
Patch now! Critical RCE vulnerability in Microsoft Message Queuing
Patch Tuesday revealed a serious bug that could be remotely exploitable on up to a million internet-connected Windows machines.
Included in the June 2024 Patch Tuesday updates was a fix for a critical vulnerability in Microsoft Message Queuing (MSMQ) that could lead to Remote Code Execution (RCE). That sounds serious enough to dive into the issue, so let’s.
MSMQ allows communication between Windows computers that aren’t always connected to the same network. Applications send messages to queues and read messages from queues. As such it also enables applications running at different times to communicate. Messages that can’t get to their destination are added to a queue resent when the destination computer can be reached.
The Common Vulnerabilities and Exposures (CVE) database lists publicly disclosed computer security flaws. The CVE for the vulnerability in MSMQ is:
CVE-2024-30080 (CVSS score 9.8 out of 10): A Microsoft Message Queuing (MSMQ) Remote Code Execution (RCE) use-after-free vulnerability.
Use-after-free vulnerabilities are the result of the incorrect use of dynamic memory during a program’s operation. If, after freeing a memory location, a program does not clear the pointer to that memory, an attacker can exploit the error to manipulate the program. Referencing memory after it has been freed can cause a program to crash, use unexpected values, or execute code.
In this case, an attacker would need to send a specially crafted malicious MSMQ packet to an MSMQ server. This could result in remote code execution on the server side. In this case, a successful attacker could send a specially crafted message to the MSMQ service and execute arbitrary code on the target system with SYSTEM privileges.
While the number of targets is limited to Windows and Windows Server installations with the Windows message queuing service enabled, exploitation is considered easy, hence the high CVSS score. And as you can see in the Shodan scan below, there are about a million servers listening on the ports associated with MSMQ, with roughly half of them in the US.
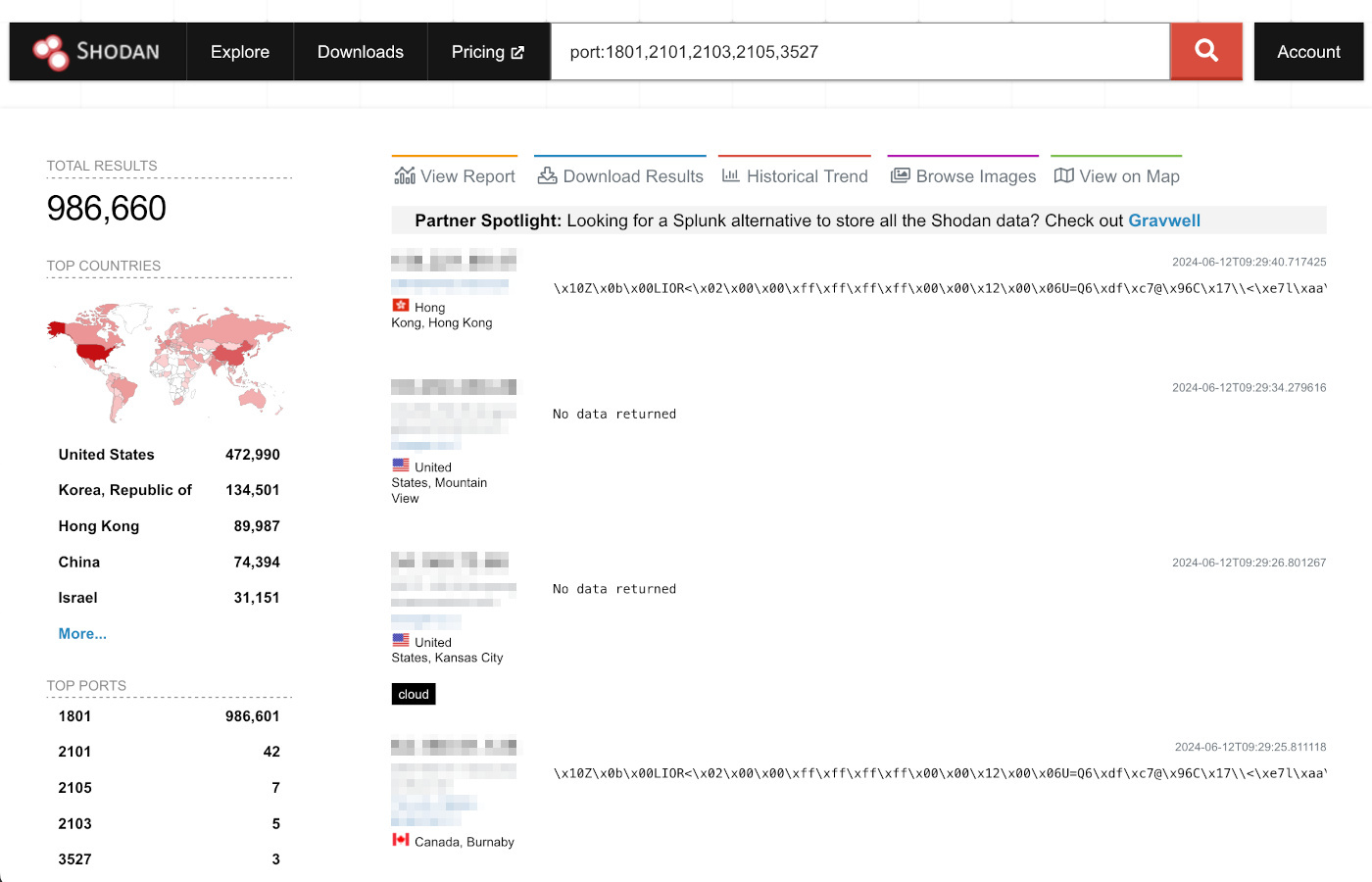
It is crucial for all businesses that are using MSMQ to prioritize this patch, since cybercriminals are likely to figure out quickly how to create messages that allow them to exploit this vulnerability.
The MSMQ service, which is a Windows component, needs to be enabled for a system to be exploitable by this vulnerability. This feature can be added or removed via the Control Panel.
So, if this vulnerability does not show up in your Vulnerability and Patch Management solution, or if you are unable to quickly apply the patch for another reason, you can also remove the MSMQ service if you are not using it.
Please Note: The process to remove the MSMQ Service is a destructive operation which can result in data loss, because all existing queues and queue configuration information are deleted, and all messages contained in those queues and the system dead letter queue (DLQ) are deleted.
On Windows servers:
- Open Server Manager
- From the manage menu, click the Remove Roles and Features
- This will open the “Remove Roles and Features” Wizard
- Click Next until the Features option is shown
- Scroll down, deselect the Message Queuing option, and click Next
- Click the Remove button to complete the removal.
A reboot may be required to finalize the changes.
On Windows 10/11:
- Open the Control Panel app
- Open the Programs option
- Under Programs and Features click on Turn Windows features on or off
- Scroll down and deselect the Microsoft Message Queue (MSMQ) Server option and then click OK
- Reboot to finalize the changes
We don’t just report on vulnerabilities—we identify them, and prioritize action.
Cybersecurity risks should never spread beyond a headline. Keep vulnerabilities in check by using ThreatDown’s Vulnerability Assessment and Patch Management solutions.
Cybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of MalwareCybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of Malware

