
Credential Dumping: How ransomware gangs steal login data and how to detect it
Get the ins and outs of Credential Dumping.
Credential Dumping on your network is one of the biggest tell-tale signs of ongoing ransomware gang activity.
In the MITRE ATT&CK Framework, Credential Dumping is a technique under the Credential Access tactic, when attackers seek legitimate credentials to gain access to other parts of a network.
More specifically, Credential Dumping is when ransomware attackers extract (i.e. ‘dump’) authentication credentials from the operating system and into locations of their own choosing, usually plaintext files (.txt).
Let’s explain how Credential Dumping works, what tools ransomware gangs use to do it, and how organizations can detect ransomware gangs using Credential Dumping in their attacks.
How Credential Dumping works
Cryptographic keys, plaintext passwords, password hashes, Kerberos tickets, security tokens, etc; there is no shortage of sensitive credentials that our computers store on a daily basis.
Unlike the login information we use for browsers, however, which is kept in encrypted browser-specific databases, operating system credentials are stored in memory and critical system files.
What controls access to this in-memory information, you ask? For Windows, it’s the Local Security Authority Subsystem Service (LSASS). On macOS, it’s the Keychain, and for Linux, it’s typically the /etc/shadow file and various security modules. The point is that each operating system has its own mechanisms to manage and protect sensitive credentials, and that gaining access to these tools essentially grants you free reign over a system.
Whenever ransomware gangs extract credentials from your system, it’s usually from these native in-memory applications and storage mechanisms. However, credential dumping can extend beyond operating system memory as well. Tools like LaZagne, for example, can also pull passwords from browser credential stores, email credentials, WiFi network passwords, and server applications.
Storage mechanisms like Windows’ LSASS or Mac’s Keychain must be pretty secure, right? After all, these systems are designed with various protocols to protect all that sensitive information. So how are attackers able to get in and steal credentials from them?
Bypassing memory storage security all comes down to using advanced tools like Mimikatz. Let’s dive into a few examples in the next section.
Mimikatz: The most popular Credential Dumping tool
Mimikatz is the most popular tool used by ransomware gangs for extracting plaintext passwords, password hashes, and PINs from memory, specifically within the LSASS process. The popularity of Mimikatz is likely because most enterprises run Windows, and Mimikatz was specifically designed for Windows systems.
A little bit about how it works: Mimikatz uses functions like OpenProcess and ReadProcessMemory to access and read the LSASS process memory directly, allowing it to bypass many security mechanisms.
Through modules like sekurlsa::logonpasswords, for example, Mimikatz can easily retrieve sensitive credentials of logged-in users. Below is a real example taken from the ThreatDown Incident Response team of a ransomware gang using Mimikatz in an attack:
"command_line": "cmd.exe /Q /c C:\\ProgramData\\mmk.exe \"privilege::debug\" \"sekurlsa::logonPasswords full\" \"exit\" 1> \\Windows\\Temp\\htAZHM 2>&1", mmk.exe hash 61c0810a23580cf492a6ba4f7654566108331e7a4134c968c2d6a05261b2d8a1In this example, the attackers executed Mimikatz (mmk.exe) to run with debug privileges and retrieve all logon passwords from LSASS memory, redirecting the output to a temporary file.
While Mimikatz is certainly the most popular tool ransomware attackers use for Credential Dumping, it is not the only tool. Below is a chart of five of the most active ransomware gangs and what tools they use for credential dumping.
| Gang | Tool | Function | MITRE ATT&CK Technique |
|---|---|---|---|
| LockBit | ExtPassword, LostMyPassword, ProcDump, Mimikatz | Recovers passwords from Windows systems, monitors applications for CPU spikes and generates crash dumps, extracts plaintext passwords, hashes, and Kerberos tickets from memory. | T1003.001 |
| Akira | Mimikatz, LaZagne | Extracts plaintext passwords, hashes, and Kerberos tickets from memory; retrieves passwords stored in various applications. | T1003 |
| PLAY | Mimikatz | Extracts plaintext passwords, hashes, and Kerberos tickets from memory. | T1003 |
| 8BASE | Mimikatz, LaZagne, WebBrowserPassView, VNCPassView, PasswordFox, ProcDump | Retrieves passwords and credentials from victim machines. | T1003 |
| Black Basta | Mimikatz | Extracts plaintext passwords, hashes, and Kerberos tickets from memory. | T1003 |
How to detect ransomware gangs Credential Dumping
In order to detect potential ongoing Credential Dumping by ransomware gangs, IT teams should be on constant watch for suspicious command-line invocations that involve known credential dumping tools and techniques. Some MITRE techniques to be aware of include:
- LSASS Memory Dumping
- Description: Attackers dump the memory of the LSASS process to extract password hashes and plaintext passwords.
- MITRE ATT&CK Technique: T1003.001
- Cached Domain Credentials
- Description: Extracting cached domain credentials stored on the local machine.
- MITRE ATT&CK Technique: T1003.005
- /etc/passwd and /etc/shadow
- Description: Retrieving user account information and hashed passwords from the /etc/passwd and /etc/shadow files on Unix-like systems
- MITRE ATT&CK Technique: T1003.008
An Endpoint Detection and Response (EDR) solution that automatically correlates these techniques to the MITRE ATT&CK framework—such as ThreatDown EDR—provides a structured approach to detecting and responding to Credential Dumping threats.
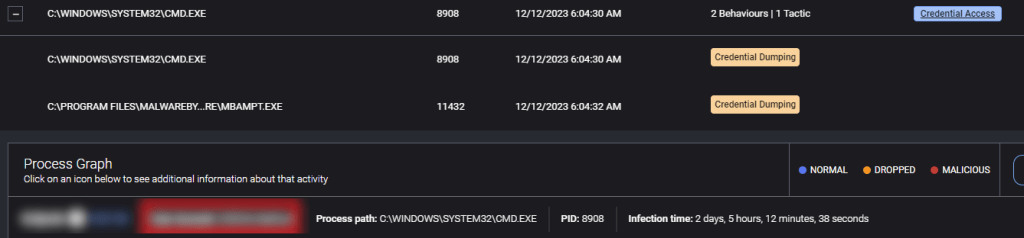
Spotting Credential Dumping with Managed Detection and Response (MDR)
Staying on top of not just Credential Dumping, but any TTPs ransomware gangs rely on in their attacks, requires 24×7 monitoring by people with the skills to spot the early signs of a ransomware attack and perform proactive threat hunting and incident response. As we wrote in our post why ransomware attacks are getting quicker, time is now of the essence when it comes to nipping attackers in the bud.
Managed Detection and Response (MDR) is a cost-efficient way to reap the benefits of a 24×7 Security Operations Center (SOC) for organizations who lack the budget to set one up themselves.
With MDR, organizations have access to a round-the-clock team of experts to threat hunt, stay on top of the latest adversary tools, techniques, and procedures (TTPs), and quickly remediate threats as necessary.
Purpose-built for organizations with small (to non-existent) security teams that lack the resources to address emerging threats like Akira ransomware, the ThreatDown Ultimate Bundle includes award-winning technologies and 24x7x365 expert-managed monitoring and response from the ThreatDown MDR team.
Cybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of MalwareCybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of Malware


