Trojan.Remcos
ThreatDown is now the name of the Malwarebytes line of business products. References to Malwarebytes below reflect the amazing technology used to first identify the threat.
Short bio
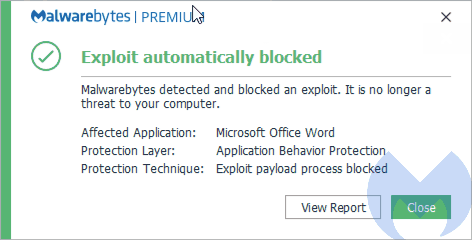
Trojan.Remcos is Malwarebytes’ detection name for a Remote Administration Tool (RAT) targeting Windows systems.
Type of infection
Trojan.Remcos typically infects a system by embedding a specially-crafted settings file into an Office document, this allows an attacker can trick a user to run malicious code without any further warning or notification. The code is XML code which allows for any binary with parameters to be executed. This code is used to download and execute the REMCOS RAT.
Aftermath
Trojan.Remcos gives the threat actor full control over the infected system and allows them to run keyloggers and surveillance (audio + screenshots) mode. This means:
- Data/information about the system may have been stolen
- User credentials may have been stolen
- Digital coins may have been stolen
- Affected system may be susceptible to further attacks and/or infection due to a backdoor that was opened
Business remediation
How to remove Trojan.Remcos with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.
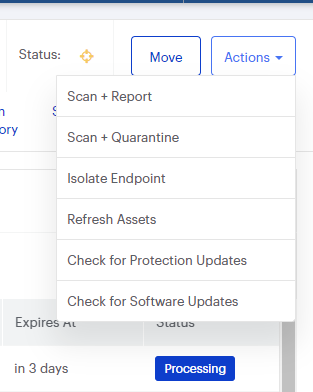
Choose the Scan + Quarantine option. Afterwards you can check the Detections page to see which threats were found.
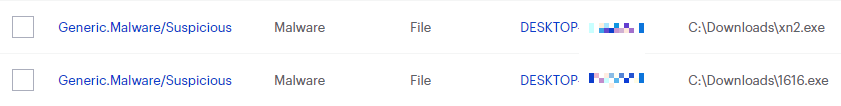
On the Quarantine page you can see which threats were quarantined and restore them if necessary.
Home remediation
Malwarebytes can detect and remove Trojan.Remcos without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get startedbutton.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.