Worm.Conficker
ThreatDown is now the name of the Malwarebytes line of business products. References to Malwarebytes below reflect the amazing technology used to first identify the threat.
Short bio
Worm.Conficker is Malwarebytes’ detection name for a family of worms that exploit a vulnerability in older Windows versions.
Type of infection
Worm.Conficker tries to exploit a vulnerability in the Windows server service. This vulnerability can lead to remote code execution if an affected system received a specially crafted remote procedure call (RPC) request. This could allow an attacker to exploit this vulnerability without authentication to run arbitrary code on unpatched versions of systems running Windows 2000 Service Pack (SP) 4, Windows XP SP2 and SP3, Windows Server 2003 SP1 and SP2, Vista Gold SP1, Windows Server 2008 and Windows 7 systems.
Malicious behavior
Network monitoring may reveal crafted RPC requests that are trying to trigger a buffer overflow.
Business remediation
How to remove Worm.Conficker with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.
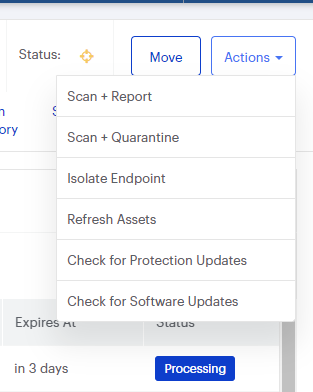
Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections page to see which threats were found.
On the Quarantine page you can see which threats were quarantined and restore them if necessary.
Home remediation
Malwarebytes can detect and remove Worm.Conficker without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.
Associated threats
- Worm.Conficker.H
- Worm.Conficker.Generic

