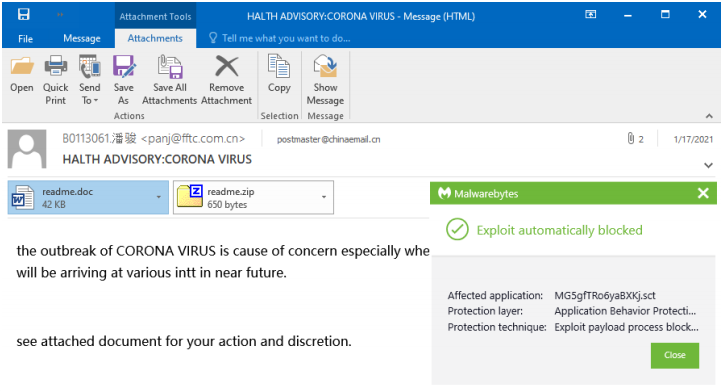
Trojan.LemonDuck
ThreatDown is now the name of the Malwarebytes line of business products. References to Malwarebytes below reflect the amazing technology used to first identify the threat.
Short bio
Trojan.LemonDuck is Malwarebytes’ detection name for the components of a specific botnet that is aimed at mining the Monero cryptocurrency using affected systems.
Type of infection
Trojan.LemonDuck is an advanced cryptominer that is actively being updated with new exploits and obfuscation tricks. Among others it aims to evade detection with its fileless miner. Trojan.LemonDuck uses several methods for the initial infection and to propagate across networks:
- Malspam: the email typically contains two files: a Word document exploiting CVE-2017-8570 and a zip archive with a malicious JavaScript.
- Server Message Block (SMB) vulnerabilities: Trojan.LemonDuck leverages EternalBlue and the SMBGhost flaw to compromise a host as well as propagate to other machines within a network.
- RDP brute-forcing: Trojan.LemonDuck’s RDP module scans for servers listening on port 3389 and tries to login as user ‘administrator’ from a list of passwords.
- SSH brute-forcing: the Linux equivalent of RDP attacks. Trojan.LemonDuck scans for machines that are listening on port 22 and performs a brute-force attack using a list of passwords combined with the ‘root’ user name.
- LNK vulnerability: leverages the vulnerability CVE-2017-8464 via USB removable drive that contain a malicious .LNK file.
- ProxyLogon: an exploit for Exchange servers that allows an unauthenticated attacker to execute arbitrary commands onto vulnerable servers.
Aftermath
Due to the high computing resources required for mining, systems and servers could become slower or even run into failure.
Trojan.LemonDuck also changes the DNS settings in some cases. This can lead to connectivity loss during infection as well as after removing the infection. Therefor it is advisable to check these settings when Trojan.LemonDuck has been detected on a system.
Business remediation
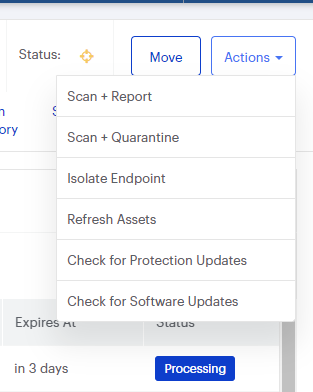
Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections page to see which threats were found.
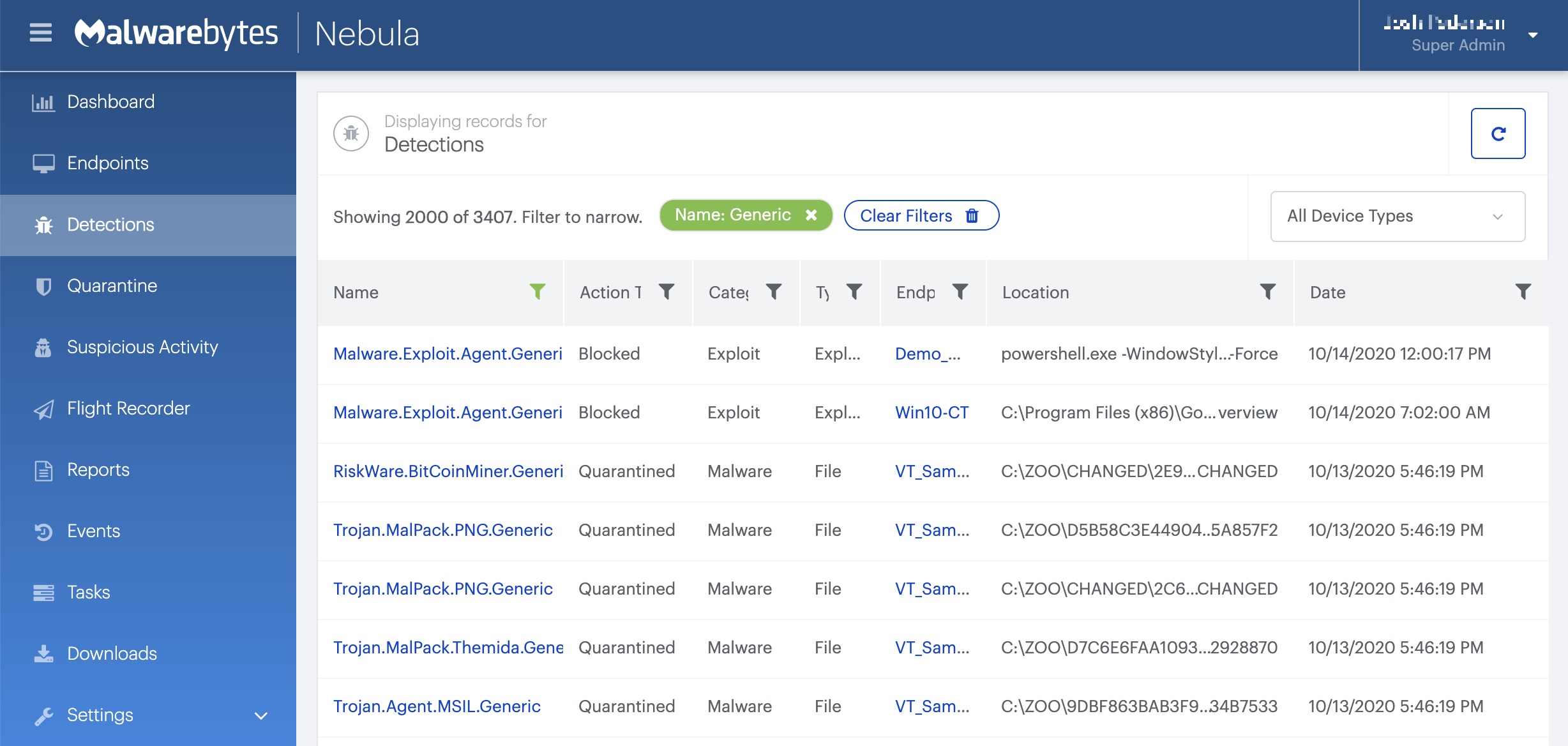
On the Quarantine page you can see which threats were quarantined and restore them if necessary.
Home remediation
Malwarebytes can detect and remove Trojan.GuLoader without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.
Associated threats
- Trojan.LemonDuck.ScriptKill