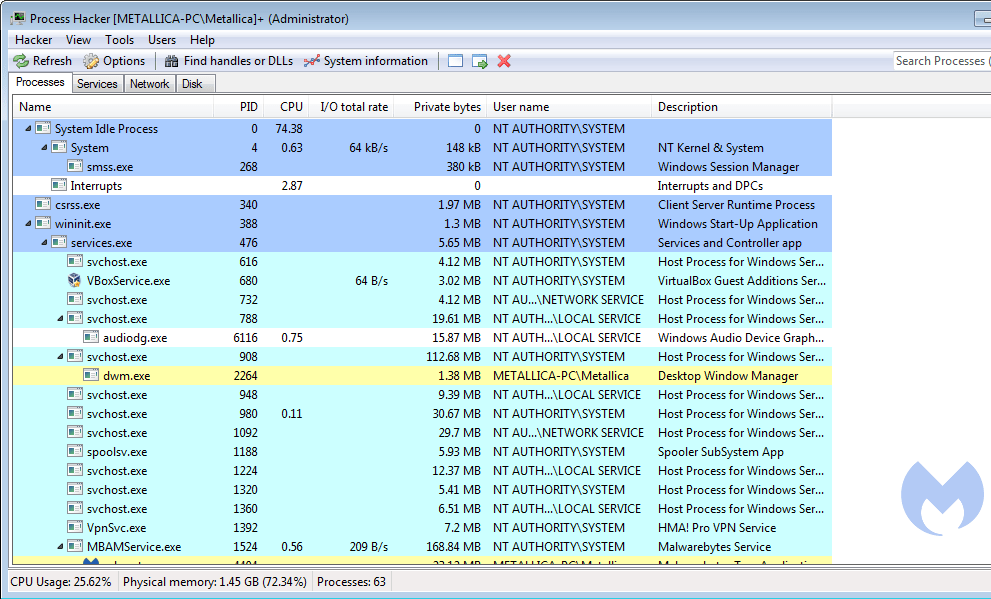
In the default settings it shows you the Processes tab with all the running processes in tree-view and lists:
- their Process Identifier (PID)
- their CPU usage percentage (CPU)
- their I/O total rate
- their private bytes
- the user-name the process is running under
- a short description
By hovering over one of the process name you can find more information about them.
The other tabs are Services, Network, and Disk. Each of the last two shows more information about the processes with regards to their network and disk usage respectively. The services tab shows a full list of present services and drivers.
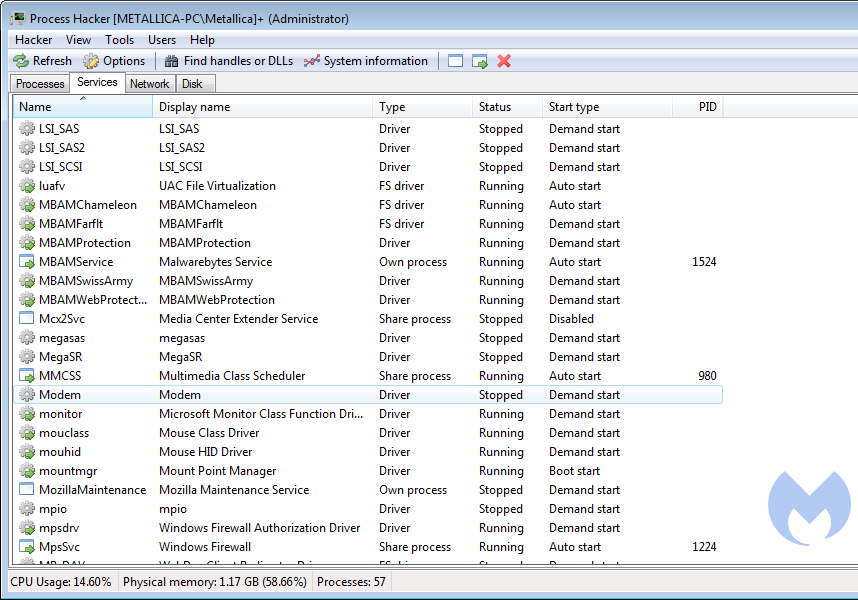
The meaning of the color-coding of the processes can be found, and changed, under Hacker > Options > on the Highlighting tab.
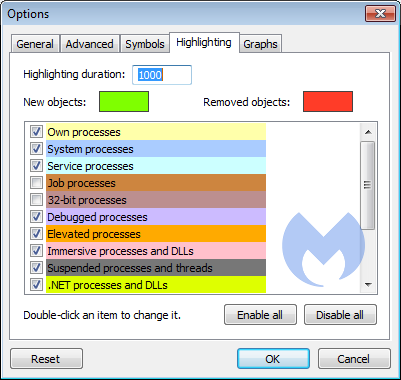
The option to toggle to Replace Task manager with Process Hacker can be found under Hacker > Options > on the Advanced tab.
Releasing handles
One very useful option that Process Hacker has to offer is that it can help you delete those files that just don’t want to go away because they are “in use by another process”.
Process Hacker can help you identify that process and break the tie. Here’s the procedure:
- In the main menu click on Find handles or DLLs
- In the Filter bar type the full name of the file or a part of that name, then click on Find
- In the results look for the exact filename and right-click that line
- From the right-click menu choose Go to owning process
- The process will be highlighted in the Processes window
- Right-click the highlighter process and choose Terminate
- Consider the warning in the prompt that data might be lost and be aware that Process Hacker can close processes where other task managers might fail
- If you choose to terminate the process you can try deleting the locked file again
Escaping browlocks
Process Hacker can also help you to escape some of the sites that use browlock tactics. For example sites that use this login script:
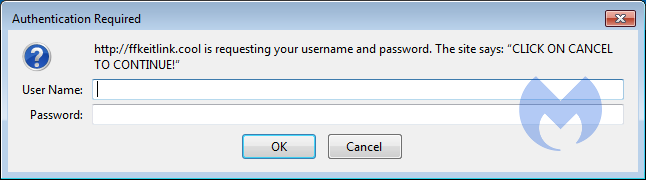
The goal of the threat-actors is is to get the visitor of the site to first allow notifications, and in the end, get him to install one of their extensions. Malwarebytes generally detects these extensions as PUP.Optional.ForcedInstalledExtensionFF.Generic. You can find some more details about these extensions in this removal guide for a nameless extension hailing from browser-test.info.
But anyhow, to close such a tab in Firefox would normally require you to shut down Firefox completely, losing all the other open tabs, or, if you have Restore previous session enabled, get them all back, including the browlock. With Process Hacker you can look at the Network tab:
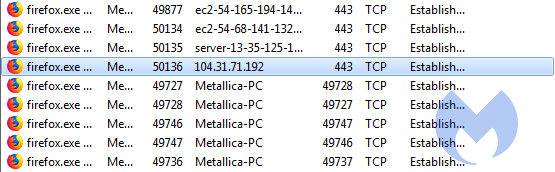
Once you found the guilty party, select the line that shows the contact to the IP or domain of the browlock site. I used tracert to determine the IP for ffkeitlink.cool. Right-click that line and choose Close and this will temporarily break the connection, stopping the script from refreshing the prompt all the time. That give you the chance to close the tab and carry on without having to force-close the Firefox process.
Dumping strings from memory
You can use Process Hacker to create memory dumps of processes. Analysts use these dumps to search for strings and they use scripts or Yara rules to make an initial classification of a process. Is it malware? If so, what kind of malware? Is it after information, which information, and where does it send it?
Right-click on the running process you wish to create a memory dump for and select Create dump file… and then use the explorer window to browse to the location where you want to save the dump. The memory dump created by Process Hacker will have the dmp extension. Depending on what you are looking for the dmp file can be opened in a hex editor, a text editor, or mimikatz (if you are after credentials).
You can create the same memory dumps with Process Explorer, but Process Hacker also includes .NET support which Process Explorer does not.
Finding resource hogs
As with most programs of this kind identifying resource, hogs is easy.
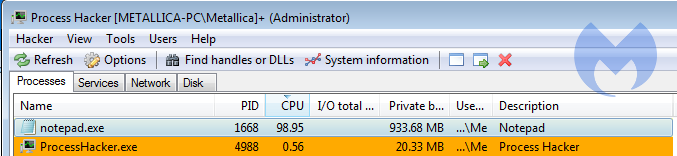
Click the CPU title above the column and the column will be sorted by CPU usage, showing you if a process is slowing you down and which one. The same can be done for Private bytes and I/O total rate.
Versatile and powerful
Process Hacker is a very versatile tool that has a lot in common with Process Explorer. Since it does have a few more options and is more powerful than Process Explorer, advanced users may prefer Process Hacker. Less advanced users who are afraid of the possible consequences of the extra power might want to stick with Process Explorer. If you require help with Process Hacker they have a fairly active forum where you might find a helping hand.
Notes:
- Some AV’s flag Process Hacker as Riskware or Potentially Unwanted because it is able to terminate many processes including some that belong to security software. Malwarebytes detects Process Hacker as RiskWare.ProcessHacker to make users aware of its presence. If you are using the tool, you can exclude it following the instructions in the detection profile.
- The mbamservice process can not be permanently stopped by Process Hacker if you have the self-protection module enabled. You can find this setting under Settings > Protection tab > Startup options.



