
How to protect against Living Off the Land attacks
Read on to learn more about LOTL attacks, including the most commonly-abused tools, how to detect stealthy LOTL tactics, and what your organization can do to protect against them.
As we kick off 2024, I can’t help but ruminate on the biggest cybersecurity challenges businesses faced last year and the ways our industry addressed or didn’t address them. From workforce shortages to ransomware gangs to vulnerability exploits, IT teams were stretched thin, often so consumed with putting out fires, they had little time to train on the complex security software purchased by their organizations. This challenge remains acute in 2024, and it’s given birth to a new kind of cyberattack.
Ever the opportunists, threat actors have pounced on legitimate IT software, tools, and processes, leveraging them against businesses to perform malicious actions disguised as normal behavior, confounding IT teams and security solutions alike. This method of compromise has become so successful at evading detection, it’s now one of the most common techniques used by ransomware gangs to steal data from organizations.
They’re called Living Off The Land (LOTL) attacks, and without swift action from the security community and businesses alike, they’ll only proliferate and evolve. Read on to learn more about LOTL attacks, including the most commonly-abused tools, how to detect stealthy LOTL tactics, and what your organization can do to protect against them.
Cheers,
Marcin Kleczynski
CEO, Malwarebytes
Cybercriminals exploit legitimate IT tools in Living Off The Land attacks
You’ve probably heard the expression, “If it ain’t broke, don’t fix it.” For ransomware gangs, it’s more like, “If it ain’t broke, break it—but don’t tell anyone.”
Over the last year, organizations of all sizes have felt the heightened threat of cyberattacks, a menace underscored by the continued proliferation of Ransomware-as-a-Service (RaaS) gangs. From July 2022 to June 2023, there were 1,900 total ransomware attacks in just four countries—the US, Germany, France, and the UK. The most popular ransomware techniques in recent years have involved supply chain attacks, double and triple extortion threats, and vulnerability exploits. But today, the most pervasive tactic ransomware gangs use to evade detection and steal data is called Living Off The Land (LOTL).
LOTL attacks are when cybercriminals leverage legitimate IT tools, such as PowerShell, PS Exec, or Windows Management Instrumentation (WMI) to perform malicious actions. A type of advanced persistent threat (APT), LOTL attacks use built-in capabilities, binaries, scripts, administrative functions, drivers, and batch files already present in the system to execute commands, modify system configurations, steal sensitive information, and ultimately, control the business network.
Unlike standard malware attacks that rely on malicious files deployed to endpoints and networks, LOTL attacks are fileless, meaning threat actors are not required to install code within the target system to achieve access. According to the 2023 CrowdStrike Global Threat Report, 71 percent of all cyberattacks last year were fileless (aka LOTL), compared to 62 percent the year before. By mimicking normal user behavior, LOTL attacks make it extraordinarily challenging for IT teams and security solutions to detect signs of malicious activity.
Some of the top RaaS gangs in action today, including Lockbit, Vice Society, and ALPHV, employ LOTL techniques after deep study of an organization’s environment and the processes typically used by employees. Adversaries manage to slip past IT teams and cybersecurity tools by blending suspicious activity within the parameters of normal usage, often remaining undetected on the network for months, if not years.
“LOTL attacks represent a sophisticated evolution in strategies employed by RaaS gangs,” said Marcelo Rivero, Senior Malware Research Engineer at Malwarebytes. “By leveraging legitimate tools and processes, these threat actors can effectively ‘hide in plain sight,’ challenging their detection and mitigation.”
For example, PowerShell has script commands that an attacker could use to steal data from a company network, but which also resemble legitimate system administrative tasks used by IT professionals. By conducting an LOTL attack using PowerShell during normal business hours, cybercriminals can avoid the usual scrutiny that would come from moving malware across a network late at night.
Top LOTL tools used by ransomware gangs
LOTL attacks exploit trusted system tools and applications to evade detection on company networks. Initial access is often gained through exploit kits, stolen credentials, hijacked native software, binary planting, registry run keys, and fileless malware. Attackers then use preexisting vulnerabilities in IT software to execute malicious code, move laterally within the system, and maintain persistence. While RaaS gangs use a wide variety of IT tools in LOTL attacks, below are the five most common documented by our team over the last year.
| Tool | Legitimate use | Malicious use | Abused by |
| PowerShell | Versatile scripting language and shell framework for Windows systems | Execute malicious scripts, maintain persistence, and evade detection | LockBit, Vice Society, Royal, BianLian, ALPHV, Black Basta |
| PS Exec | Lightweight command-line tool for executing processes on remote systems | Execute commands or payloads via temporary Windows service | LockBit, Royal, ALPHV, Play, BlackByte |
| WMI | Admin feature for accessing and managing Windows system components | Execute malicious commands and payloads remotely | LockBit, Vice Society, Black Basta, Dark Power, Cl0p, BianLian |
| Mimikatz | Open source tool for Windows security and credential management | Extract credentials from memory and perform privilege escalation | LockBit, Black Basta, Cuba, ALPHV |
| Cobalt Strike | Commercial penetration test to assess network security and simulate advanced threat actor tactics | Command and control, lateral movement, and exfiltration of sensitive data | LockBit, Black Basta, Royal, ALPHV, Play, Cuba, Vice Society |
Read also: Living Off The Land (LOTL) attacks: Detecting ransomware gangs hiding in plain sight
Impact of LOTL attacks
The impacts of successful LOTL attacks on businesses large and small are significant, ranging from data theft and extortion to complete system compromise. Where LOTL criminals remain undetected on business networks for long stretches of time, ample opportunities arise for sabotage, espionage, fraud, social engineering, privilege escalation, credential theft, and more. LOTL attacks, which typically evolve into ransomware attacks, often result in the loss of sensitive information, business disruption, financial loss, and damage to an organization’s reputation. The economic consequences can be especially severe for small and medium-sized businesses that may not have the resources to recover.
In 2017, the Petya and NotPetya attacks leveraged LOTL techniques to wreak havoc on organizations around the world, causing an estimated $10 billion dollars in losses and underscoring the need for more robust cybersecurity practices to combat such tactics. However, with LOTL attacks showing no signs of stopping in 2024, it’s clear that IT and security teams need additional help to spot the malicious within the mundane.
Read also: Ransomware gangs and Living Off The Land (LOTL) attacks: a deep dive
Detecting LOTL attacks
When it comes to fighting LOTL, organizations must combine human expertise with advanced detection technologies in order to properly identify and respond.
“For effective detection of LOTL attacks, understanding the environment is paramount,” said Hiep Hinh, Principal MDR Analyst at Malwarebytes. “This requires knowledge of typical network activities, such as standard user behaviors, their usual online hours, and common data usage patterns.” Hinh said security analysts armed with this baseline can more easily identify anomalies or outliers, such as employees being active at unusual times or using tools like command interfaces or PowerShell, which are not inherently malicious but may be uncommon for the user or environment.
IT and security teams must have a thorough understanding of normal network traffic and staff behavior to be able to spot and investigate LOTL abnormalities. Detection requires deep network visibility with continuous monitoring for anomalous commands, payloads, or other suspicious activities. Analysts should scrutinize trusted network paths for abuse, especially commands to and from key assets to ensure they are authorized, expected, and unmanipulated.
Product spotlight: Fight LOTL attacks with ThreatDown Bundles
Many IT-constrained businesses are facing difficult cybersecurity challenges, as their teams lack deep security expertise, and their time is spent under constant alert triage. Add to this the rising complexity of managing multiple security solutions while uncovering hidden threats that can dwell on networks for years undetected, and it’s no wonder ransomware gangs are increasingly turning to LOTL techniques.
IT teams facing the threat of LOTL attacks need powerful technological and human interventions to stay ahead of today’s nimble RaaS adversaries.
With ThreatDown Core, Advanced, Elite, and Ultimate Bundles, security professionals receive industry-leading endpoint security that offers protection across the entire attack cycle. And with ThreatDown Bundles that include Managed Detection and Response services (Elite, Ultimate), teams get access to the most vital component of modern security defense: human expertise.
ThreatDown Elite and Ultimate Bundles provide teams with 24-hour, 365-day security monitoring and triage from, a dedicated team of security experts provides who supply IT with incident analysis, active remediation or remediation guidance, and threat hunting and reporting that helps teams prioritize security incidents.
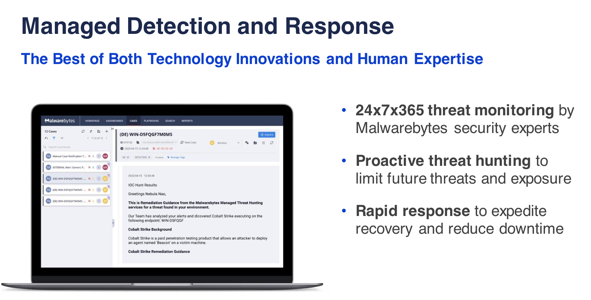
The Managed Detection and Response (MDR) analysts that support ThreatDown are experienced in detecting the malicious use of legitimate tools and blocking such attacks. They identify unusual behavioral patterns, connections to malicious IP addresses and domains, and unauthorized use of applications in LOTL attacks conducted by RaaS gangs, and relay important alerts to an organization’s IT members.
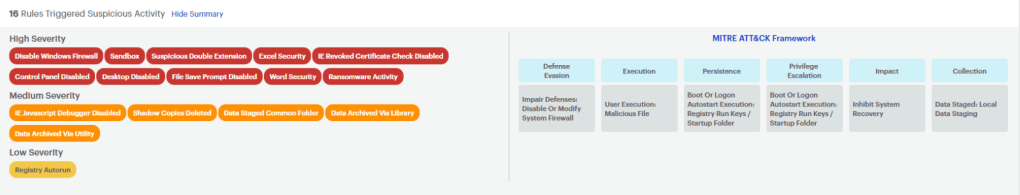
ThreatDown MDR observes the behaviors of processes, registries, files, systems, and network activities on the endpoint using a heuristic algorithm looking for deviations. Here you can see 16 detection rules triggered by suspicious activity and their mapping to MITRE ATT&CK framework.
Notifications sent by the ThreatDown MDR team are contextual and thorough, enabling security staff of all skill levels to clearly understand the status of an incident and the recommended response across threatened endpoints. The MDR service is supported by back-end artificial intelligence and machine learning, a proprietary analytics engine, and a cloud-based platform with integrated threat intelligence sources. Importantly, intelligence is delivered to security teams from analysts through a single pane of glass, standard in all ThreatDown Bundles.
To learn more about ThreatDown Bundles, check out our webpage.
How to protect against LOTL attacks
By combining cutting-edge technology and cybersecurity expertise, IT and security teams can uncover covert LOTL techniques before they blossom into full-blown ransomware attacks. The following tips from Malwarebytes’ ThreatDown MDR analysts underscore the multi-disciplinary approach necessary to detect and mitigate LOTL attacks before they cause irreparable damage.
- Regularly monitor network traffic and logs
- Regularly analyze your network traffic for any unusual patterns or connections to known malicious IP addresses or domains associated with the use of tools like Chisel, Qakbot, or Cobalt Strike.
- Enable logging on critical systems (firewalls, servers, and endpoint devices), and regularly review logs for unusual activities or signs of compromise.
- Stay informed on the latest threat intelligence
- Leverage threat intelligence feeds, including the Malwarebytes Labs research blog, to stay informed about new attack techniques, indicators of compromise (IOCs), and other relevant threat data.
- Use this data to fine tune your security monitoring, detection, and response capabilities to identify and mitigate LOTL attacks.
- Leverage behavioral analysis and anomaly detection
- Implement advanced monitoring tools that focus on detecting unusual user or system behavior rather than relying solely on known signatures or patterns.
- Use machine learning and artificial intelligence to identify deviations from normal behavior, which might indicate an ongoing LOTL attack.
- Restrict the abuse of legitimate tools
- Focus on setting stronger security controls, policies, and oversight of legitimate tools and system features often exploited in LOTL attacks.
- Implement least-privilege access controls, limiting access to certain data and toolsets only to users who require them for job functionality. Monitor their usage and apply specific security policies to restrict potentially harmful actions.
- Regularly scan and patch vulnerabilities
- Regularly scan for known vulnerabilities and patch to prevent software and operating systems from being exploited in LOTL attacks.
- Push out regular, automated updates of business applications, ensuring users are always on the latest version.
By continuously analyzing network and system data, identifying potential vulnerabilities, monitoring anomalous user activities, and anticipating which legitimate tools might be abused, IT teams can begin to get the upper hand against RaaS gangs that favor LOTL attacks. Vigilance, knowledge, and support of skilled security team members and solutions is key in rooting out the insidious from the benign.
Additional resources
While less established than the known exploited vulnerabilities (KEV) catalog, IT teams and security analysts can reference a growing list of resources to better understand how tools and processes are leveraged by cybercriminals in LOTL attacks. Here are a few of the top repositories:
Living Off The Land Binaries, Scripts and Libraries (LOLBAS) is a compilation of Windows executables that can be used to bypass security controls, execute code, and otherwise carry out LOTL attacks. This resource helps security analysts understand how the listed binaries function and can be abused, with techniques mapped to MITRE ATT&CK® framework.
GTFOBins is a similar compilation of curated Unix binaries that can be used to get around local security restrictions in misconfigured systems. This collection provides insights into legitimate binary functions used for malicious activities, such as privilege escalation, file transfer, or facilitation of other post-exploitation tasks.
LOLDrivers catalogs legitimate Windows drivers that can be exploited by attackers to bypass security measures. This resource includes a list of drivers, their capabilities, and potential risks to aid in threat detection and mitigation.
Finally, the LOLBAS project page for WMI command-line provides information on how the WMIC utility, a command-line interface for WMI, can be used in LOTL attacks.



