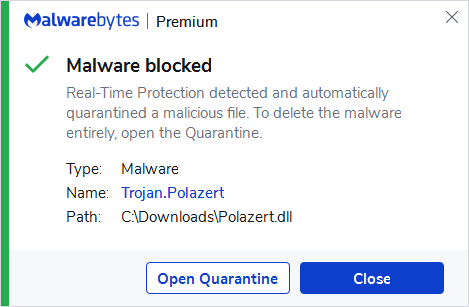
Trojan.Polazert
ThreatDown is now the name of the Malwarebytes line of business products. References to Malwarebytes below reflect the amazing technology used to first identify the threat.
Short bio
Trojan.Polazert is Malwarebytes’ detection name for a .NET Remote Access Trojan (RAT) that acts as a backdoor.
Type of infection
There are several campaigns that distribute Trojan.Polazert. In general they use SEO and social engineering to get victims to download the RAT disguised as a document. Trojan.Polazert is specifically designed to steal credentials from browsers and provide the attacker with a backdoor to further compromise infected systems. To achieve this collected data are sent to a C&C server.
Malicious behavior
Trojan.Polazert adds shortcuts to the Startup folder and changes existing shortcuts on the victim’s computer to gain persistence.
Aftermath
The backdoor component of Trojan.Polazert can be used to install further malware on the infected system. As of yet there is no fixed follow-up payload.
Business remediation
How to remove Trojan.Polazert with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.
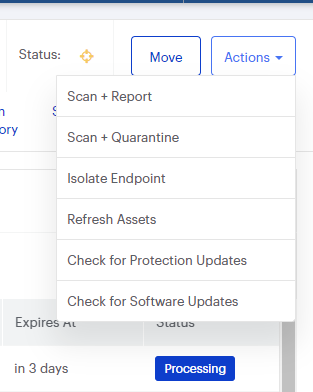
Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections page to see which threats were found.
On the Quarantine page you can see which threats were quarantined and restore them if necessary.
Home remediation
Malwarebytes can detect and remove Trojan.MalPack.GS without further user interaction.