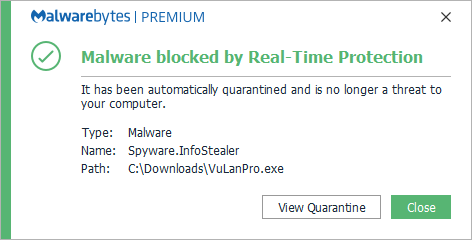
Spyware.InfoStealer
ThreatDown is now the name of the Malwarebytes line of business products. References to Malwarebytes below reflect the amazing technology used to first identify the threat.
Short bio
Spyware.InfoStealer is Malwarebytes’ generic detection for applications that can harvest keystrokes, screenshots, network activity, and other information from systems where it is installed. It may also covertly monitor user behaviour and harvest personally identifiable information (PII) including names and passwords, keystrokes from emails, chat programs, websites visited, and financial activity.This spyware may be capable of covertly collecting screenshots, video recordings, or the ability to activate any connected camera or microphone. Collected information may be stored locally and later retrieved, or may be transmitted to an online service or location.
Type of infection
Spyware.InfoStealer may be distributed using various methods. This software may be packaged with free online software, or could be disguised as a harmless program and distributed by email. Alternatively, this software may be installed by an individual with physical or remote access to the computer. Spyware.InfoStealer may be installed with or without user consent.
Malicious behavior
Spyware.InfoStealer may run as a start-up entry and may be visible as running processes on compromised machines. Alternatively, Spyware.InfoStealer may also be configured in a manner which prevents visible processes and start-up entries
Business remediation
How to remove Spyware.InfoStealer with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.
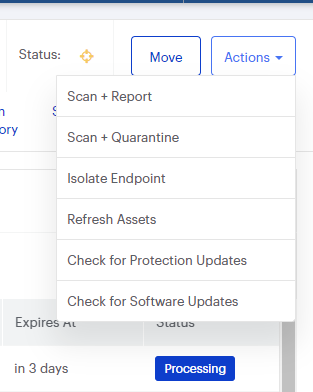
Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections page to see which threats were found.
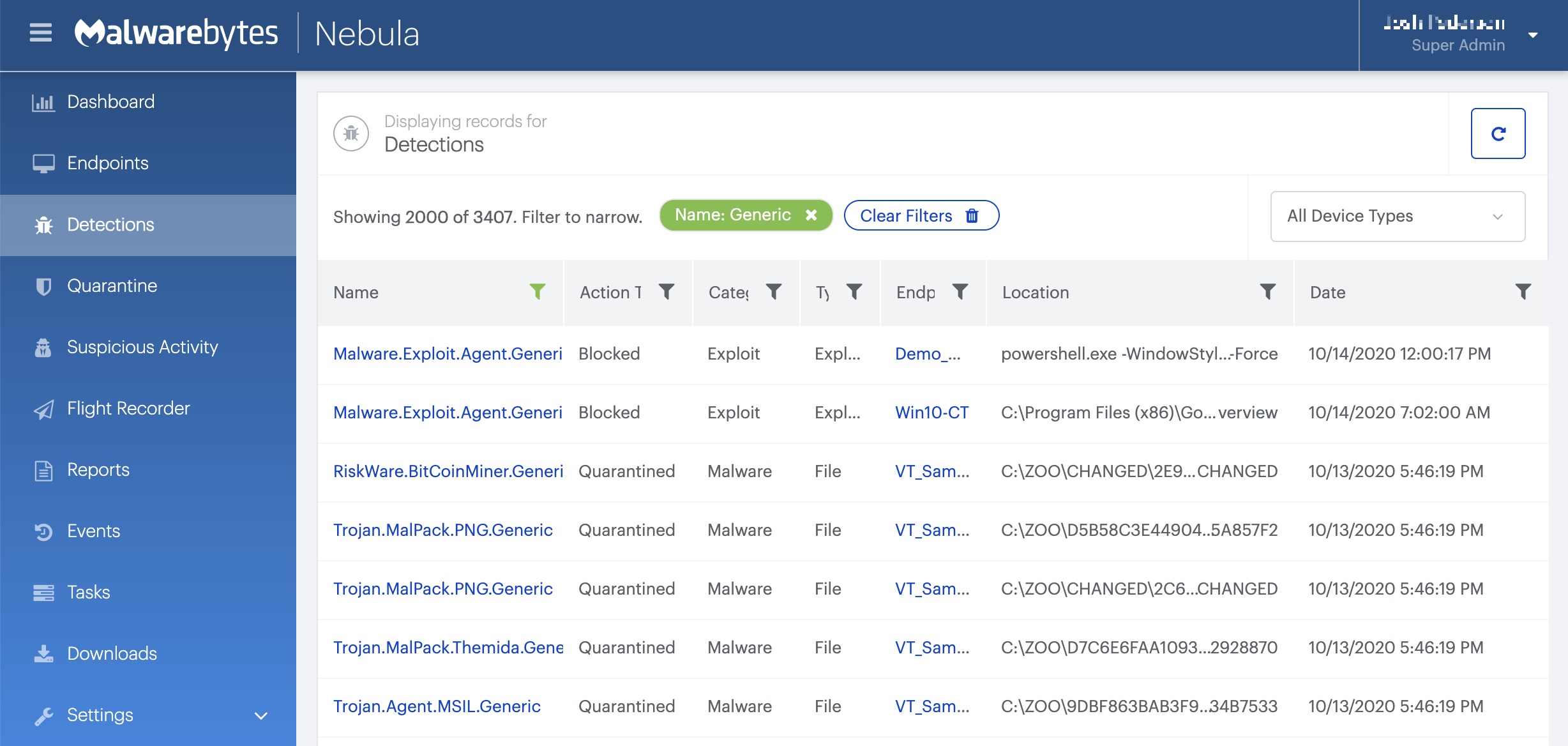
On the Quarantine page you can see which threats were quarantined and restore them if necessary.
Home remediation
Malwarebytes can detect and remove many Spyware.InfoStealer infections without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.