
Why are browser vulnerabilities going unpatched?
Last week, the top five unpatched vulnerabilities were all browser-based, some from 2023.
When we looked at the ThreatDown stats from our Vulnerability and Patch Management solution for last week, we noticed a worrying trend.
We looked specifically at vulnerabilities that made it to the Known Exploitable Vulnerabilities catalog maintained by the Cybersecurity and Infrastructure Security Agency (CISA).
On September 18, 2023, CISA announced that this catalog reached the milestone of covering more than 1,000 vulnerabilities since its launch in November 2021. While this may seem like a lot, with over 25,000 new vulnerabilities released in 2022 alone, it helps organizations to focus on the vulnerabilities that matter the most.
So, when we noticed that there were five CVEs on the CISA list that really stood out in our data, we decided to do some investigating. The information is anonymized, so we can’t ask the customers what’s going on.
Instead, we focused on the vulnerabilities themselves, and we soon found a trend. Let’s look at the top five, and you’ll probably see soon enough what we spotted.
- CVE-2024-4947 is a type confusion vulnerability in V8, Chrome’s JavaScript and WebAssembly engine, which allows a remote attacker to execute arbitrary code inside a sandbox via a crafted HTML page. Patch issued May 15, 2024.
- CVE-2024-4761 is an out of bounds write in V8 in Google Chrome, which allows a remote attacker to perform an out-of-bounds memory write via a crafted HTML page. Patch issued May 13, 2024.
- CVE-2023-42917 is a memory corruption vulnerability in Safari was addressed with improved locking where processing web content may lead to arbitrary code execution. Patch issued November 30, 2023.
- CVE-2023-41993 is a WebKit vulnerability where processing web content may lead to arbitrary code execution. This vulnerability affects various systems, including Safari. Patch issued September 26, 2023.
- CVE-2024-4671 is a use after free vulnerability in the Visuals component of Chrome that can be exploited by remote attackers to trigger an exploitable heap corruption via a specially crafted HTML page.
At first glance, I’m immediately seeing browser vulnerabilities in Chromium browsers and Safari. Together they would account for a market share of roughly 90% at this moment (I’ve counted Edge and Opera as well because they are Chromium based).
In fact, this trend continues if we look at the number of affected machines, the numbers six (CVE-2023-5217 Chrome) and seven (CVE-2024-0519 Chrome) complete the list of high severity vulnerabilities that ThreatDown flagged to its customer, but they were about half as prevalent as those of the top five.
All of these problems could be fixed by patching, so what’s going on? The data itself is coming from a solution that can patch the vulnerabilities, so it’s not a technology problem, it must be something else.
The first thing to understand is that every organization has its own array of operating systems, databases, network devices, and applications, and they all need to be supported. Patching is just one of many IT and security responsibilities, and it can be easy to put it off. Vulnerability and Patch Management software can certainly make it easier, but every organization needs a process for patching.
Even in an environment with a patching process in place, the impact on security is only one consideration for organizations to weigh up. Everyone has a browser, and browsers are heavily used. Forcing a browser update, which usually triggers a restart, might inconvenience a lot of (vocal) users.
And in some organizations, the choice of browser is left to users, and those users may be responsible for keeping them updated. (If you look at the type of vulnerabilities we listed, that might not be the best of ideas—all of them can be exploited by viewing malicious content, and all of them can lead to remote code execution.)
If employees can’t be convinced to keep their browsers updated, what are your other options? Solutions that companies can use to manage popular browsers at the corporate level are available. But if you want to do this right, the first step is to restrict all browsers except those specifically allowed and managed by the organization. ThreatDown users could use Application Block to stop employees from using other browsers, for example.
Once you have limited the number of browsers you need to worry about, it is time to make sure that every user has automatic updates enabled, if possible. That should bring those numbers of unpatched systems down quickly.
The rest will have to endure scheduled software updates. In ThreatDown’s Nebula, you can create a schedule to install third-party software updates regularly.
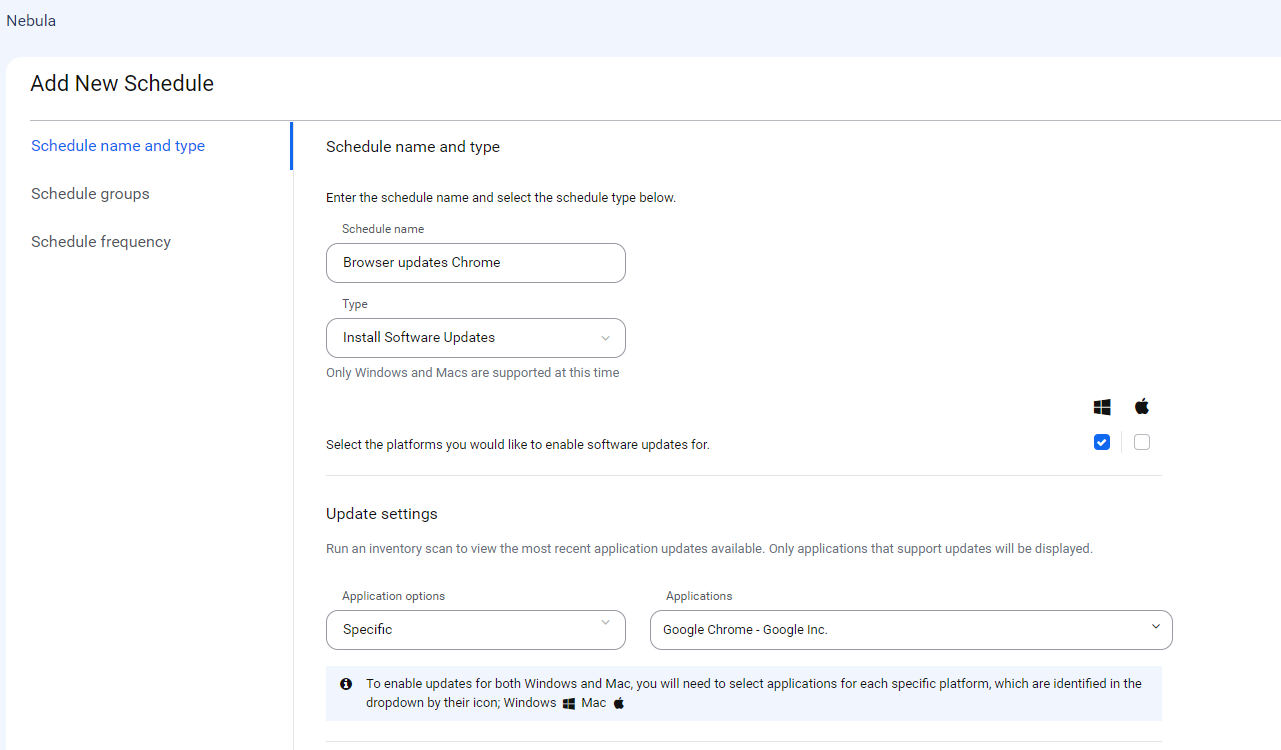
Happy patching!
We don’t just report on vulnerabilities—we identify them, and prioritize action.
Cybersecurity risks should never spread beyond a headline. Keep vulnerabilities in check by using ThreatDown’s Vulnerability Assessment and Patch Management solutions.


