
Ransomware group steps up, issues statement over MGM Resorts compromise
Christopher Boyd
Christopher Boyd
The recent attack on MGM Resorts generated lots of speculation with regard to what the cause was. Some folks claimed the culprit was ransomware. Well, confirmation is now forthcoming as an affiliate of the BlackCat/ALPHV ransomware group is said to be the one responsible for the attack and subsequent outage.
The statement is quite long, takes a few digs at MGM Resorts, and seeks to correct what the group feels to be inaccurate statements made by security vendors and others with regard to the attack.
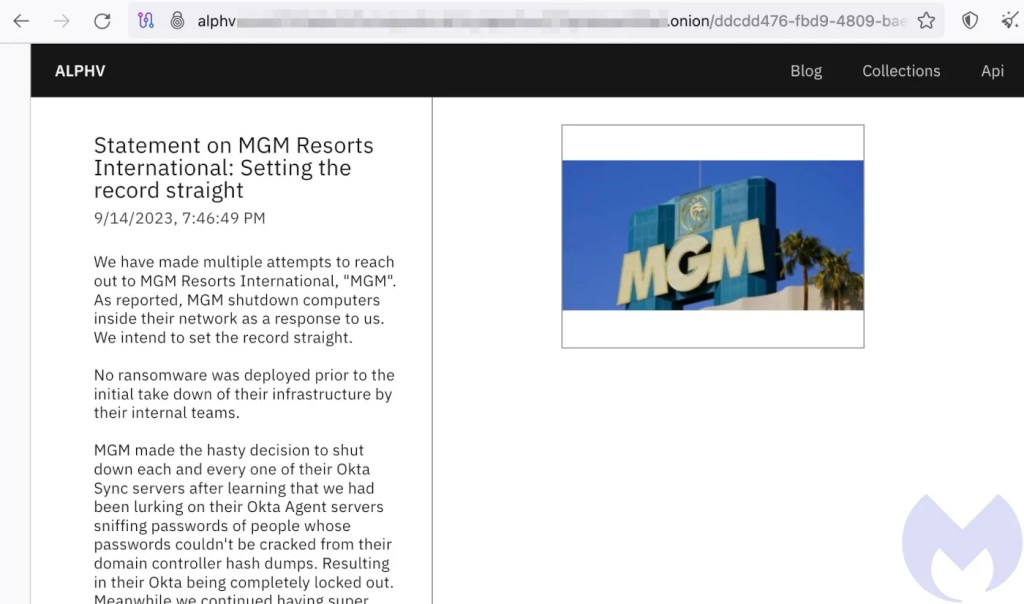
It begins:
Statement on MGM Resorts International: Setting the record straight
9/14/2023, 7:46:49 PM
We have made multiple attempts to reach out to MGM Resorts International, “MGM”. As reported, MGM shutdown computers inside their network as a response to us. We intend to set the record straight.
No ransomware was deployed prior to the initial take down of their infrastructure by their internal teams.
MGM made the hasty decision to shut down each and every one of their Okta Sync servers after learning that we had been lurking on their Okta Agent servers sniffing passwords of people whose passwords couldn’t be cracked from their domain controller hash dumps. Resulting in their Okta being completely locked out. Meanwhile we continued having super administrator privileges to their Okta, along with Global Administrator privileges to their Azure tenant. They made an attempt to evict us after discovering that we had access to their Okta environment, but things did not go according to plan.
On Sunday night, MGM implemented conditional restrictions that barred all access to their Okta (MGMResorts.okta.com) environment due to inadequate administrative capabilities and weak incident response playbooks. Their network has been infiltrated since Friday. Due to their network engineers’ lack of understanding of how the network functions, network access was problematic on Saturday. They then made the decision to “take offline” seemingly important components of their infrastructure on Sunday.
As with so many break ins, this begins with a social engineering attack. There have been claims on social media that this was done by finding an employee on LinkedIn, and calling the helpdesk for what would presumably be a password reset attempt. However, the statement is quite light with regard to the specifics:
We are unable to reveal if PII information has been exfiltrated at this time. If we are unable to reach an agreement with MGM and we are able to establish that there is PII information contained in the exfiltrated data, we will take the first steps of notifying Troy Hunt from HaveIBeenPwned.com. He is free to disclose it in a responsible manner if he so chooses.
The rumors about teenagers from the US and UK breaking into this organization are still just that—rumors. We are waiting for these ostensibly respected cybersecurity firms who continue to make this claim to start providing solid evidence to support it. Starting to the actors’ identities as they are so well-versed in them.
There are also claims that the attackers still have access to the MGM Resorts network, despite the shutdown and clean up operation taking place:
The ALPHV ransomware group has not before privately or publicly claimed responsibility for an attack before this point. Rumors were leaked from MGM Resorts International by unhappy employees or outside cybersecurity experts prior to this disclosure. Based on unverified disclosures, news outlets made the decision to falsely claim that we had claimed responsibility for the attack before we had.
We still continue to have access to some of MGM’s infrastructure. If a deal is not reached, we shall carry out additional attacks. We continue to wait for MGM to grow a pair and reach out as they have clearly demonstrated that they know where to contact us.
We’ve written about BlackCat/ALPHV many times on the Malwarebytes Labs Blog. Their range is large, with high-publicity takedowns ranging from major cosmetics firms and leaked hospital photographs to point of sale outages and video game publishers.
In this specific case, Bleeping Computer describes the alleged group behind the chaos as “Scattered Spider”. This particular group has a fondness for social engineering tactics used to slip into corporate networks. They don’t just use password reset impersonation, but also phishing, SIM swapping (hijacking someone’s mobile number), and even MFA fatigue where your mission is to annoy an employee with so many alerts that they eventually say “yes”.
An interesting development, then. Even so, with so much speculation and claim/counterclaim flying around it’s probably best to keep an open mind on these latest developments. The truth will out one way or another, but the biggest concern has to remain potential data theft and leakage of those making use of MGM Resort facilities.
Cybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of MalwareCybercrime Has Gone Machine-Scale
AI is automating malware faster than security can adapt.
Get the facts Read the 2026 State of Malware


