
Ransomware review: June 2024, a year-high 470 attacks recorded
In May, we recorded a total of 470 known ransomware attacks, including some sickening attacks on healthcare.
This article is based on research by Marcelo Rivero, Malwarebytes’ ransomware specialist, who monitors information published by ransomware gangs on their Dark Web sites. In this report, “known attacks” are those where the victim did not pay a ransom. This provides the best overall picture of ransomware activity, but the true number of attacks is far higher.
In May, we recorded a total of 470 ransomware attacks, the most all year so far. The biggest stories of the month included authorities revealing the identity of LockBit leader LockBitSupp, devastating attacks on the healthcare sector, and reports of the BlackBasta group using an increasingly popular social engineering scam.
First off, the elephant in the room: On May 6th, the NCA, Europol, and the FBI revealed the identity of LockBitSupp, a 31-year-old Russian named Dmitry Yuryevich Khoroshev. LockBitSupp was a prominent leader and spokesperson of the LockBit group who performed various key roles for the gang, including upgrading its infrastructure, recruiting new developers, and managing the affiliate gangs that used the LockBit ransomware in attacks.
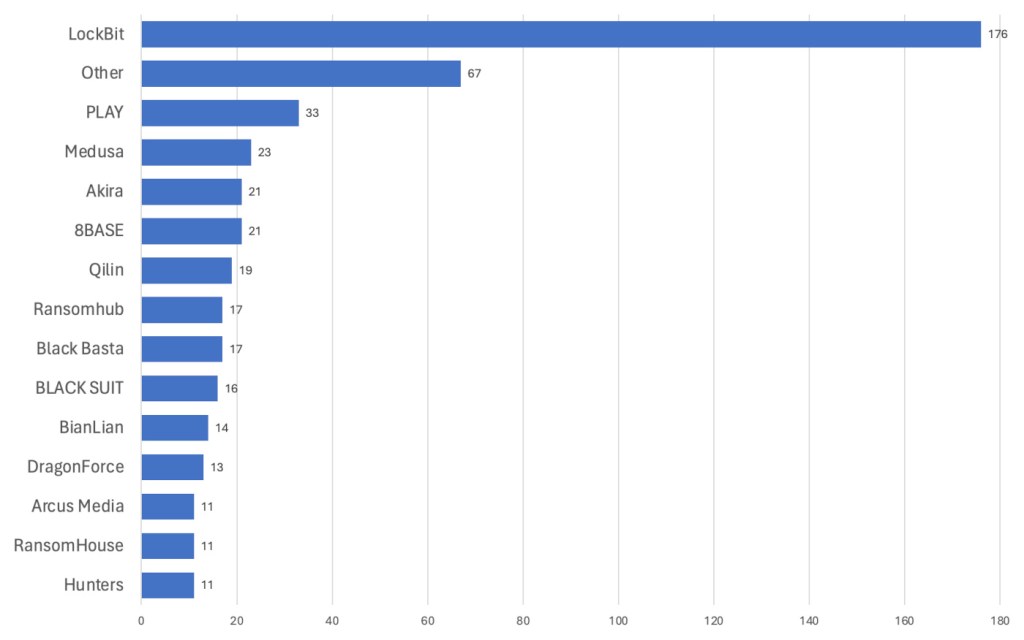
Since the reveal, LockBit has leaked the names of 176 victims on its site—the most in its almost 5-year history. While one might think of this burst of activity as a revenge spree, there might be reason to be skeptical of their recent numbers. In April, the gang was caught posting illegitimate victims on its leak site, likely in an attempt to feign normalcy amidst the disruption of the takedown. For May, however, our data shows very few duplicate attacks, suggesting that at the very least, LockBit probably isn’t reusing old data to puff up its numbers.
Despite the unmasking of Khoroshev, it’s undeniable that LockBit remains active. Was Operation Cronos as successful as we originally thought? LockBit, unsurprisingly, seems to think it’s all theater. “I don’t understand why they’re putting on this little show,” a LockBit representative told VX Underground in response to Khoroshev’s identity being revealed. “They’re clearly upset that we continue to work.” The spokesperson also accused US agents of lying.

Healthcare in the crosshairs
In May, two devastating ransomware attacks hit the healthcare sector.
Ascension, one of the nation’s largest health systems, suffered a ransomware attack at the hands of Black Basta, causing significant disruption as doctors and nurses resorted to paper records.
Australian e-prescription service MediSecure also suffered a large-scale ransomware attack, which forced the company into voluntary administration. Both attacks come on the heels of the massive ransomware attack on Change Healthcare in April—already described as the most significant cyberattack on the US healthcare system in history.
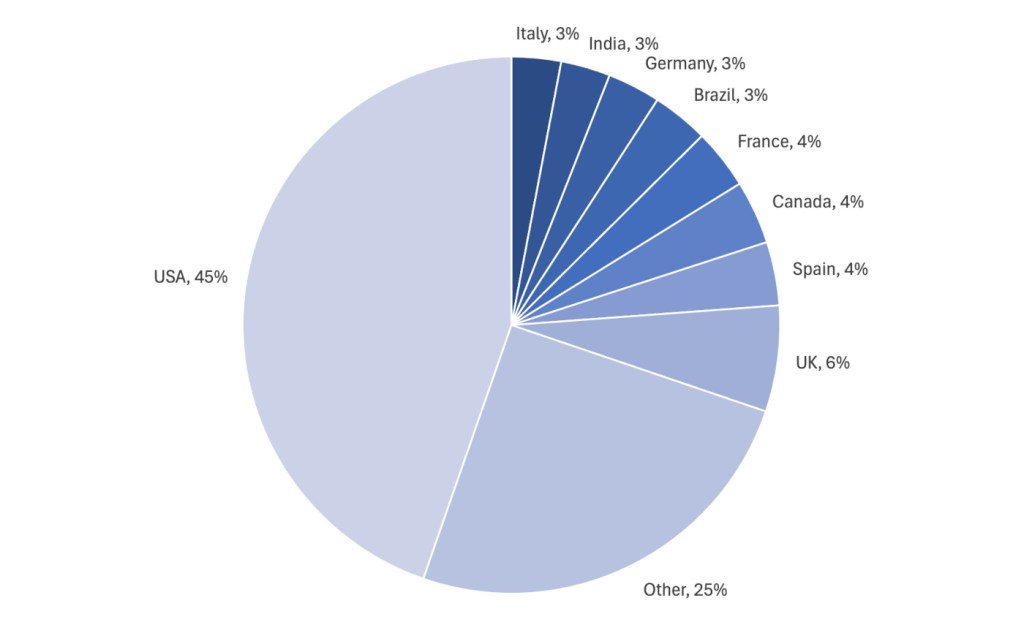
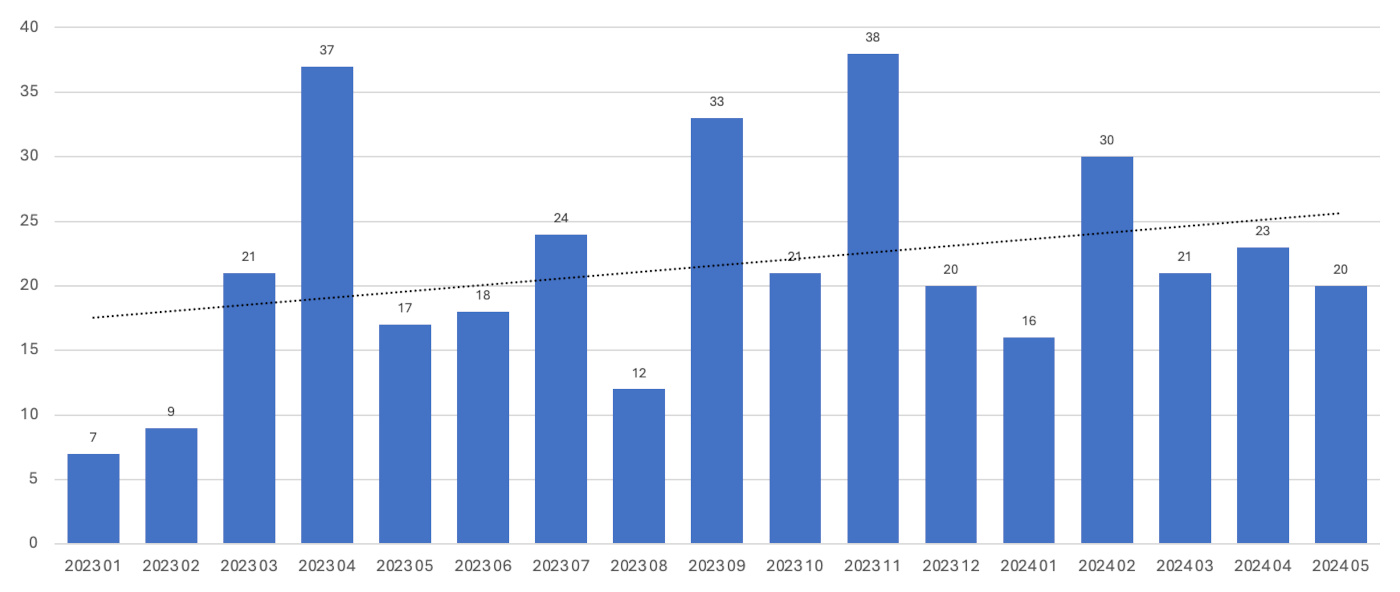
Healthcare’s ransomware crisis is borne out by our data: Despite month-to-month variability, we’ve observed an overall increasing trend in ransomware attacks on the healthcare sector since Jan 2023, the vast majority of which fall in the USA.
Support scams
Earlier this month, I returned from the Gartner Security and Risk Management Summit. One topic that came up repeatedly was the rise of attackers using IT support scams to gain initial access to a victim’s computer. If you’ll recall, this is exactly how MGM and Caesars Entertainment were breached in September 2023: Threat actors used LinkedIn to pinpoint employees, subsequently impersonating them and contacting the company’s help desk requesting account access.
Last month, Black Basta was the latest ransomware gang observed using similar tactics.
Specifically, Microsoft observed a Black Basta affiliate tricking victims by posing as Microsoft technical support or an IT professional from the user’s company. In these attacks, the affiliate convinces the victim that they need technical assistance and persuades them to grant access to their device through Quick Assist, a legitimate IT application that allows users to share their Windows or macOS device with another person remotely for technical support.
Once access is granted, the attackers establish backdoor access to the machine. After the call, they use this backdoor to install Black Basta ransomware.
Let this be a warning on the increasing use of help desk-based social engineering scams for initial access: Stay vigilant by monitoring the use of remote management tools such as Quick Assist, educating employees on recognizing phishing attempts, and implementing strict access controls.
New players
FSOCIETY
FSOCIETY is a new ransomware group that published the data of four victims on its leak site last month.
Underground
Underground is a new ransomware group that published the data of two victims on its leak site last month.
EMBARGO
EMBARGO is a new ransomware group that published the data of three victims on its leak site last month.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Detecting ransomware attacks with ThreatDown Managed Detection and Response (MDR)
ThreatDown MDR analysts are experienced in detecting threats early and blocking ransomware attackers before it’s too late. Read more on how the ThreatDown MDR team successfully stopped a Medusa ransomware attack here.



